
Private Investigator Challenge
Description: You’re hired by UVW88 Inc. to investigate Ron, a purchasing manager suspected of leaking product launch details. After physical surveillance shows nothing, you capture and analyze his home WiFi traffic for clues.
Level: Easy
Category: Wifi Security Forensics Basics
Link: https://my.ine.com/challenge/private-investigator
Tactics: Reconnaissance, Credential Access, Impact / Denia, Initial Access
Tools: Wireshark, Aircrack-ng
Scenario
You are a licensed Private Investigator (PI). UVW88 Inc is one of your old customers. They import electronics from abroad and sell the re-branded product. They asked you to look into Ron, one of their purchasing managers. They think that he is tipping off their competitors about the soon to be launched products in advance, giving the competition an edge over them. They checked his company issued phones and corporate email account but didn’t find anything suspicious. Hence, they brought in the big guns ( yes you :-). You follow him for 2 days but he isn’t meeting anyone. So, the next night you decide to wait outside his house in your car. While sitting outside, eating a burger, you notice his home WiFi network and you realize that he may be using this to communicate with the 3rd party. So, you capture his WiFi traffic and return to your office to analyze it.
- The relevant details
- The details of Ron's home WiFi network are given below:
- SSID:
Ron_Home - BSSID:
30:b5:c2:11:de:2a - Security:
WPA2-PSK - Phone MAC:
5c:51:88:31:a0:3b - Laptop MAC:
e8:de:27:16:70:c9
Questions
Q1. How he is communicating with the 3rd party?
Solution: He is sending SMS (and tried to call) using VoIP service using his home WiFi.
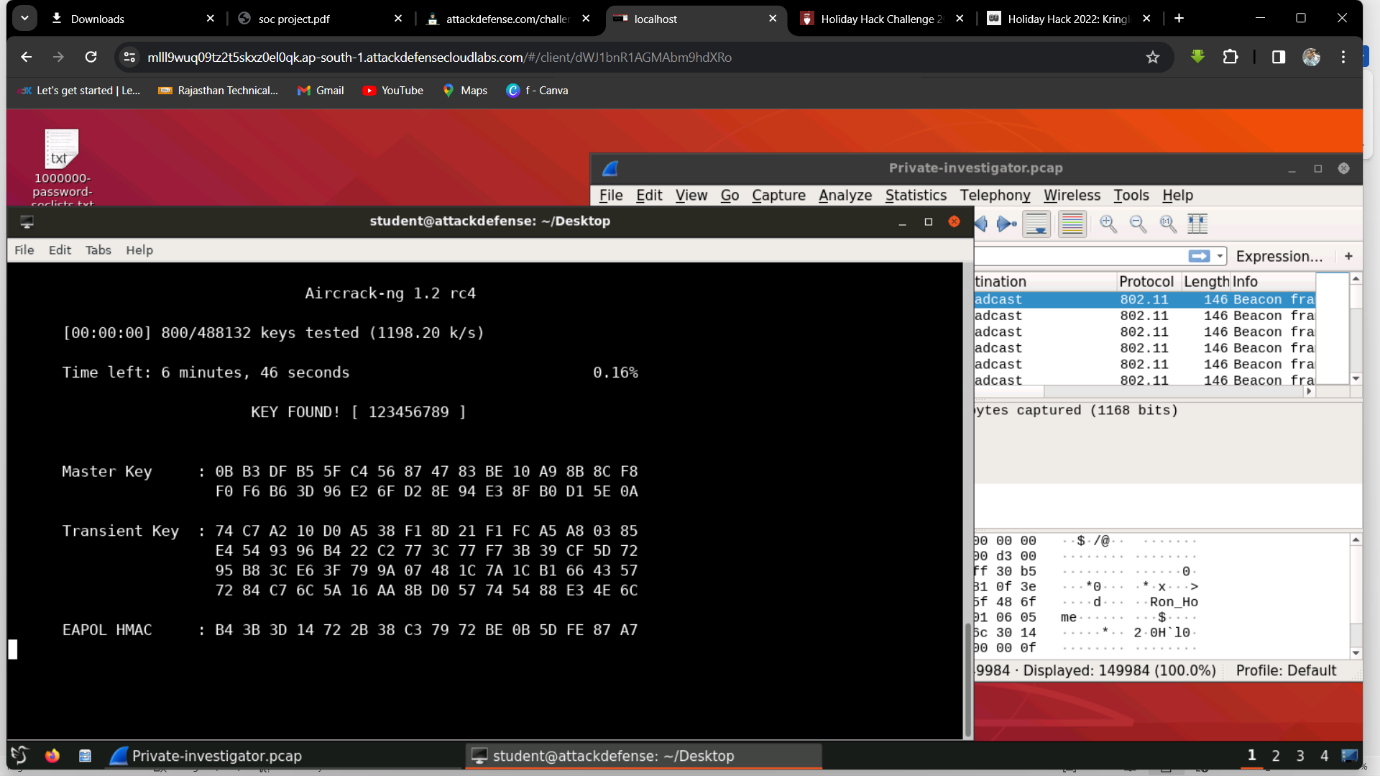
Step 1: Find the Wi-Fi password using aircrack-ng, a wordlist, and the Private-investigator.pcap file. The password is 123456789.
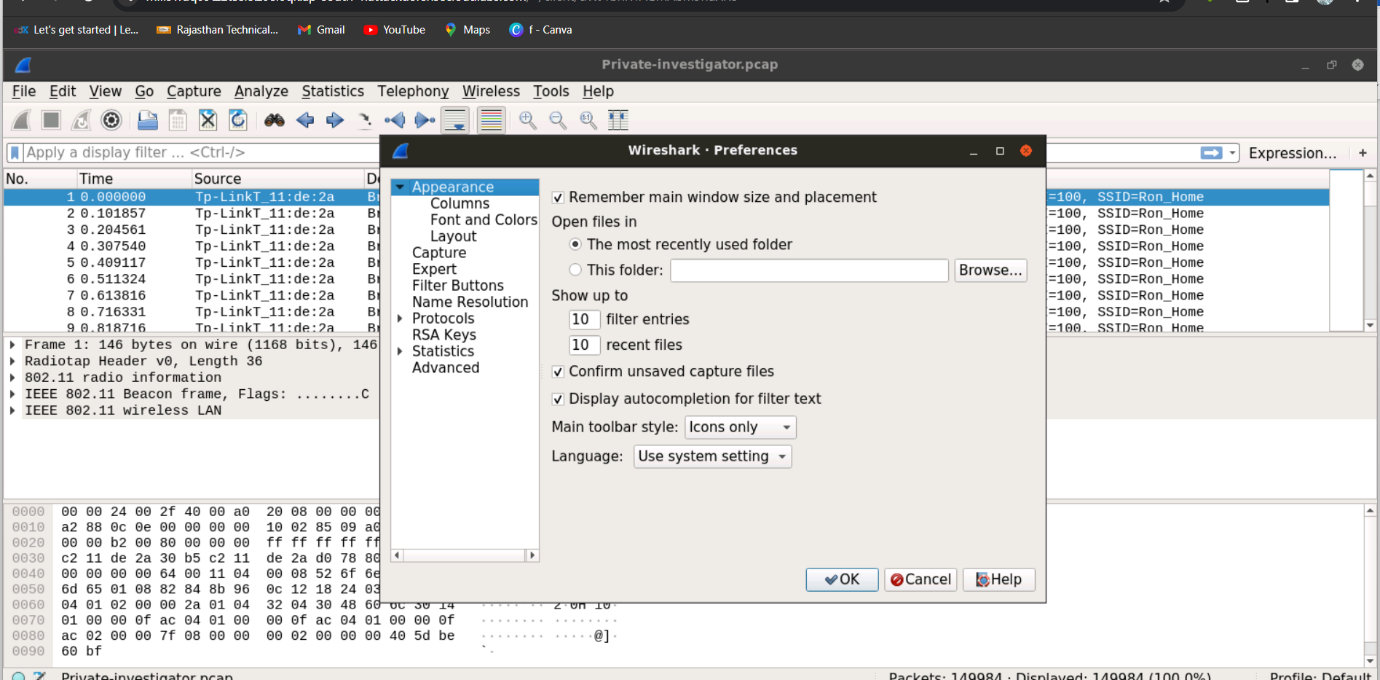
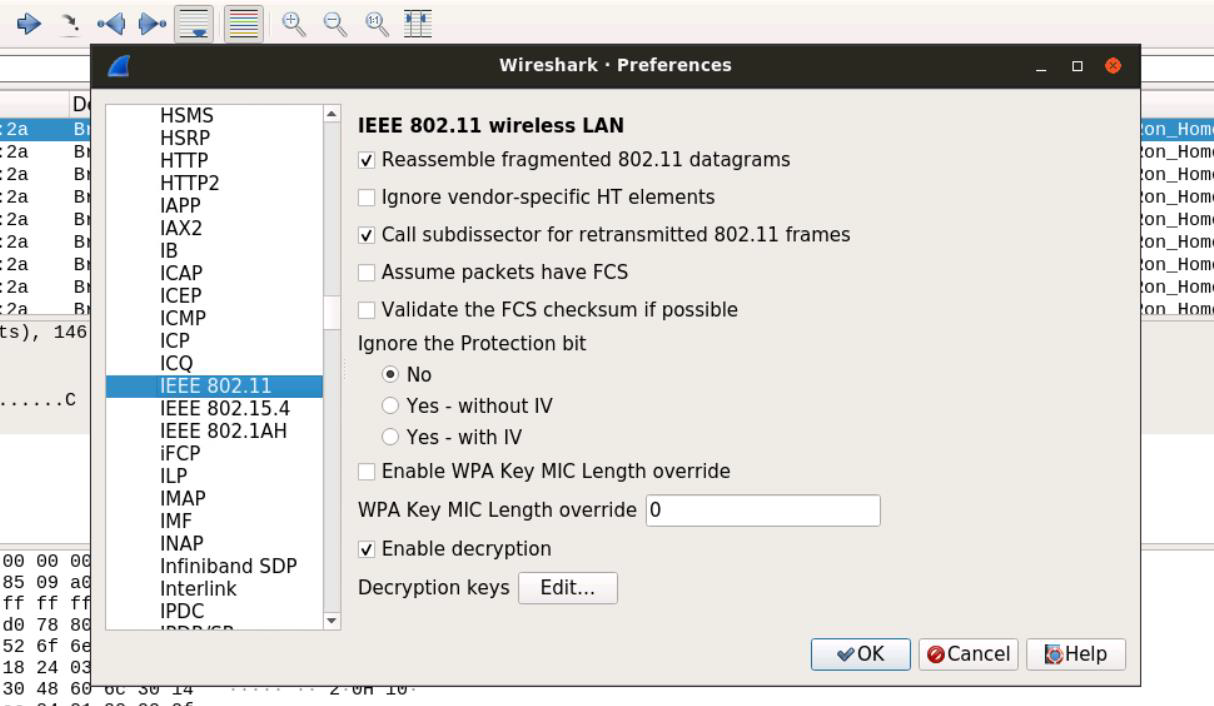
Step 2: In Wireshark, set the decryption key to wpa-pwd 123456789:Ron_Home under Edit -> Preferences -> Protocols -> IEEE 802.11.
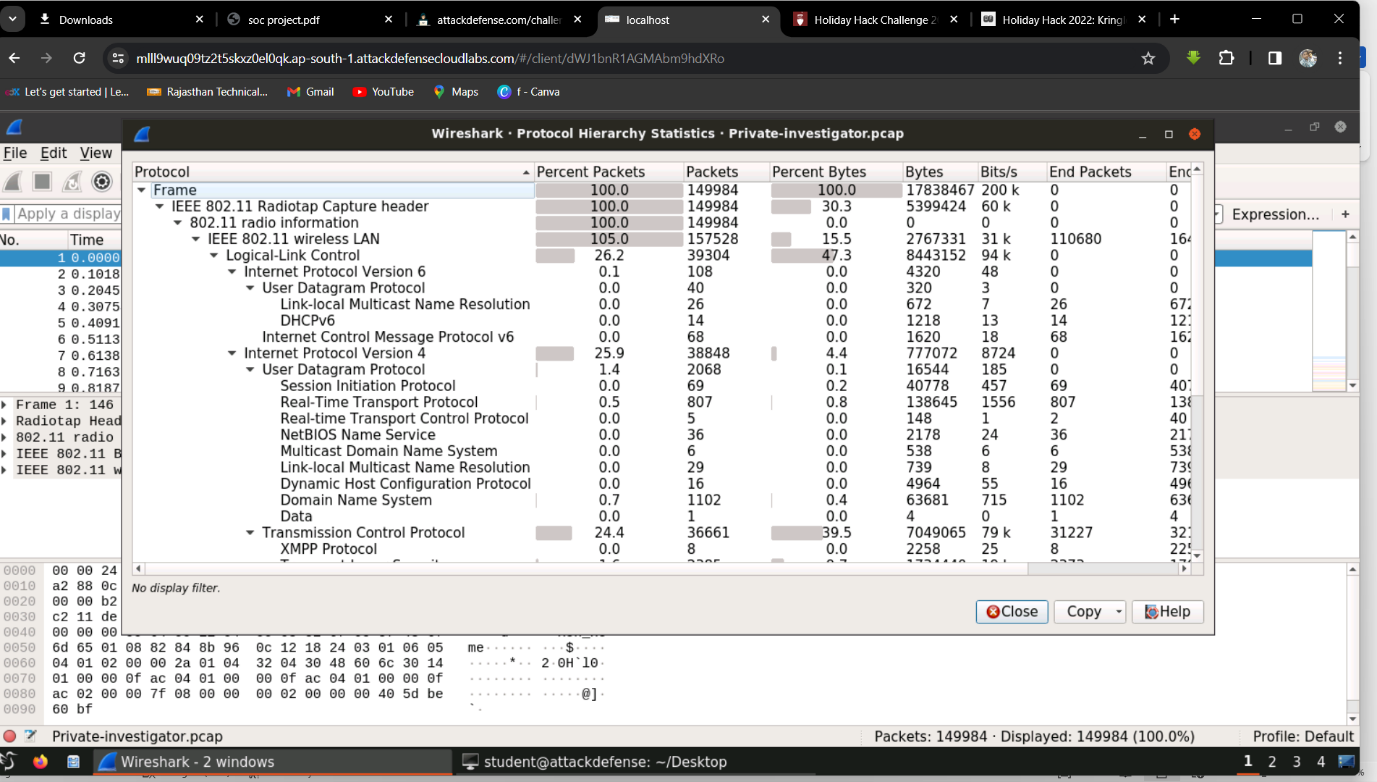
Step 3: Analyze the protocol hierarchy and find SIP and RTP protocols, indicating VoIP usage.
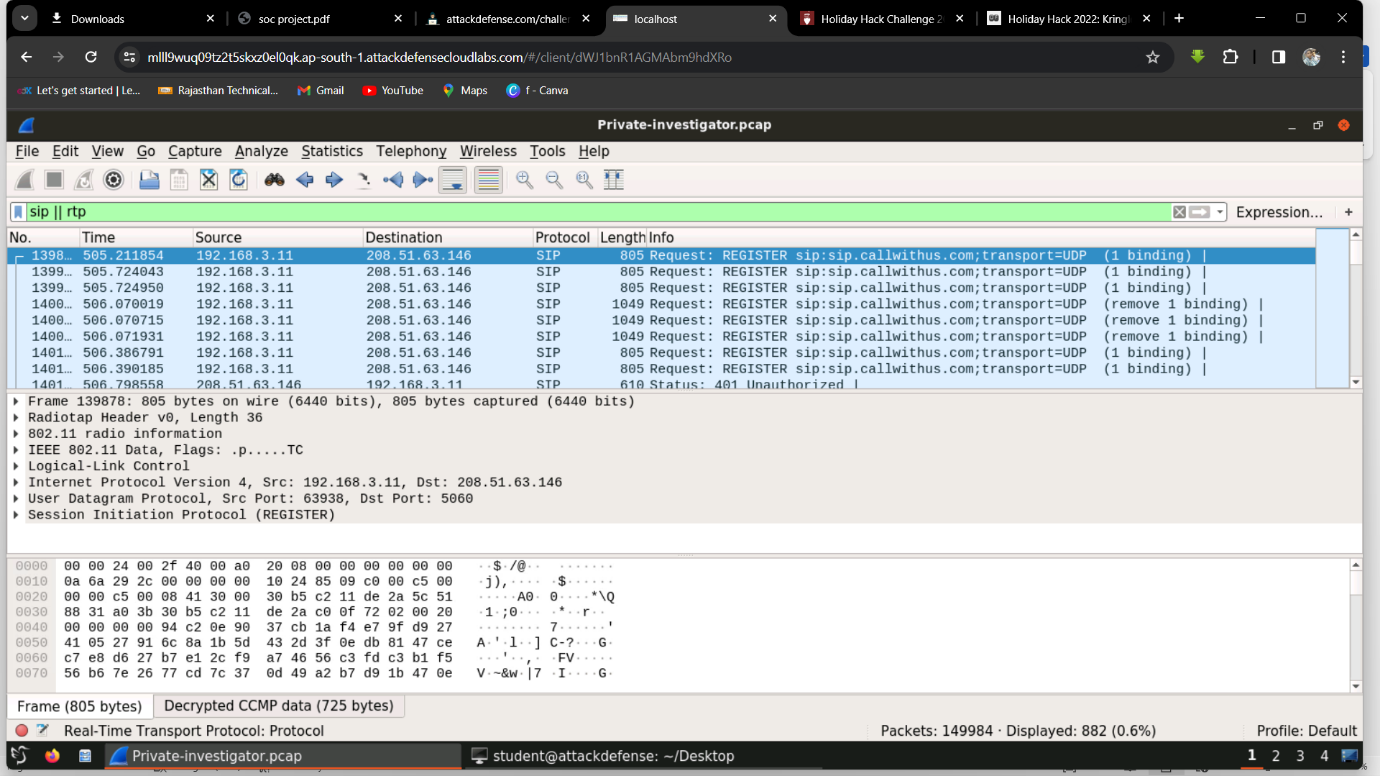
Q2. What content did you recover from the communication intercepted (if any)?
Solution: The message "Hey..I have more information regarding new product....I will call you shortly.".
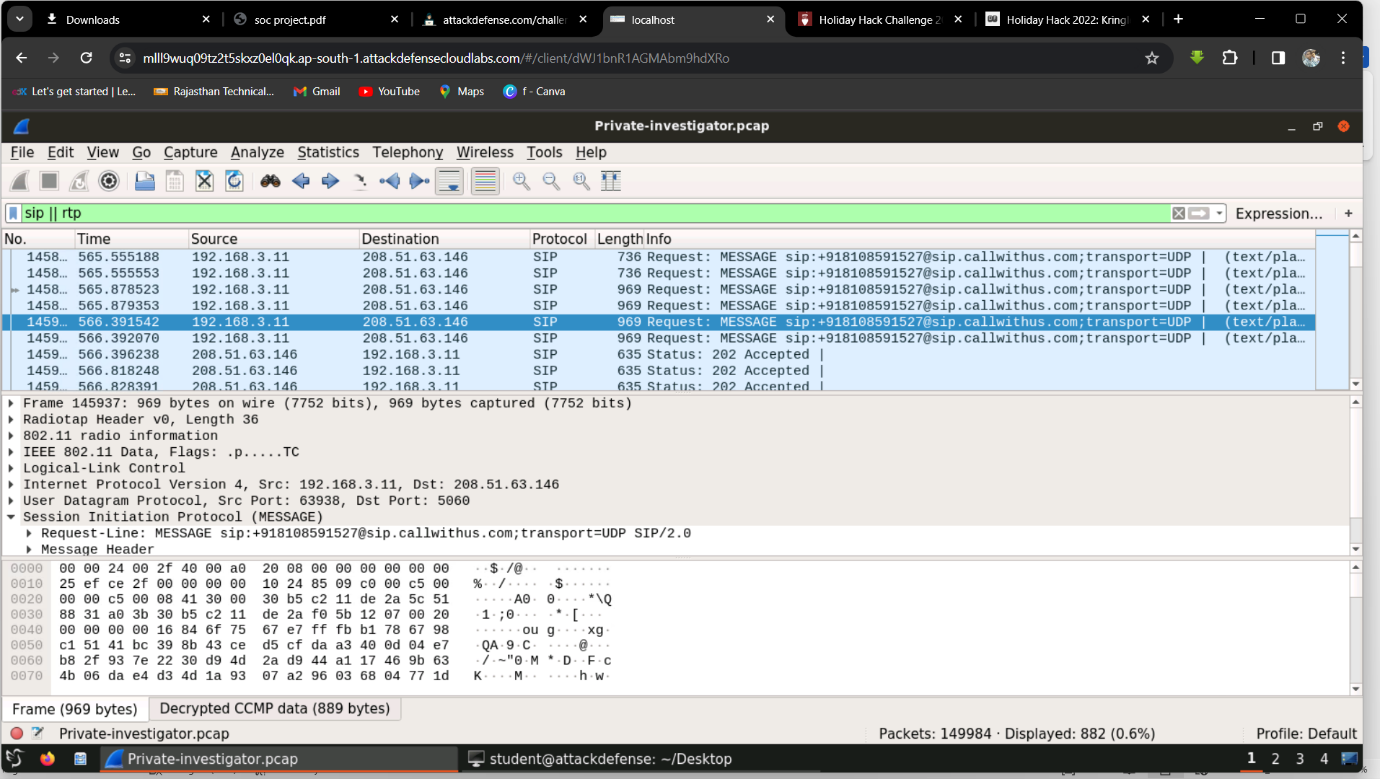
Step 1: Filter for SIP || RTP and analyze a packet.
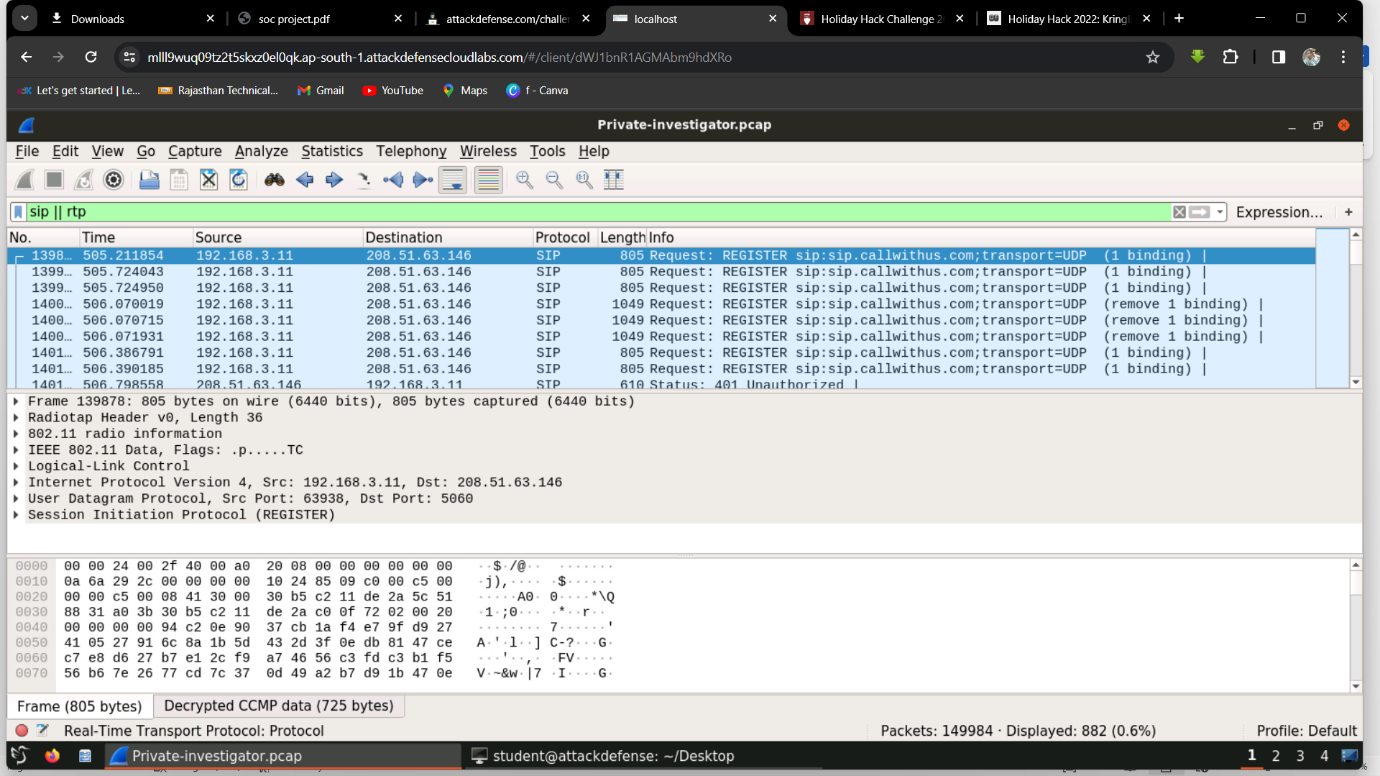
Step 2: Go to packet 1459 and analyze the details.
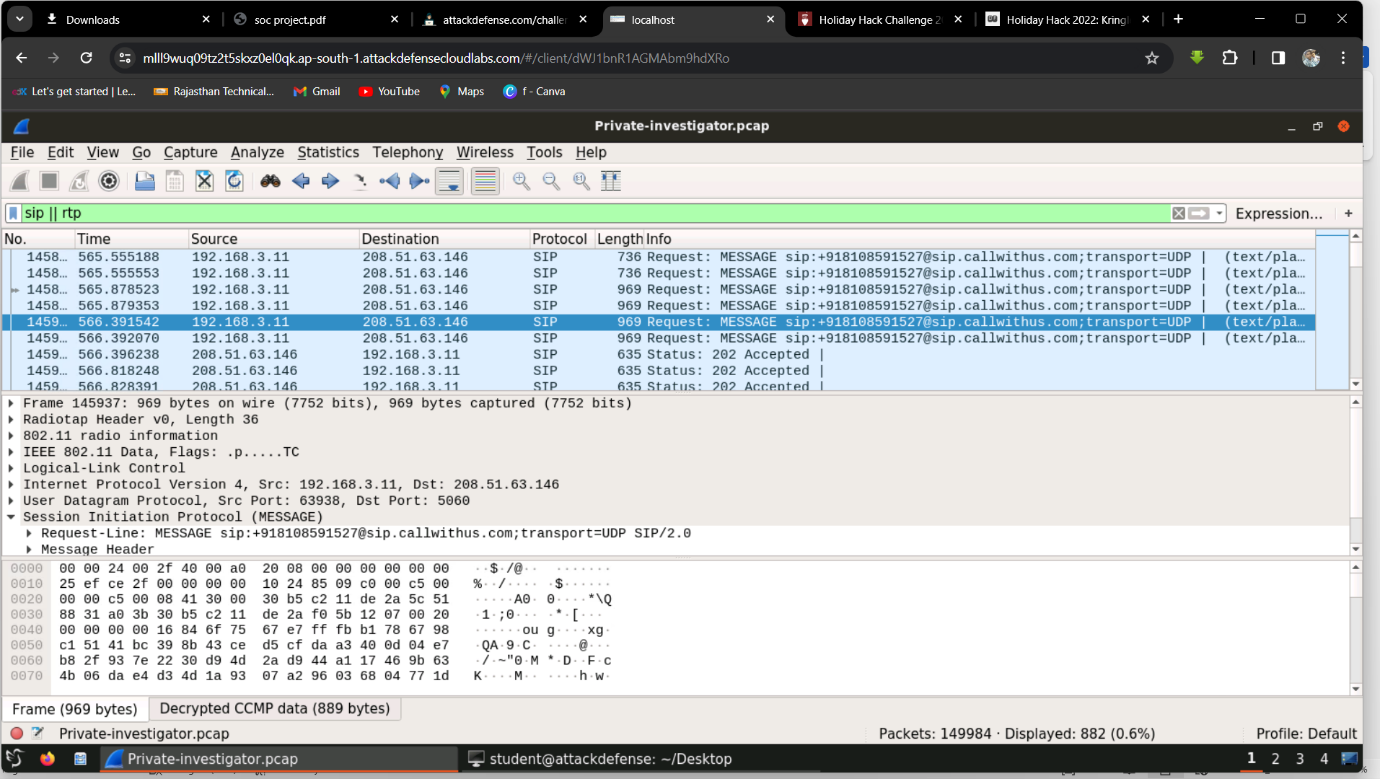
Step 3: Find the message body under Session Initiation Protocol -> Message Body -> Line-based text data.

Q3. Any contact information of the 3rd party (if any)?
Solution: The cell number is +91-8108591527.
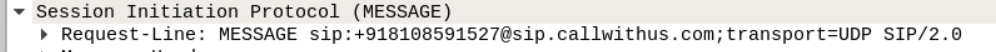
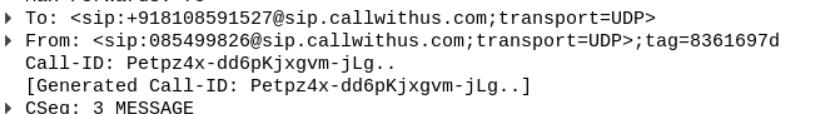
Step 1: Analyze packet 1459 for details.
Step 2: The phone number +918108591527 is found in the Request-Line under Session Initiation Protocol.
Q4. Anything interesting that you observed during the analysis which could shed light on his other motives?
Solution: He is researching a lot of spy gadgets.
Step 1: Go to Statistics -> HTTP in Wireshark.
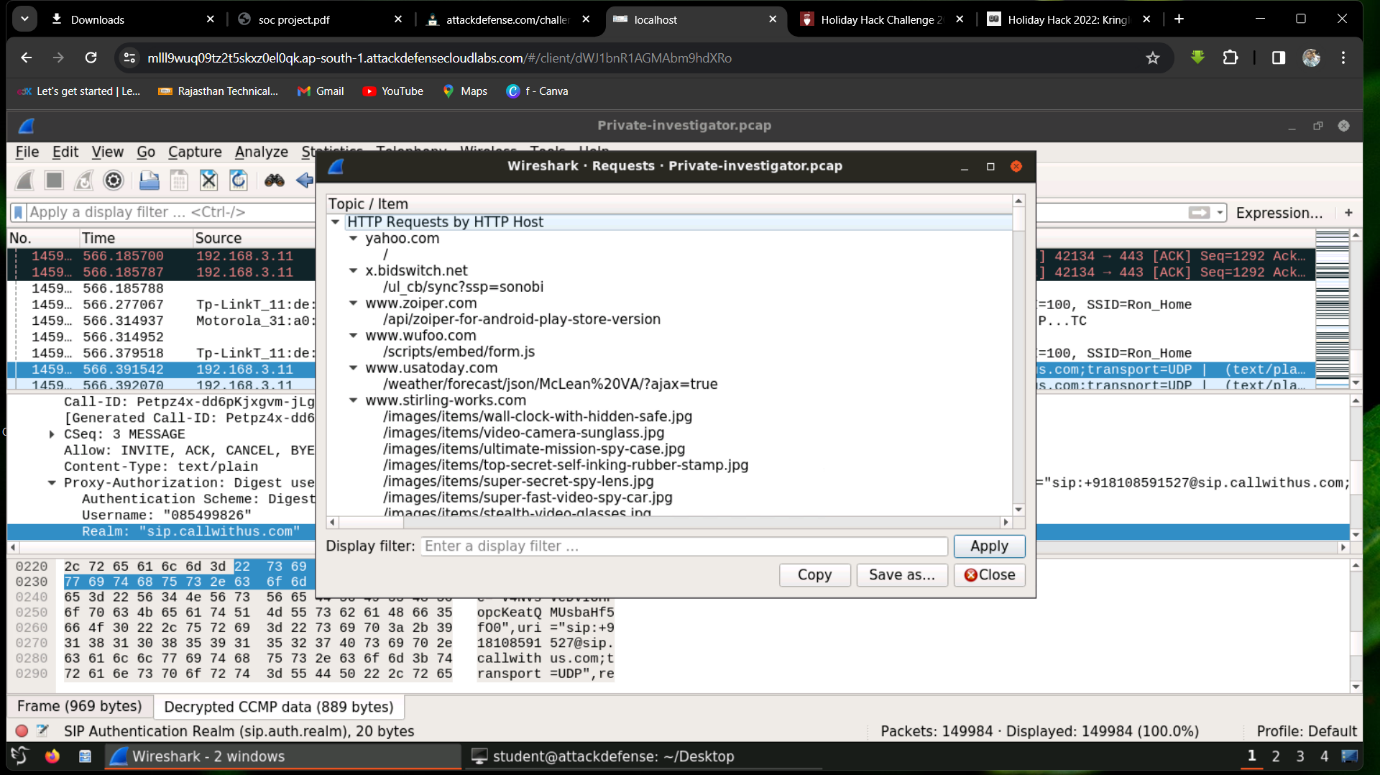
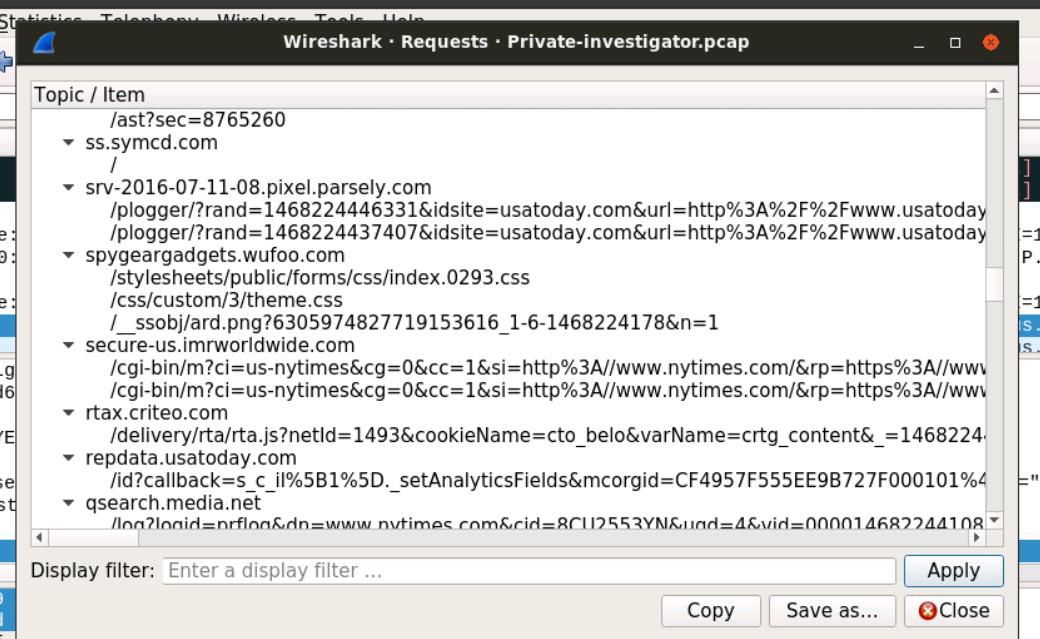
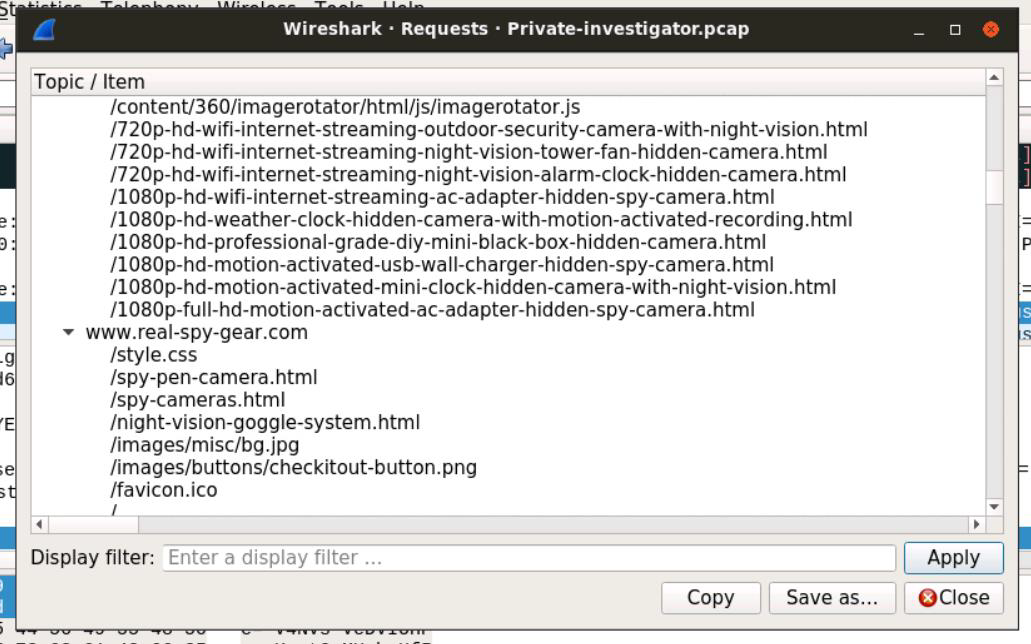
Step 2: Analyze the links and topics accessed by the attacker. Many of the links point to pages for spy cameras and night vision goggles.
Conclusion
Based on the analysis of the captured Wi-Fi traffic, it is confirmed that Ron, the purchasing manager, is communicating with a third party using his home network, and his activities suggest motives beyond simply leaking product information.
The investigation revealed that Ron used a VoIP service to send a text message and attempt a call to a third party. The recovered message, "Hey..I have more information regarding new product....I will call you shortly," directly implicates him in leaking confidential company information. The recipient of this message and the attempted call has been identified as +91-8108591527.
Beyond the product leak, the analysis of his web browsing history uncovered a suspicious pattern. Ron was actively researching and viewing content related to spy gadgets, including spy cameras and night vision goggles. This activity, combined with his unauthorized communication with a competitor, indicates a deeper level of misconduct. It suggests he may be considering further illicit activities or surveillance, potentially to gather more sensitive information or for personal gain.
In conclusion, Ron is not just a passive leak; he is an active participant in corporate espionage, using secure communication methods and actively researching tools to aid his illegal activities. This is a clear breach of trust and a significant threat to the company's intellectual property.