
Phishing Email Challenge
Description: Your email address has been leaked and you receive an email from Paypal in German. Try to analyze the suspicious email.
Level: Easy
Category: Email Analysis
Link: https://app.letsdefend.io/challenge/phishing-email
Tactics: Initial Access, Execution, Credential Access, Collection, Command and Control, Impact
Tools: VirusTotal, Curl, Thunder Bird, EmailAnalytics
Scenario
In this writeup we will be analyzing a email to determine whether it was a phishing attempt or not. We will only use a mail client(You can use any you like) and avail Threat intel platforms like virustotal and cisco talos intelligence
Questions
Q1. What is the return path of the email?
Solution: bounce@rjttznyzjjzydnillquh.designclub.uk.com.
Step 1: Open Paypal.eml file in Thundermail.
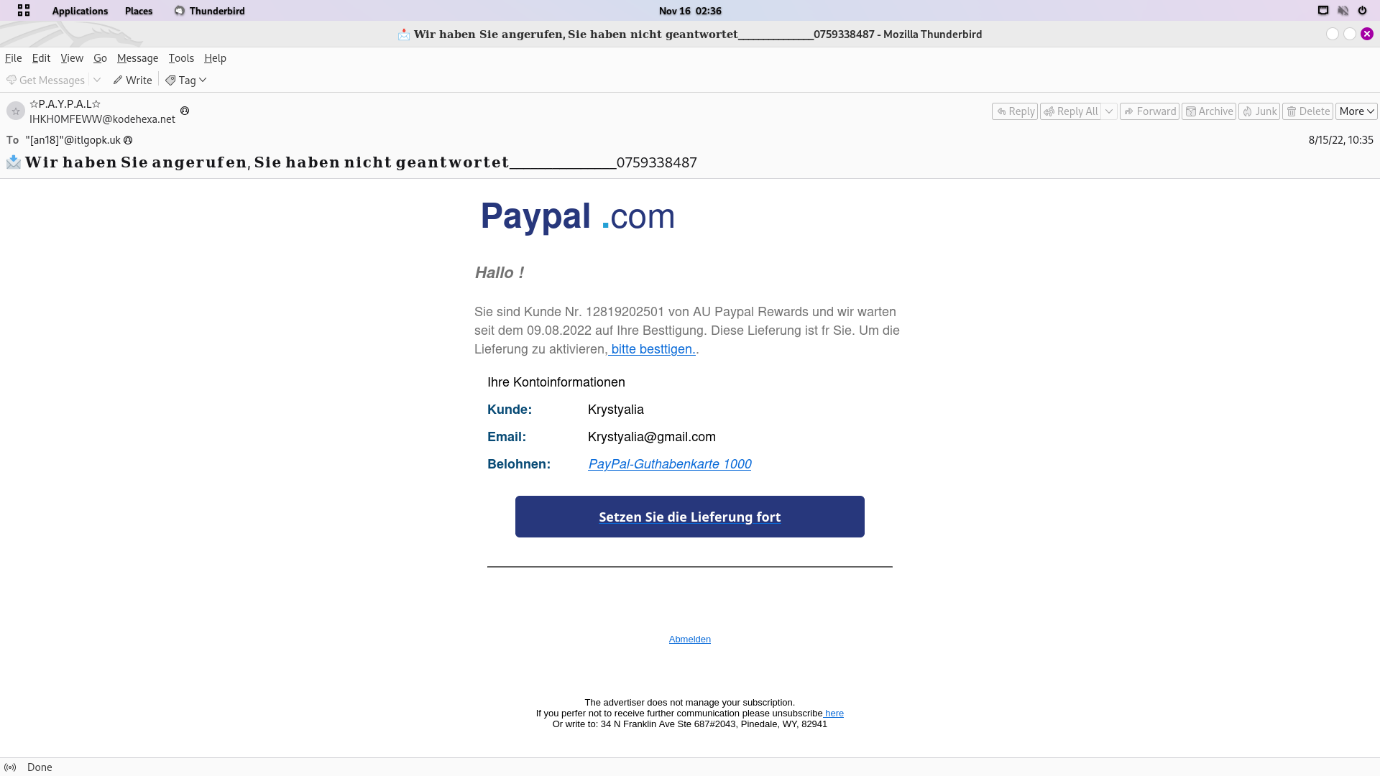
Step 2: Open and Analyse the Paypal.txt file then find the domain.
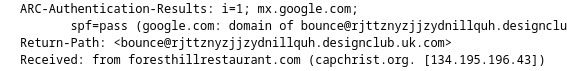
Q2. What is the domain name of the url in this mail?
Solution: storage.googleapis.com.
Step 1: Copy Blue Button link then paste in newly created file Paypal.txt.
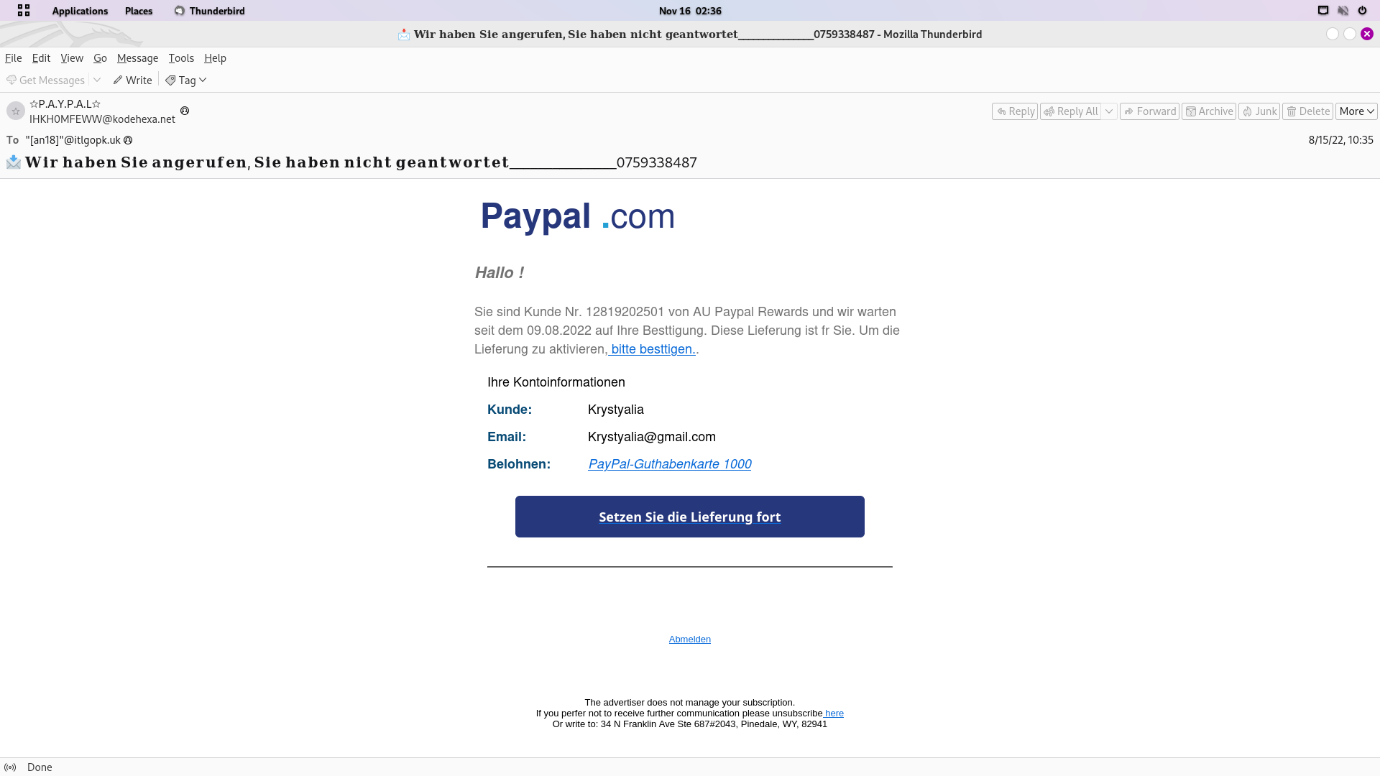
Step 2: Open and Analyse the Paypal.txt file then find the domain.

Q3. Is the domain mentioned in the previous question suspicious?
Solution: yes.
Step 1: Search domain storage.googleapis.com on Virustotal site then analyse the report.
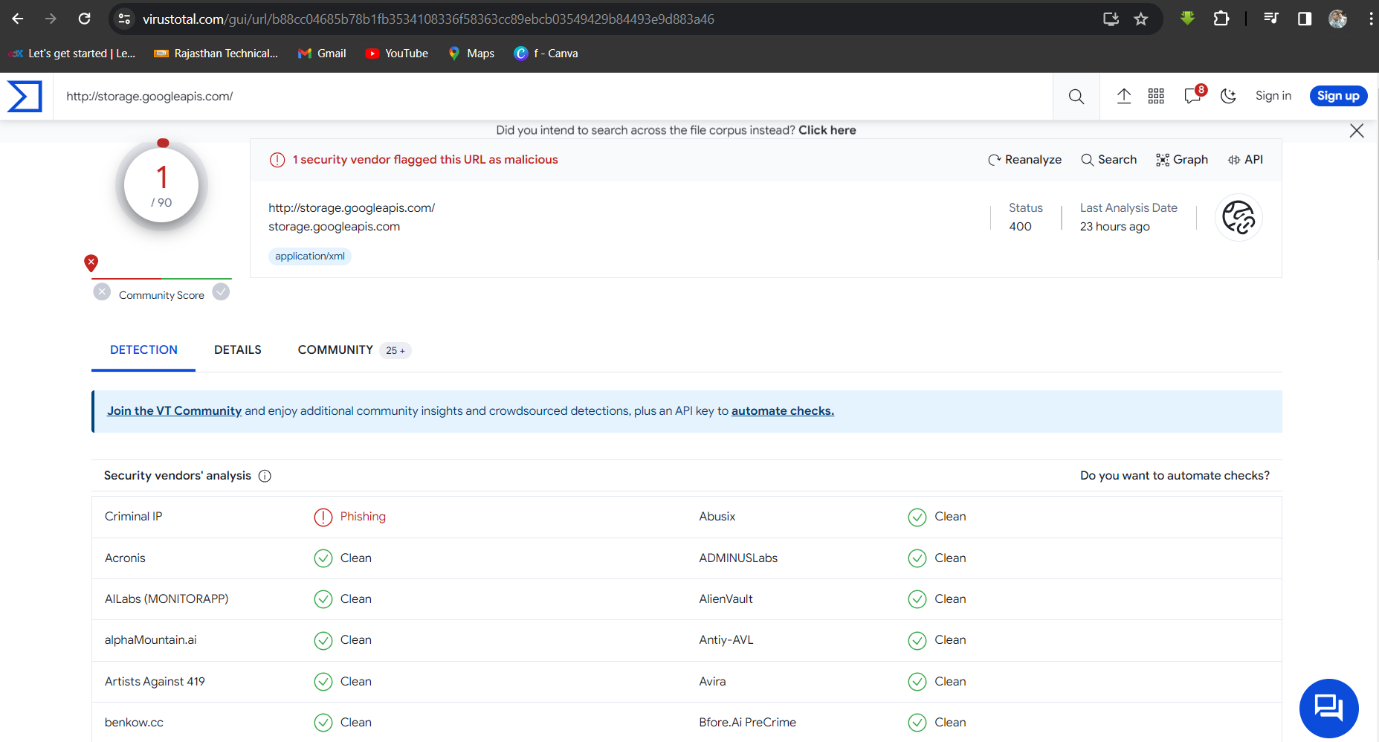
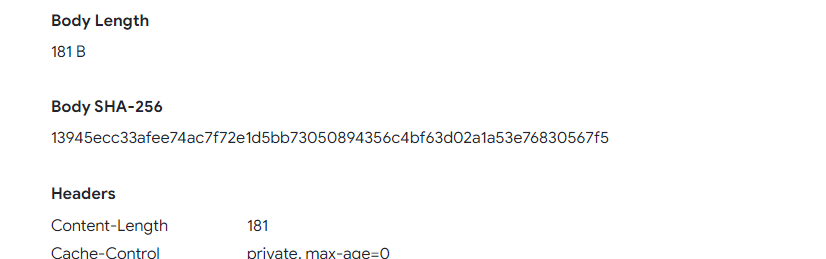
Q4. What is the body SHA-256 of the domain?
Solution: 13945ecc33afee74ac7f72e1d5bb73050894356c4bf63d02a1a53e76830567f5.
Step 1: Select Details -> Scroll down and analyse the report.
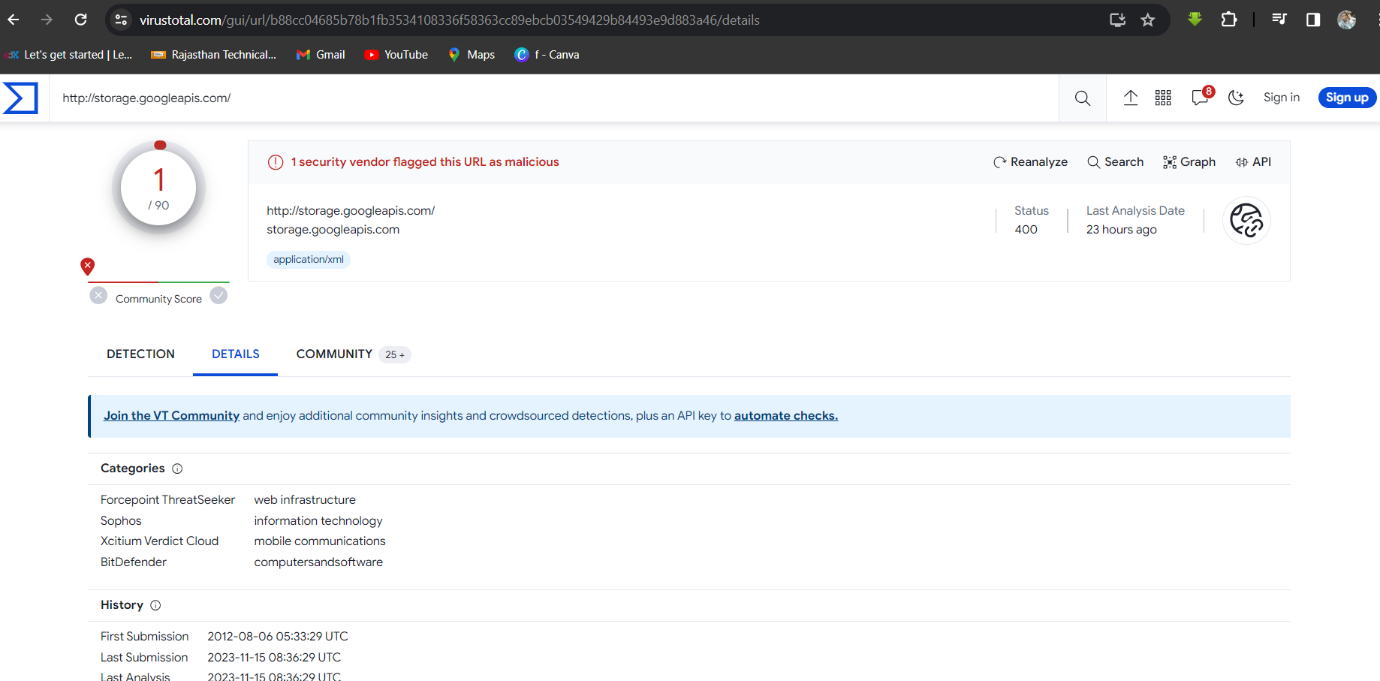
Step 2: Find the Body SHA-256 Tag.
Q5. Is this email a phishing email?
Solution: Yes.
Conclusion
The investigation into the provided email has successfully identified it as a phishing attempt. By examining the email's headers, specifically the return path (bounce@rjttznyzjjzydnillquh.designclub.uk.com), and the domain associated with the embedded link (storage.googleapis.com), we were able to find multiple indicators of compromise.
The domain storage.googleapis.com itself is not inherently malicious, as it's a legitimate Google service. However, threat actors often abuse such services to host malicious content, a common technique known as "living off the land." This makes detection more difficult as the domain appears trustworthy. The VirusTotal analysis of the domain's body SHA-256 (13945ecc33afee74ac7f72e1d5bb73050894356c4bf63d02a1a53e76830567f5) would likely reveal its association with malicious files or activities, further confirming our suspicion.
This case serves as a practical example of how to conduct an initial email analysis using simple tools like a mail client and threat intelligence platforms. It highlights the importance of scrutinizing every element of a suspicious email, from the sender's address to the linked URLs, and how even seemingly benign domains can be part of a larger malicious scheme. The ability to recognize these signs is a crucial skill in cybersecurity for preventing unauthorized access and data breaches.