
CyberDefender: Flare-on 3 Lab Challenge Writeup
Description: Analyze and reverse engineer complex malicious challenges using static and dynamic analysis tools to uncover hidden functionality and extract IOCs.
Level: Insane
Category: Malware Analysis
Link: https://cyberdefenders.org/blueteam-ctf-challenges/flare-on-3/
Tactics: Privilege Escalation, Defense Evasion, Command and Control
Tools: IDA Pro, x64dbg, OllyDbg, FlareVM, WinDbg, CFF Explorer, Hex Workshop, ilspy
Scenario
Instructions:
- Uncompress the lab (
pass: cyberdefenders.org), analyze samples and find the key. Each key looks like an email address and ends with@flare-on.com. - The first challenge is a self-extracting zip file that requires you to accept the EULA before continuing.
- Fire-Eye pleased to announce the conclusion of the third Flare-On challenge. This year they had fantastic participation with a total of 2,063 players!
WARNING!Some of these challenges may be malicious. Exercise extreme caution when executing unknown code. Be safe and perform the analysis inside of a virtual machine.
Questions
Q1. Challenge 1 - challenge1.exe key?
Solution: shooting_phish_in_a_barrel@flare-on.com
Step 1: Open the challenge1.exe file in a disassembler like IDA Pro or IDA Free.
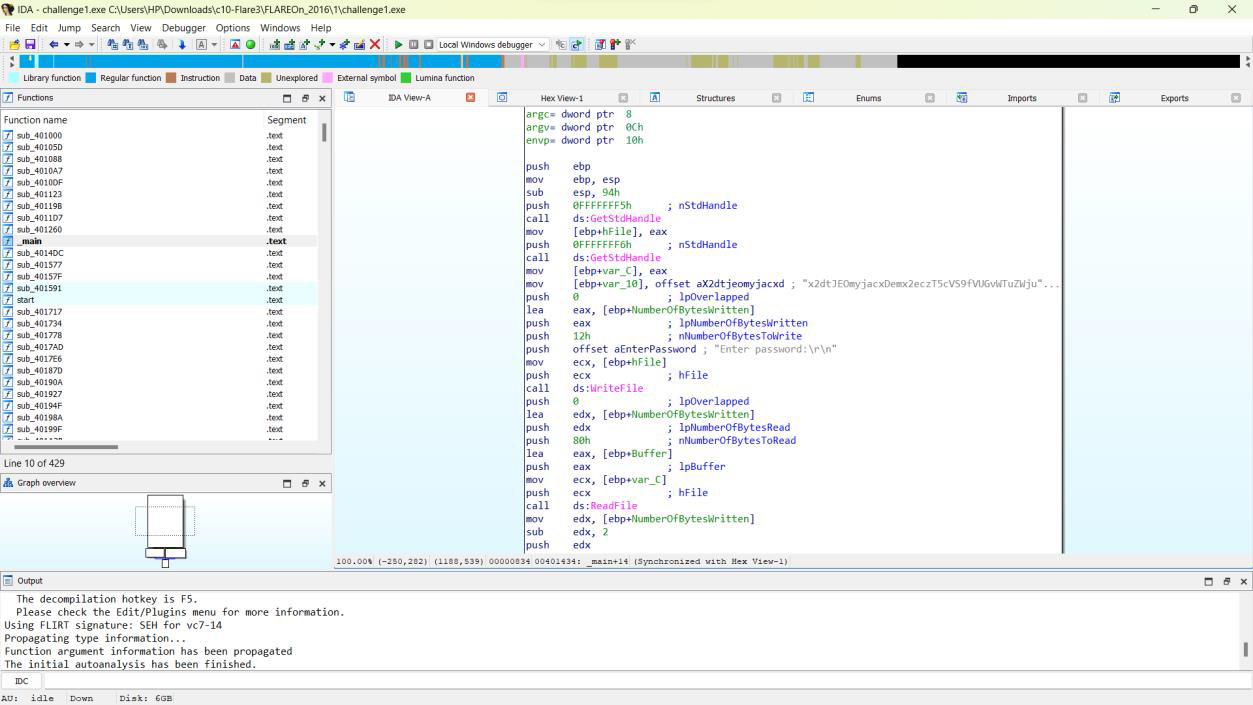
Step 2: Analyze the functions \_main and sub_401260.
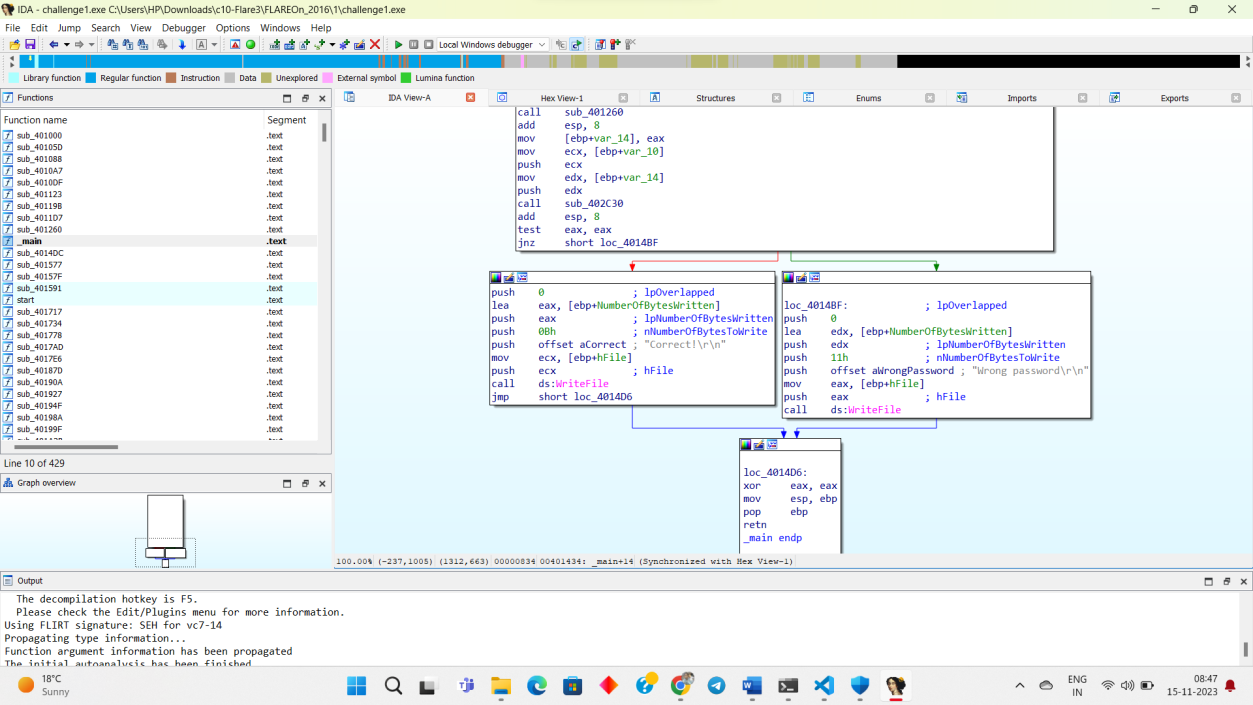
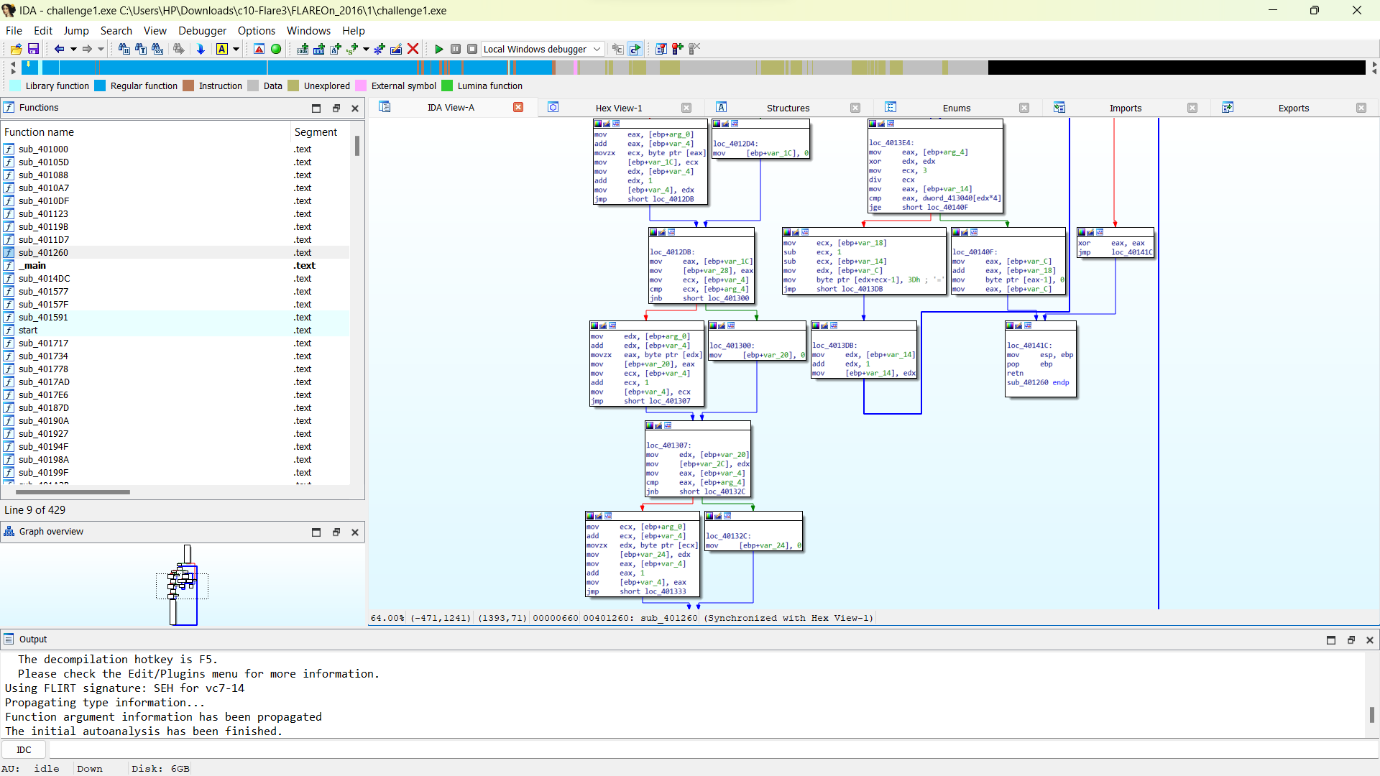
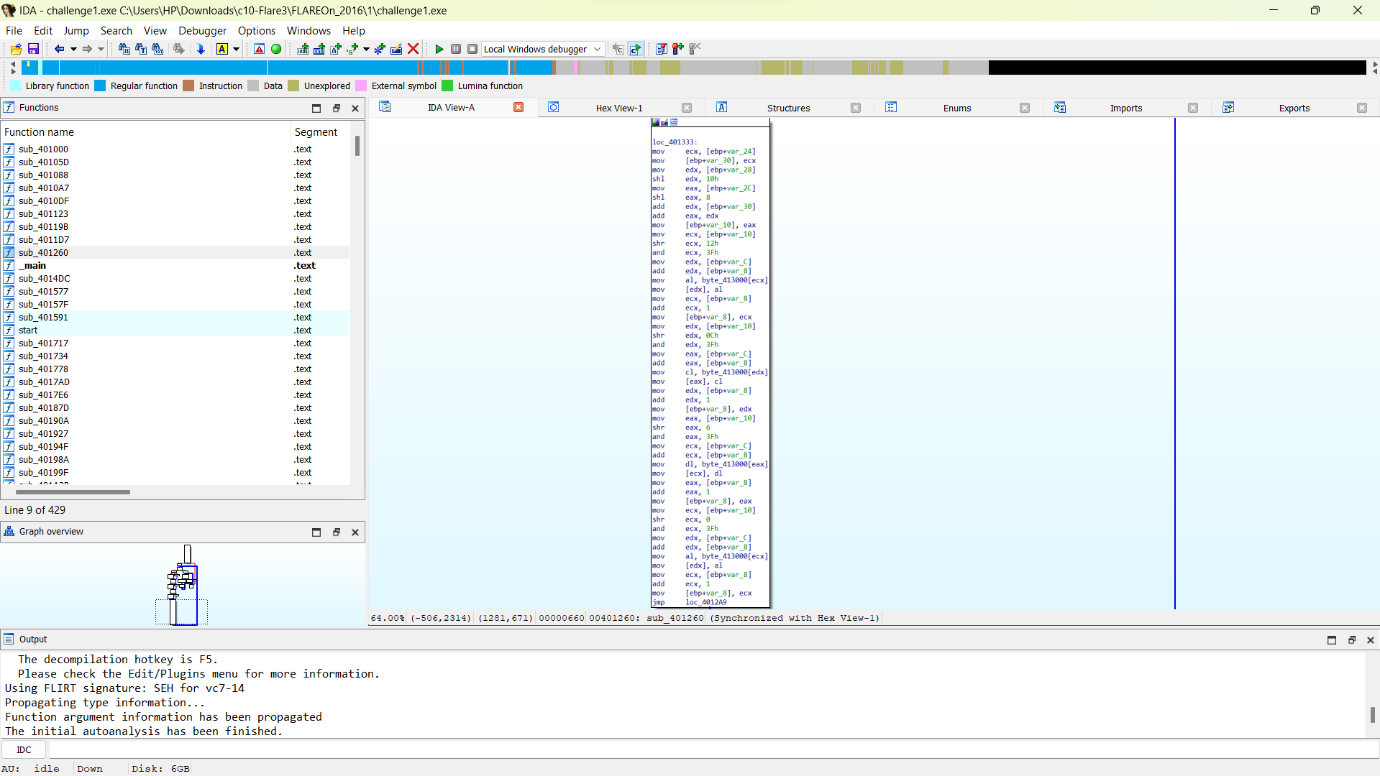
Step 3: Find the base64 encoded string: x2dtJEOmyjacxDemx2eczT5cVS9fVUGvWTuZWjuexjRqy24rV29q.
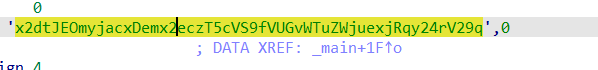
Step 4: Create a Python program to decode the string.
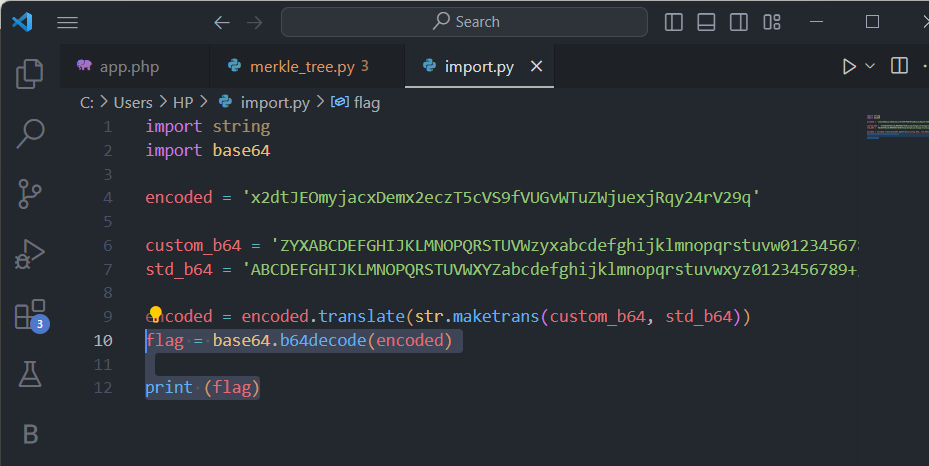
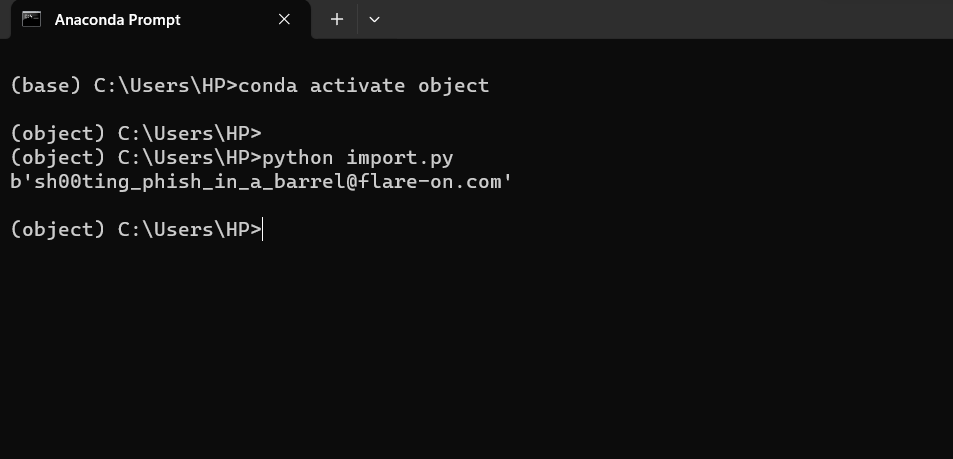
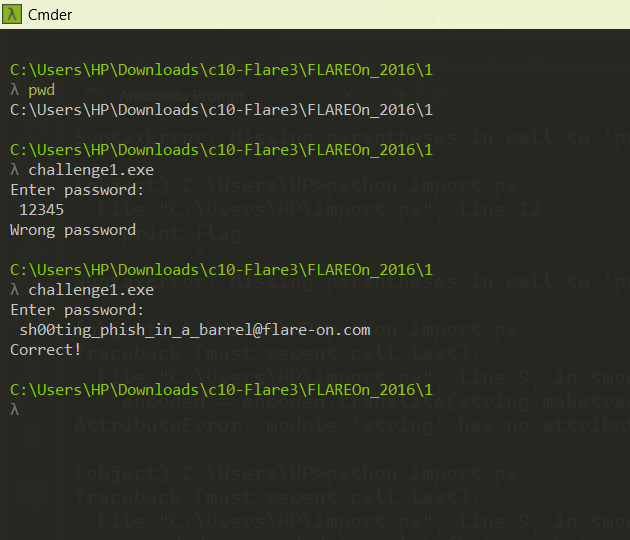
Step 5: Test the decoded string shooting_phish_in_a_barrel@flare-on.com as the password, which is successful.
Q2. Challenge 2 - DudeLocker.exe key?
Solution: close_t3h_file_On_th1s_One@flare-on.com
Step 1: Check for a Briefcasedirectory at %USER%\Desktop.
Step 2: The program checks if the disk serial number is 0x7DAB1D35 by calling GetVolumeInformationA.
Step 3: A set of AES-256 keys is generated with fixed content sha1("thosefilesreallytiedthefoldertogether").
Step 4: All files in the Briefcase directory are encrypted using AES-256.
Step 5: The wallpaper is changed to ve_vant_ze_money.jpg to inform the user of the RSA-4096 encryption.

Step 6: The solution is to patch the binary to replace CryptEncrypt with CryptDecrypt and modify the return value of GetVolumeInformationA to 0x7DAB1D35. The key is then revealed as
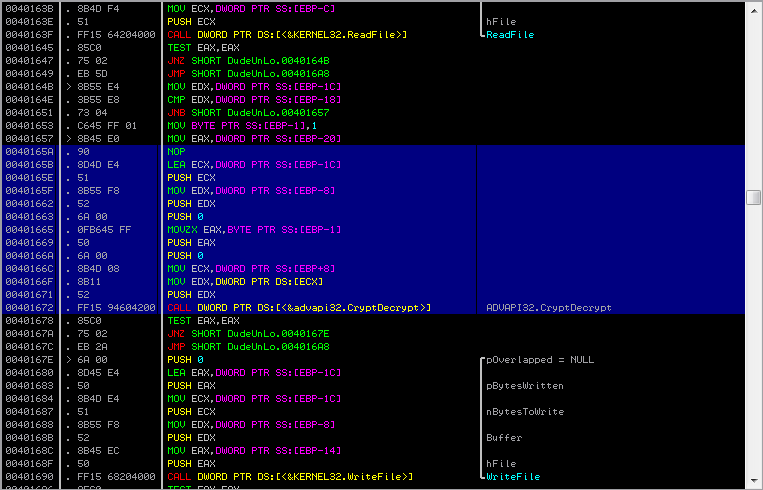

close_t3h_file_On_th1s_One@flare-on.com.
Q3. Challenge 3 - unknown key?
Solution: Ohs0pec1alpwd@flare-on.com
Step 1: Opening the file in IDA provides a clue about the symbol filename C:\extraspecial.pdb.
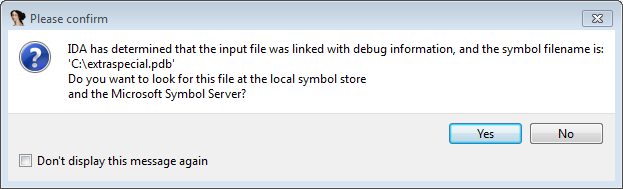
Step 2: Analyze the file in the IDA debugger.
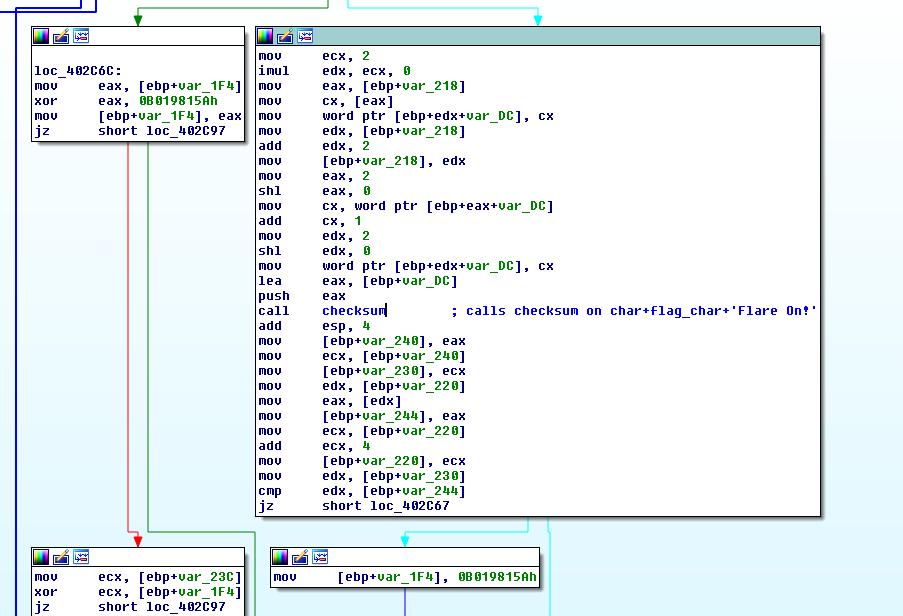
Step 3: Create a Python script to decrypt the hex code.
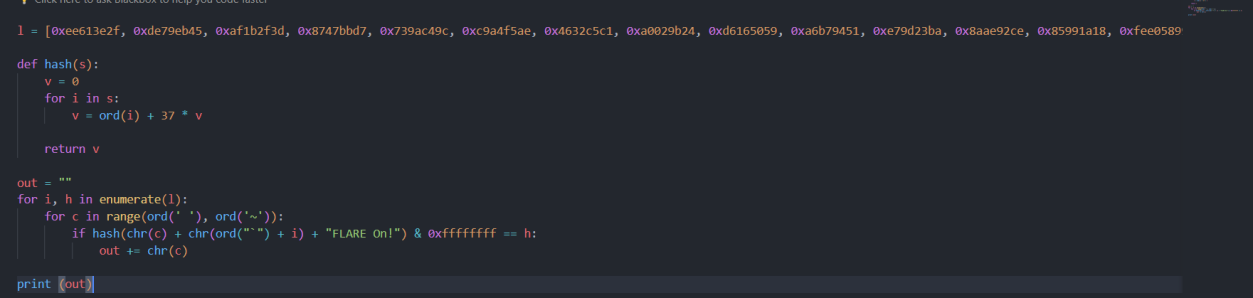
Step 4: Run the script import2.py to generate the key, which is Ohs0pec1alpwd@flare-on.com.
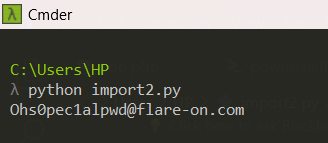
Q4. Challenge 4 - flareon2016challenge.dll key?
Solution: follow_t3h_3xp0rts@flare-on.com
Step 1: Open the file flareon2016challenge.dll in an IDA debugger.
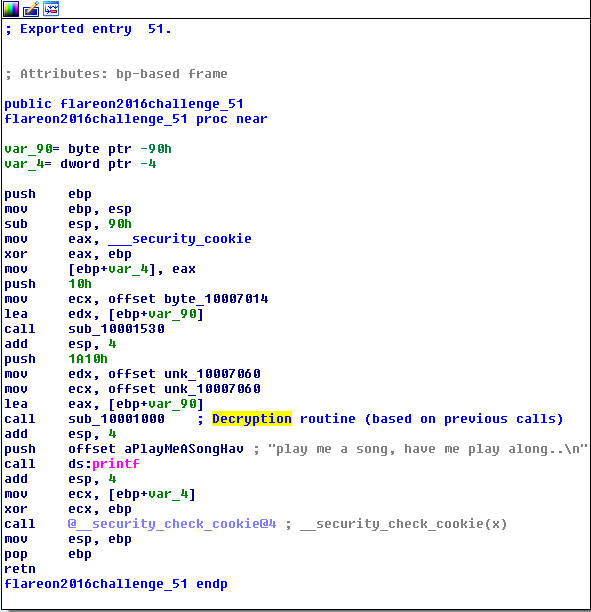
Step 2: Analyze the file in the IDA debugger.
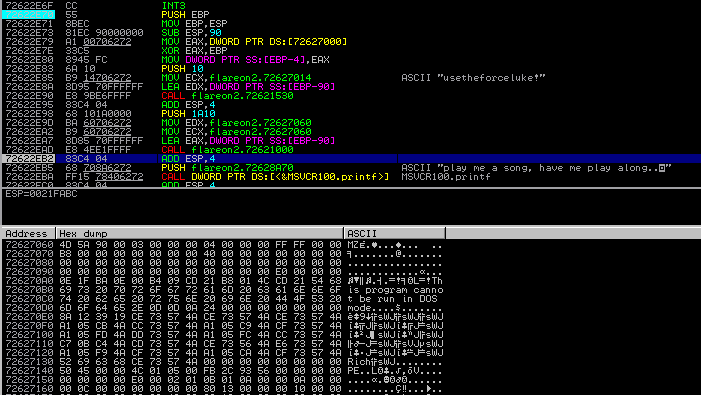
Step 3: After dumping the executable from memory, a secret melody that provides parameters for the export is found.
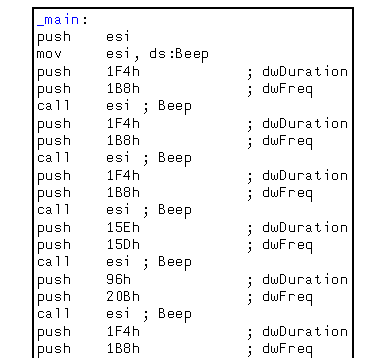
Step 4: Create a Python script that decrypts the hex codes.
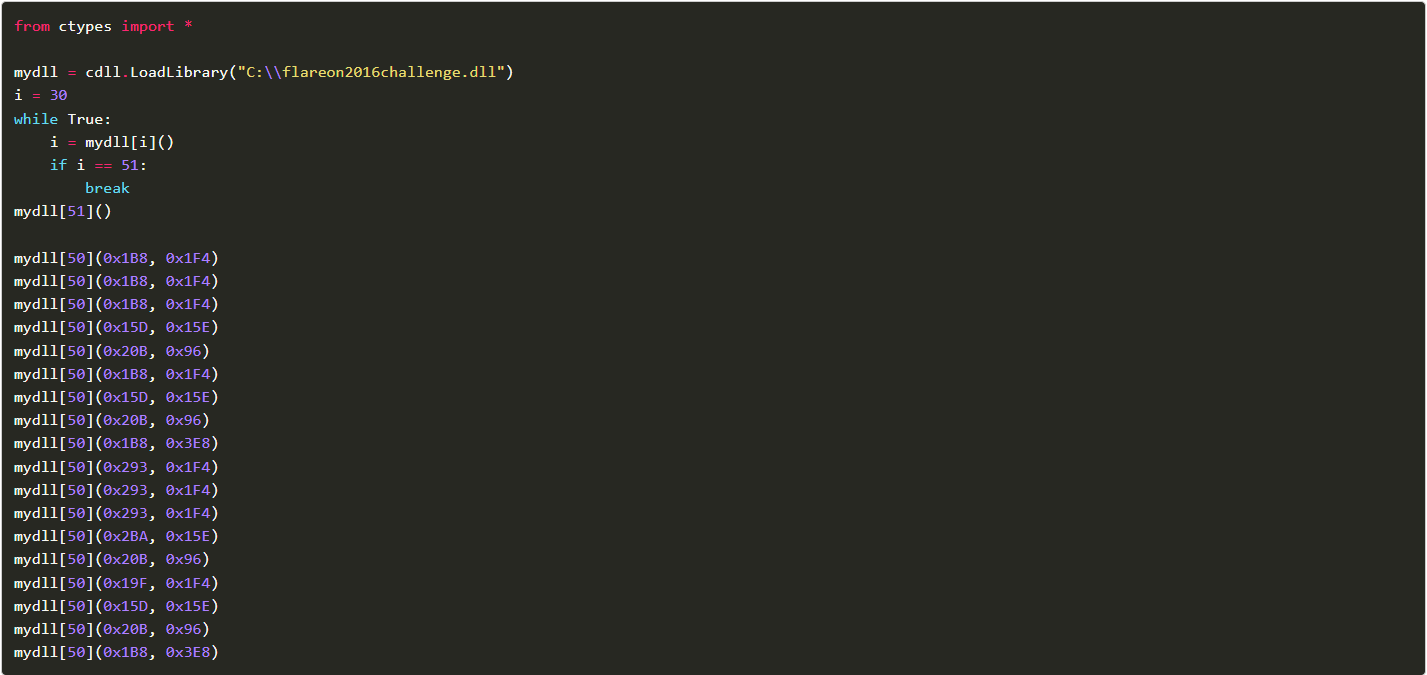
Step 5: Run the Python file ch4.py to generate the key, which is follow_t3h_3xperts@flare-on.com.
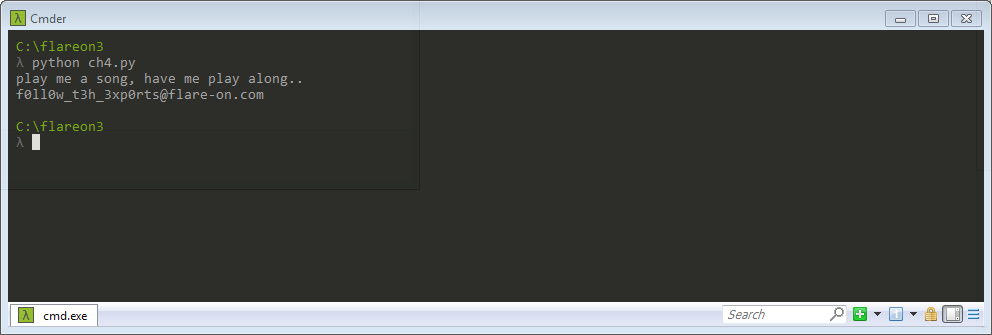
Q5. Challenge 5 - smokestack.exe key?
Solution: A*pop_pu$H*&_a_Jmp@flare-on.com
Step 1: Open smokestack.exe in the IDA debugger and analyze the code.
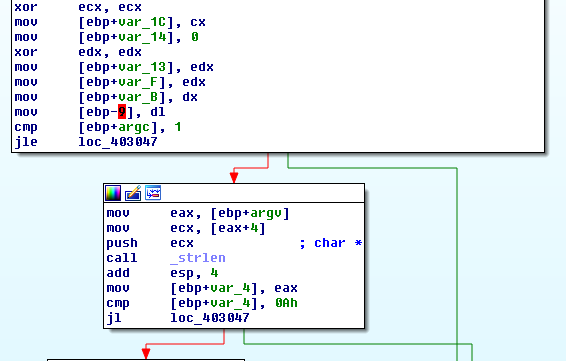
Step 2: Analyze the function sub_401610.
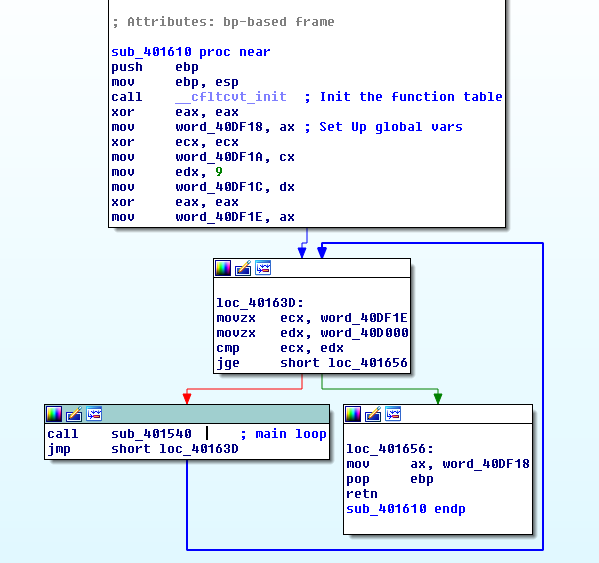
Step 3: The program calls sub_401540 inside a loop, which uses an index of functions to perform operations.
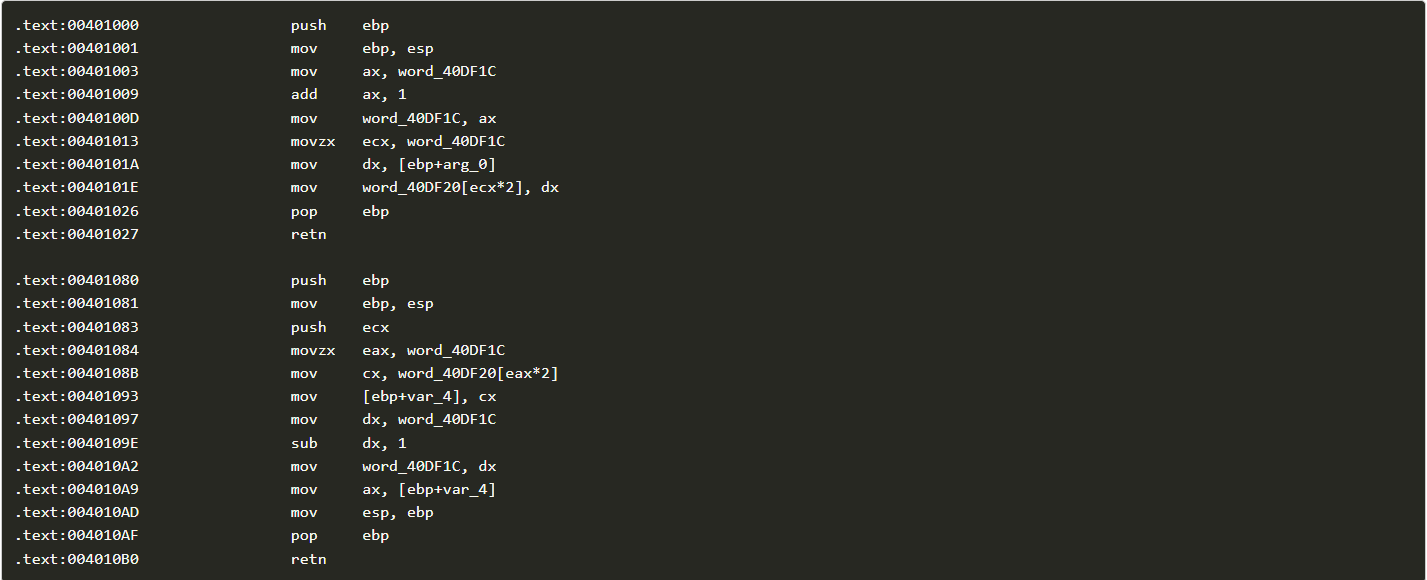
Step 4: A Python script bruteforce.py is used to bruteforce the key and Result of running bruteforce.py.
File Link:https://github.com/kiinji/FLARE-On-2016/tree/master/challenge_5
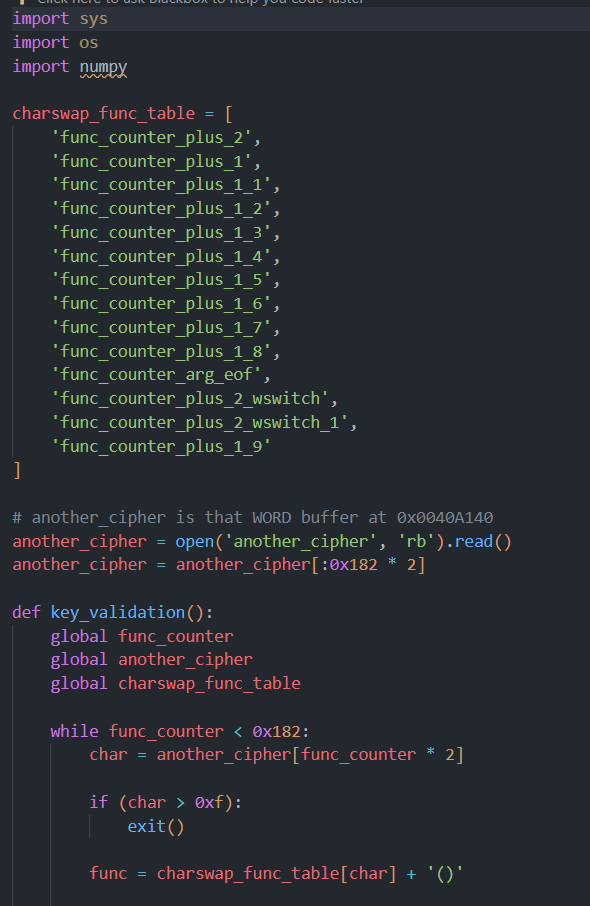
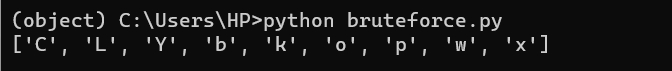
Step 5: A second Python script is created to find the key by iterating through characters.
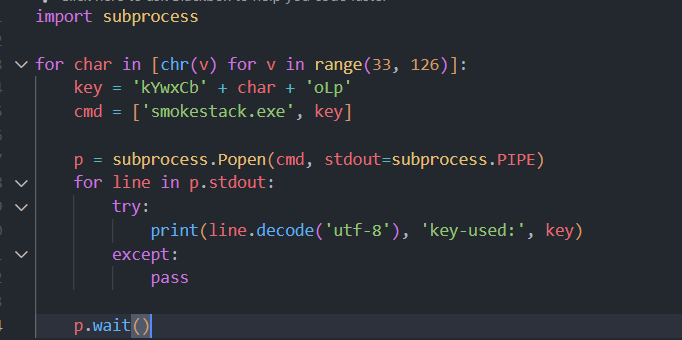
Step 6: Running the Python script generates the key.
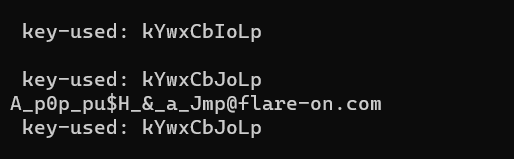
Step 7: The key is then tested on the executable, and it works.
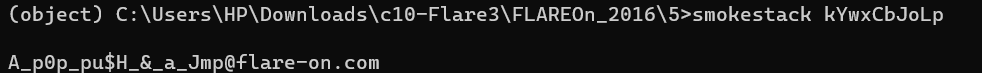
Q6. Challenge 6 - khaki.exe key?
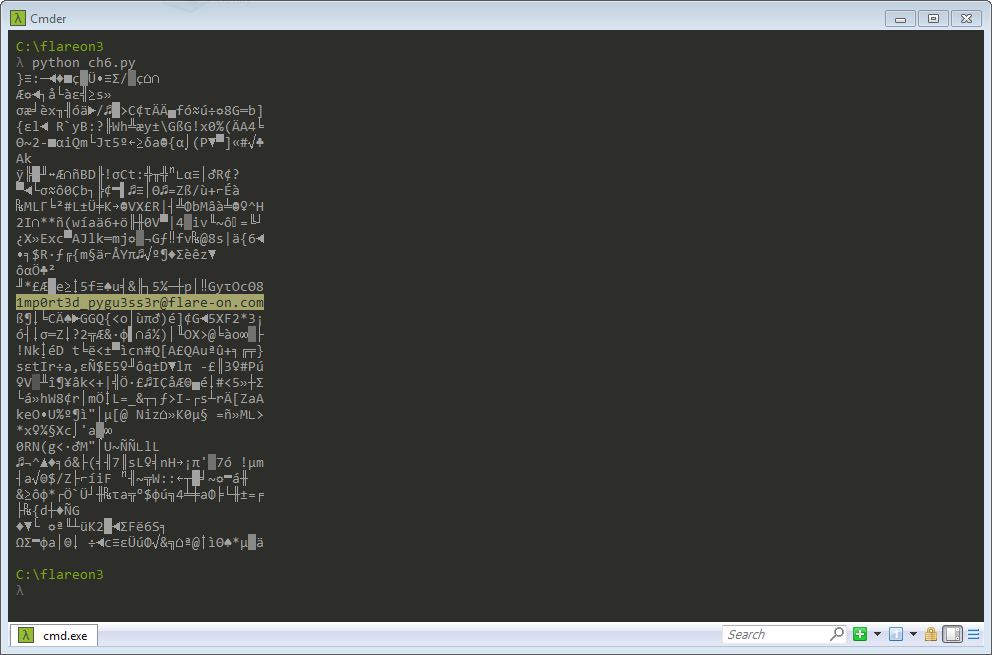
Solution: 1mp0rt3d_pygu3ss3r@flare-on.com
Step 1: Run the khaki.exe file.
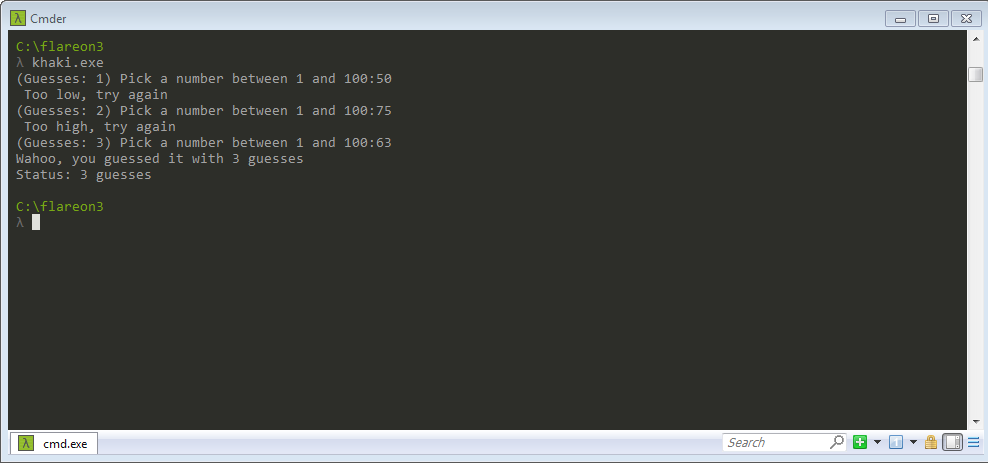
Step 2: Open the file in the IDA debugger.
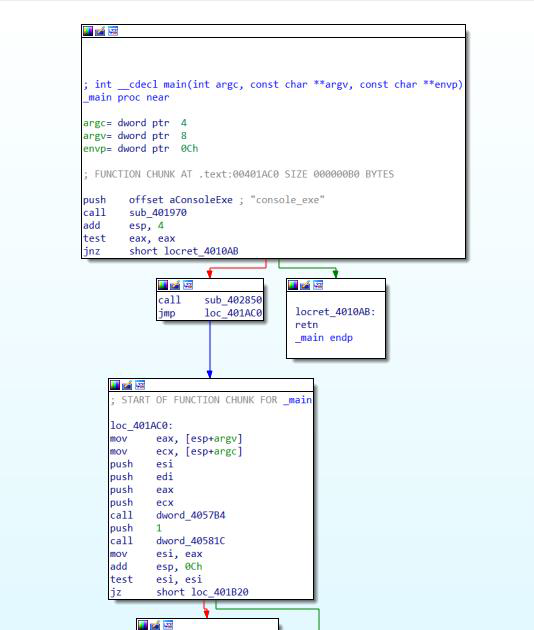
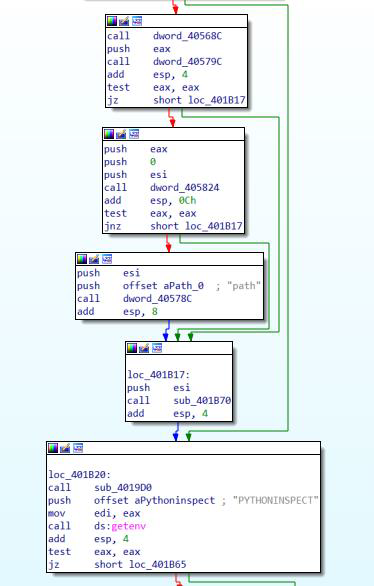
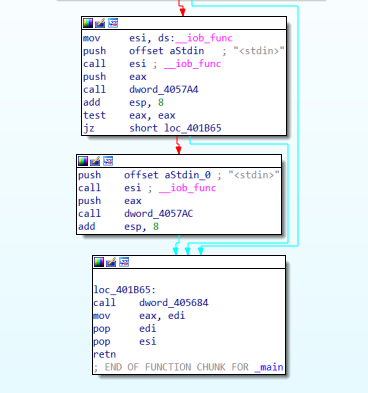
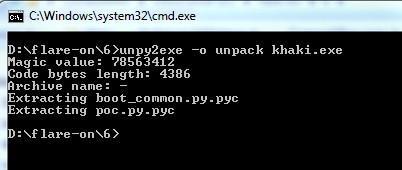
Step 3: The file is unpacked using the unpy2exe tool.
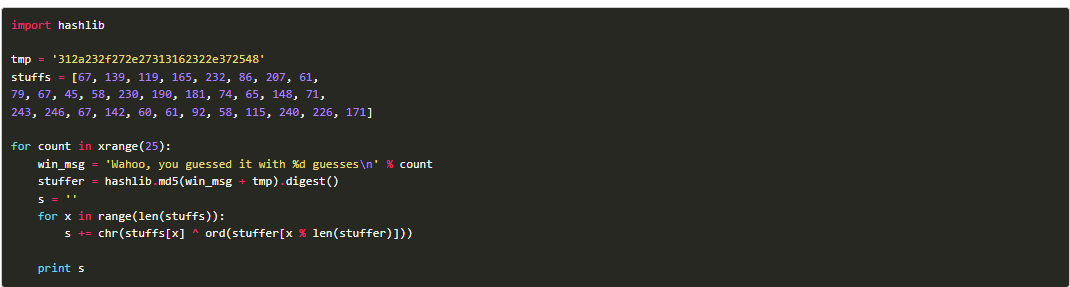
Step 4: Run a Python program file.
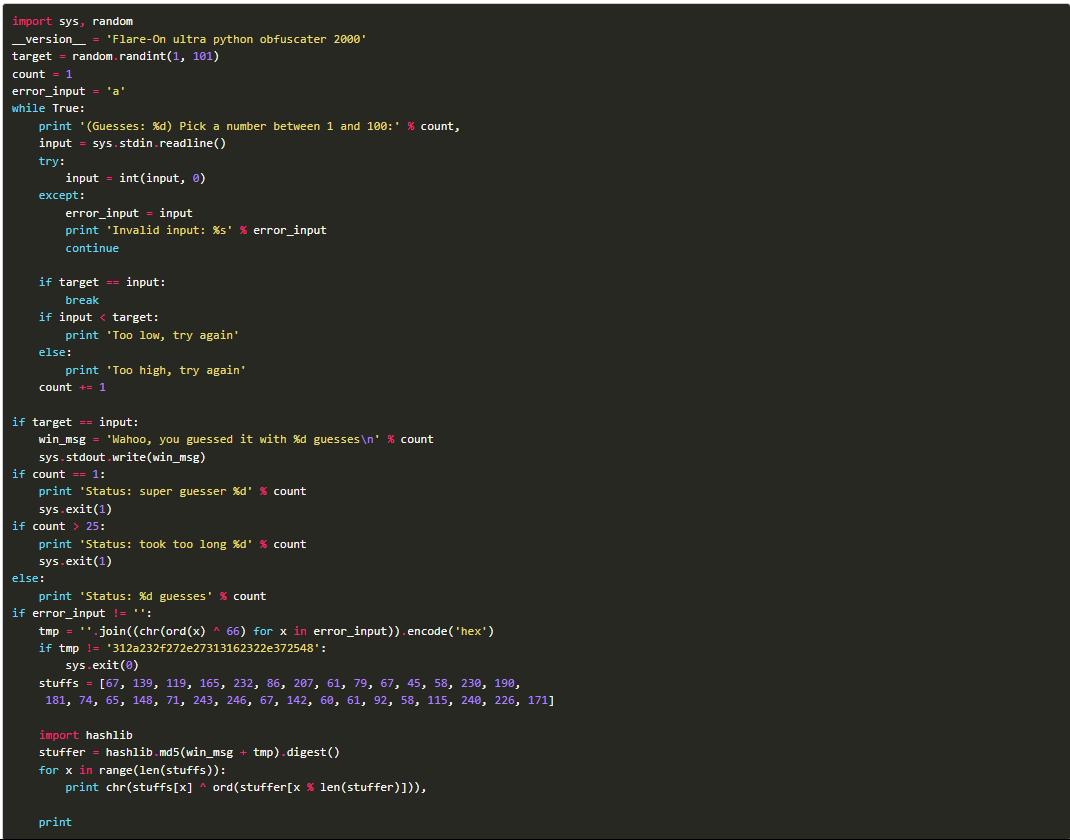
Step 5: Run another Python program that provides the key.
Q7. Challenge 7 - hashes.exe key?
Solution: h4sh3d_th3_h4sh3s@flare-on.com
Step 1: Open the hashes.exe file in the IDA debugger.
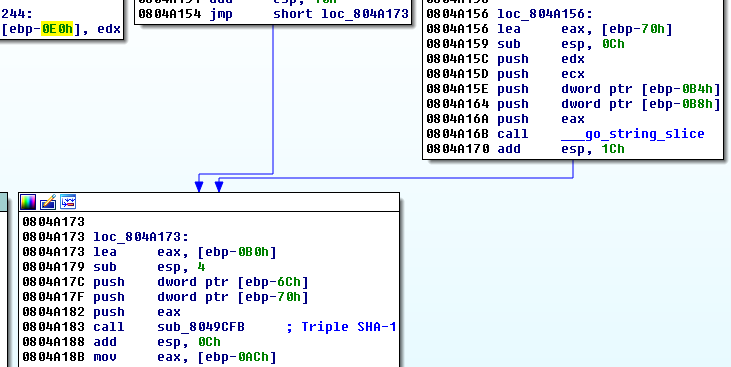
Step 2: Analyze the file in IDA.
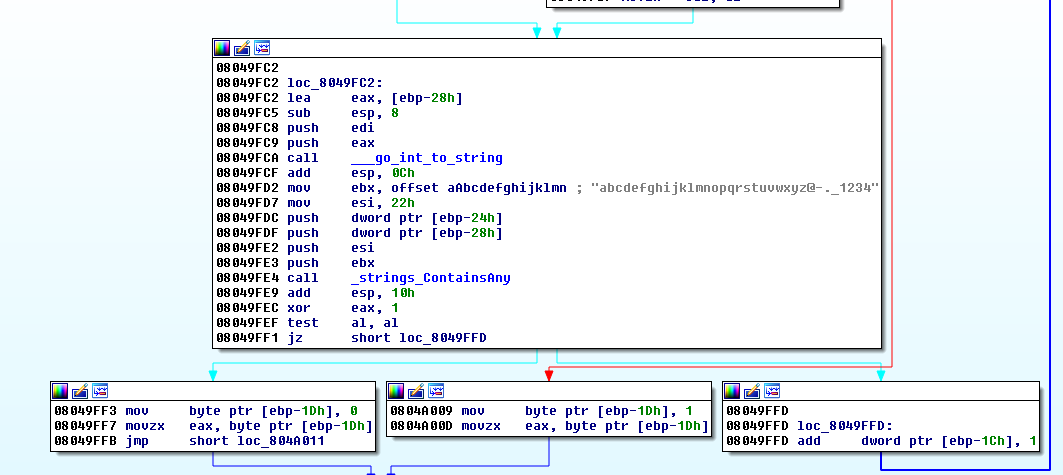
Step 3: Create a Python program that combines all the cracked pieces to find the key.
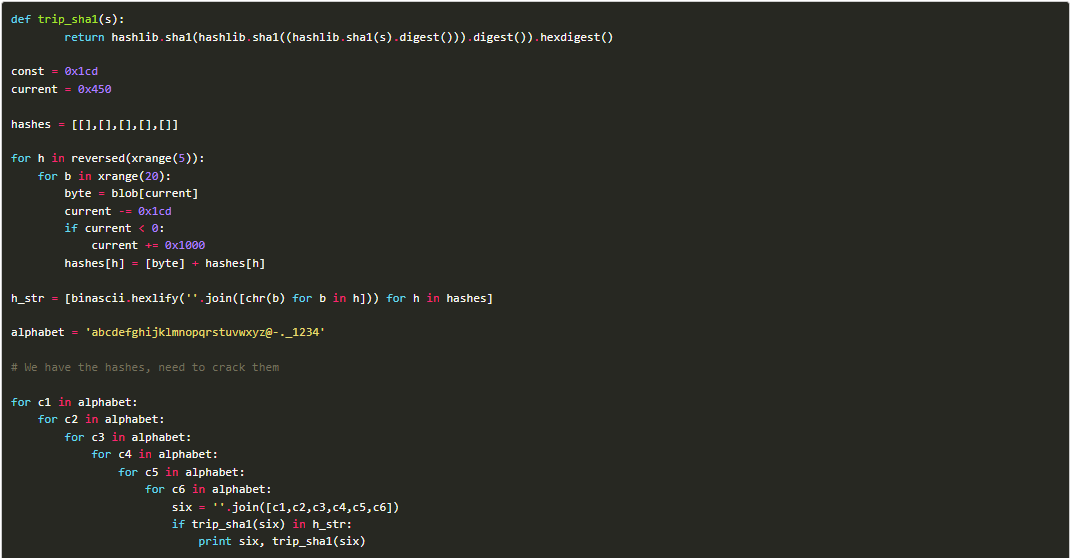
Q8. Challenge 8 - CHIMERA.EXE key?
Solution: retr0_hack1ng@flare-on.com
Step 1: Open the CHIMERA.EXE file in the IDA debugger and analyze it.
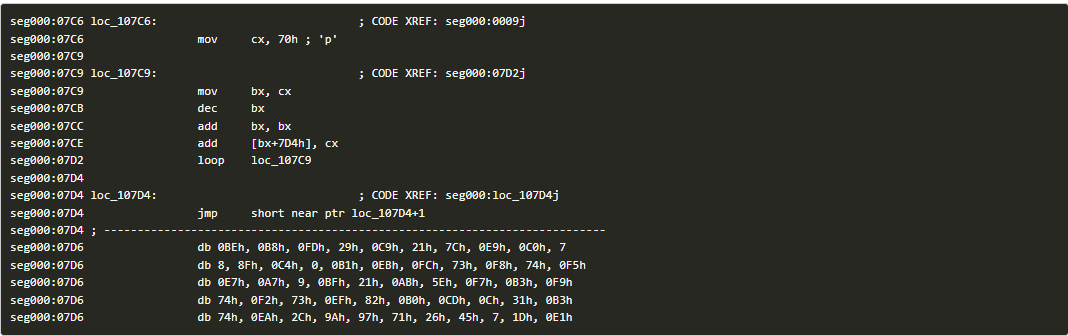
Step 2: A Python script is used to replicate the decryption routine.

Step 3: The decrypted code shows up in IDA.
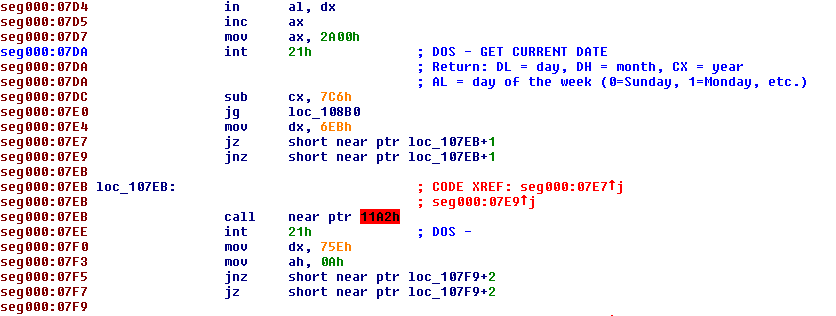
Step 4: The instructions are redefined as code in IDA to fix the jumps.
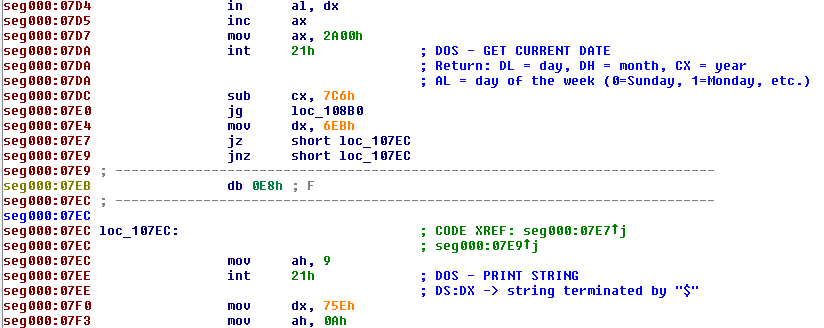
Step 5: A DOSBox debugger is used to validate the findings.
Step 6: A Python script reverses the encoding to find the flag.
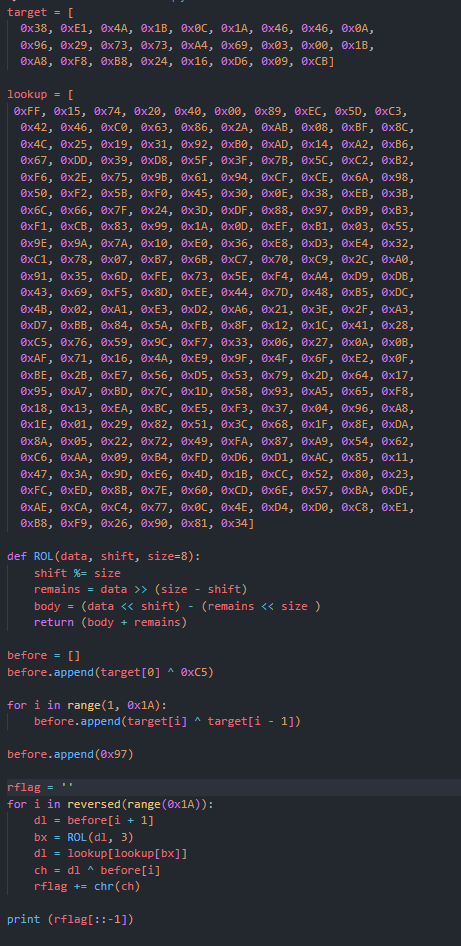
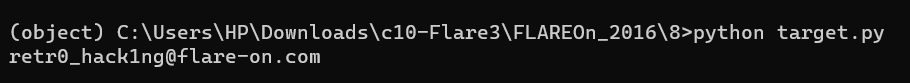
Step 7: Running the Python script target.py gives the key retro_hacking@flare-on.com.
Q9. Challenge 9 - GUI.exe key?
Solution: Shamir_1s_Confused@flare-on.com
Step 1: Open the GUI.exe file.
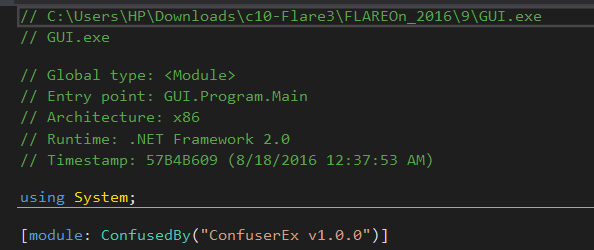
Step 2: The file is opened in dnSpy and found to be obfuscated with ConfuserEx 1.0.
Step 3: The button click handler function is analyzed.
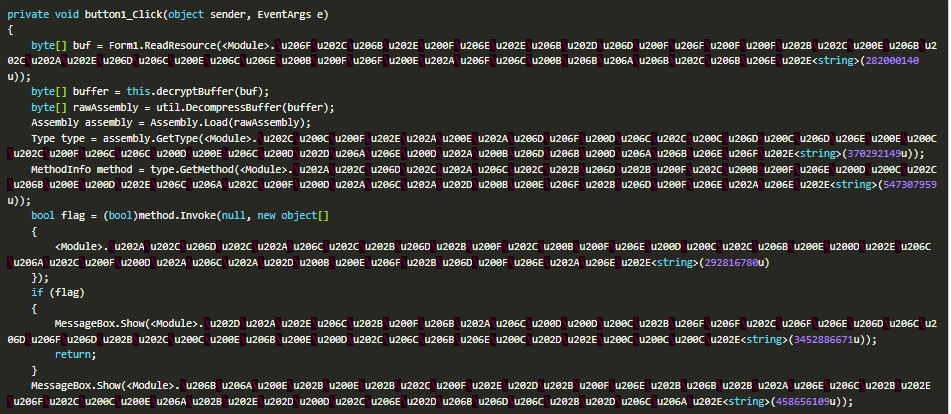
Step 4: The deDot tool is used to deobfuscate the code.
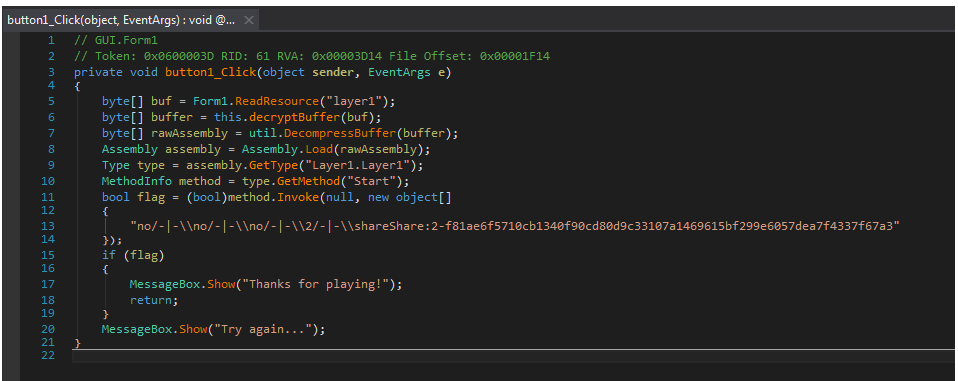
Step 5: The program dynamically decrypts and loads Layer1.dll, and its code is dumped and deobfuscated.
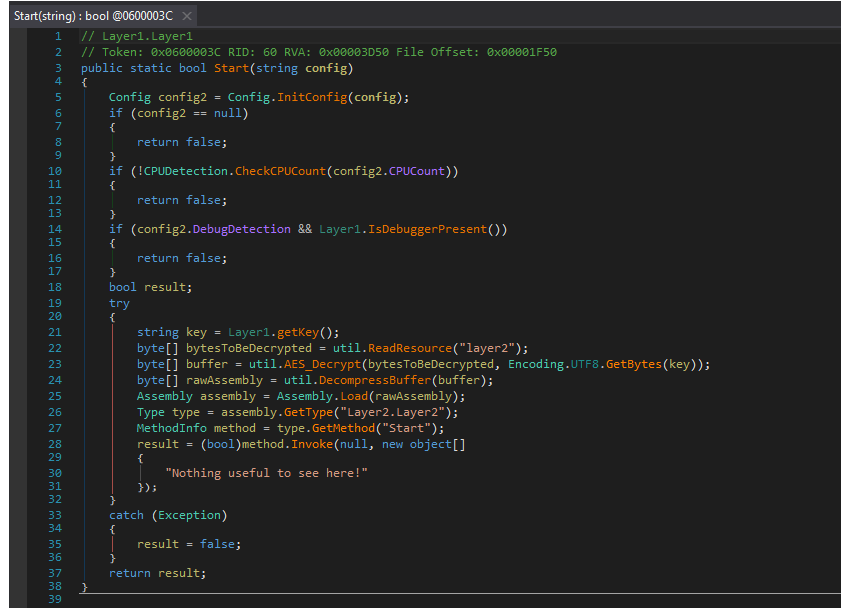
Step 6: Now, the programs decrypts and loads Layer2.dll. Similarly, Layer2 checks for VM usage with a WMI query select \* from win32_videocontroller.
Step 7: The getKey function looks for a registry key secret under HKEY_CURRENT_USER.After creating the key in the registry, we proceed to Layer3.
Step 8: The third layer checks for the existence of the user shamir.

Step 9: The flag is found by combining 6 shares using ssss-combine.exe, with the shares dumped from memory and the 6th share from a decoded PNG.
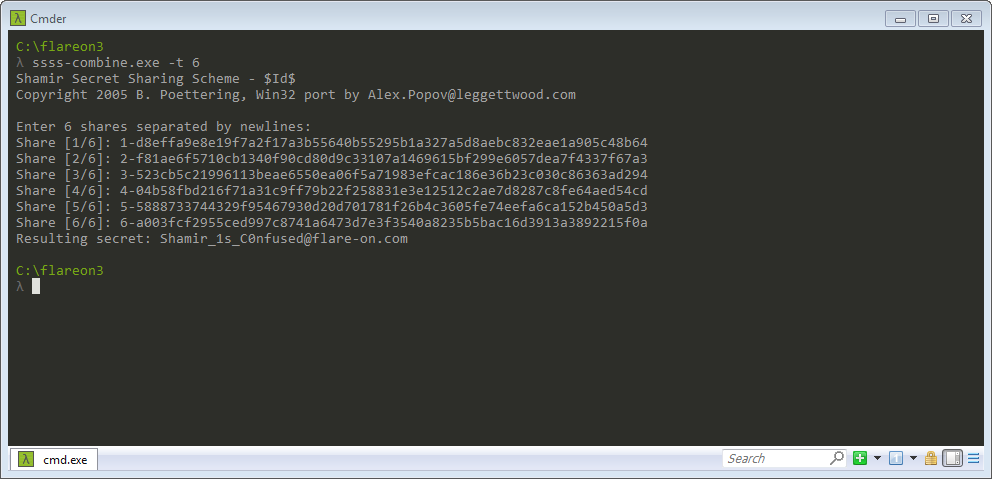
Q10. Challenge 10 - flava.pcap key?
Solution: angl3rcan7ev3nprim3@flare-on.com
Step 1: Open flava.pcap in Wireshark and filter for tcp.stream == 233. It contains obfuscated JavaScript.
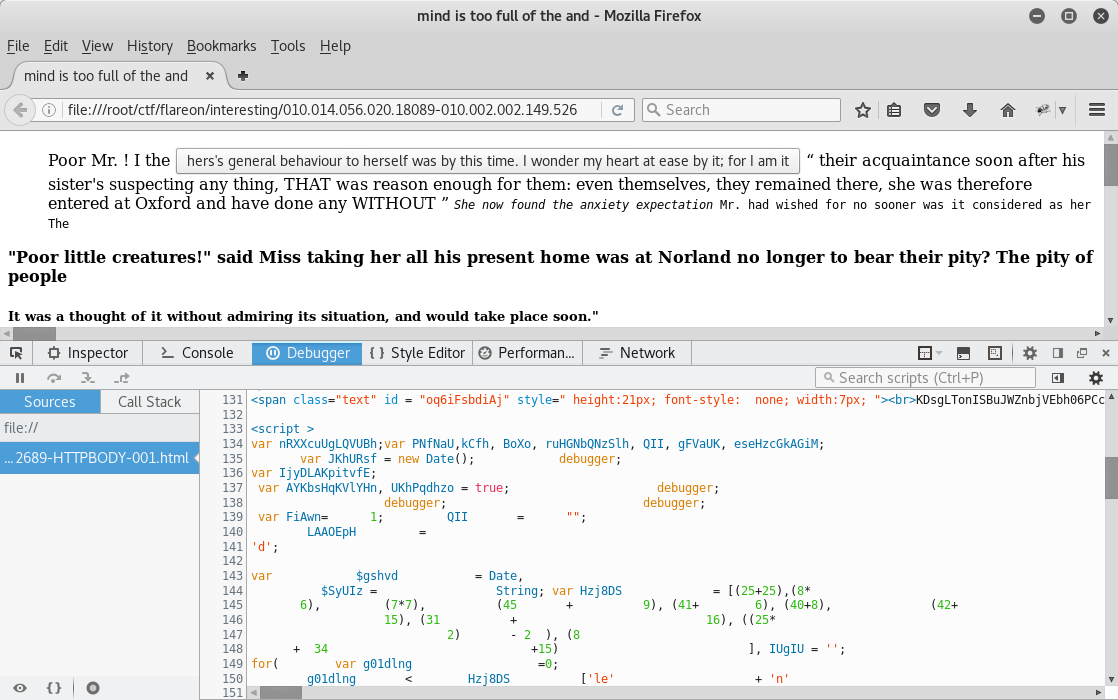
Step 2: The code is inside a try/catch block, which suppresses faulty decoding.

Step 3: After fixing the checks, the second layer is decoded.
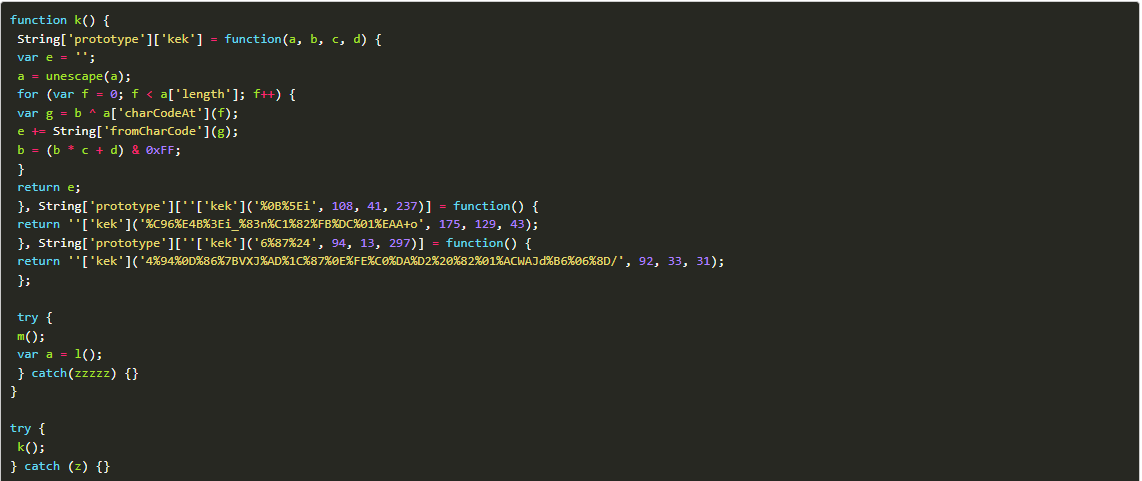
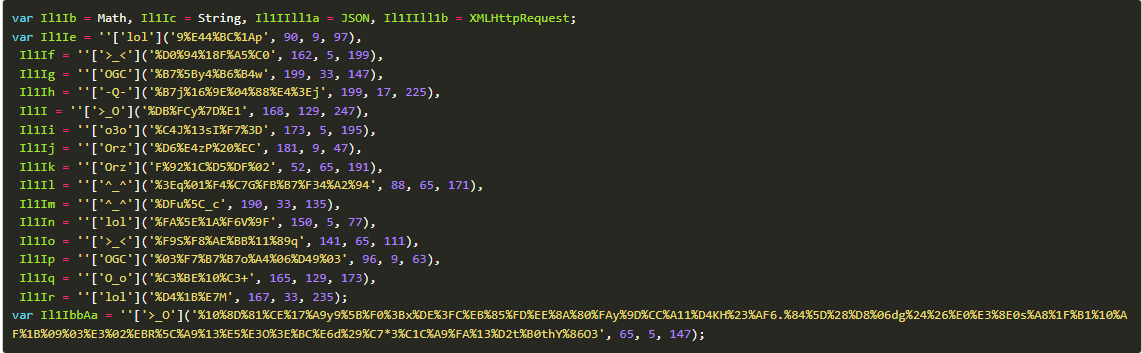
Step 4: After bypassing checks for Kaspersky, the third layer is decoded.
Step 5: A function sends an HTTP POST request that is RC4 encrypted with the key flareon_is_so_cute and base64 encoded.
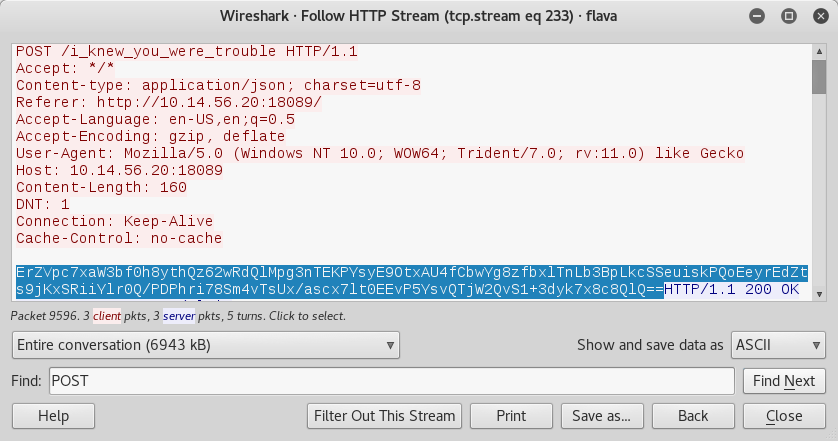
Step 6: A Python script is used to reverse the RC4 encryption and decode the dictionary value.
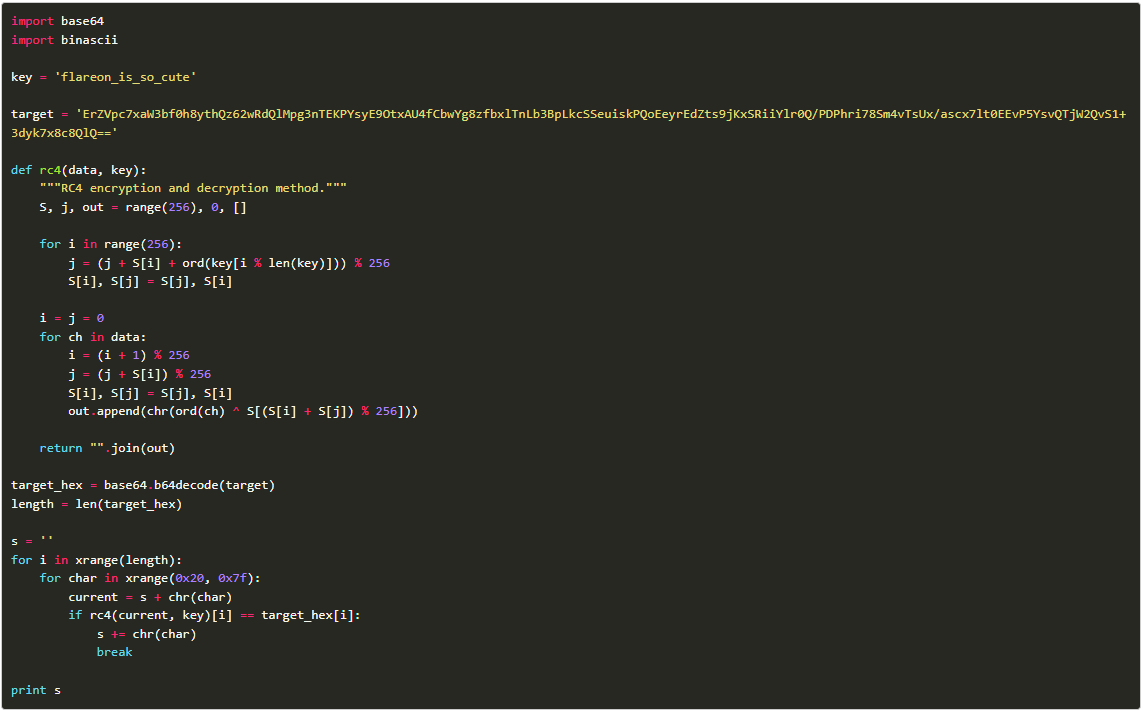
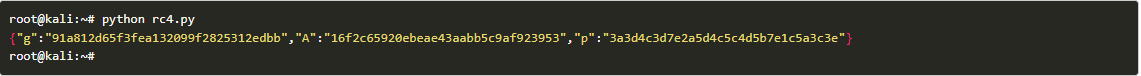
Step 7: Plugging in our values into the program then we get.

Step 8: The key is used to decode the received payload.
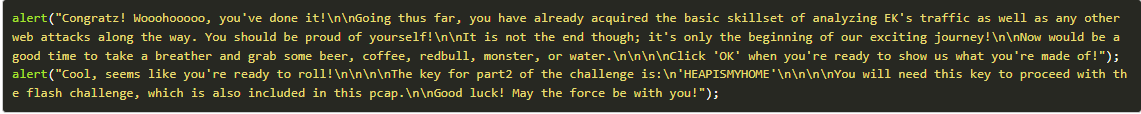
Step 9: The flash file is extracted from the pcap, and after decompiling, a loader function is found.
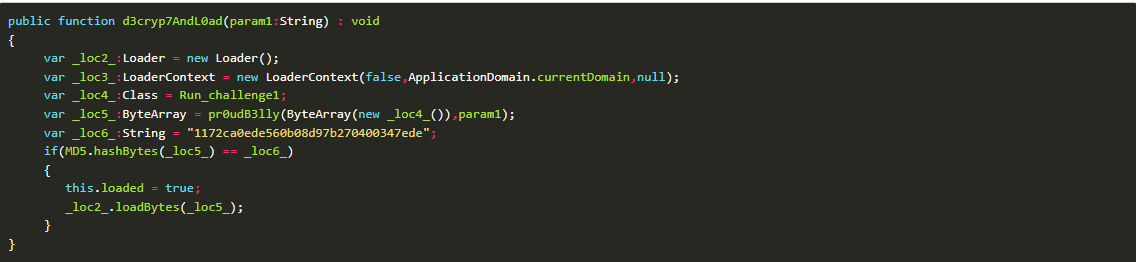
Step 10: The loaded flash file is dumped and deobfuscated.
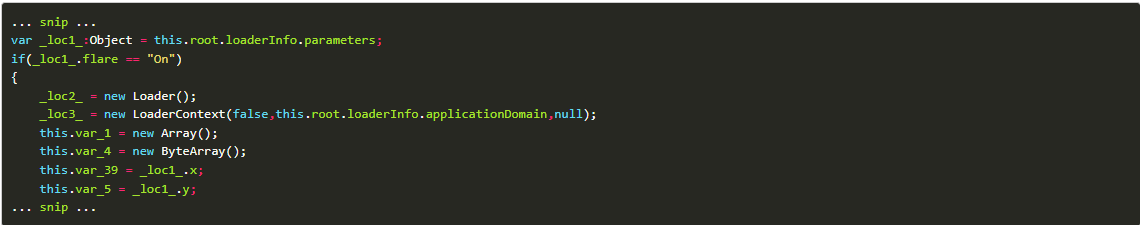
Step 11: The code references an image at http://imgur.com/vnUziJP.
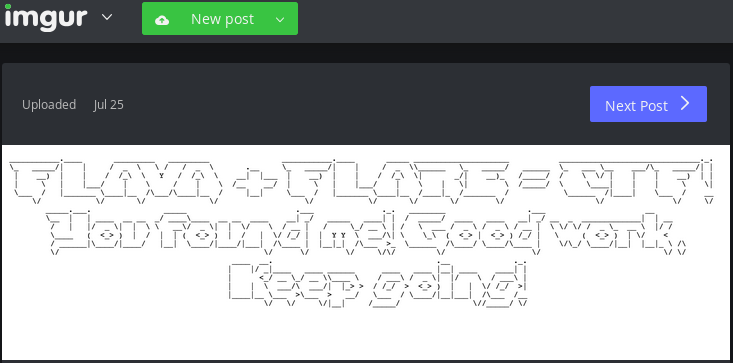
Step 12: There are two encrypted blobs of data and an image that is the decryption of one of them. By XOR-ing them, the flag can be found.
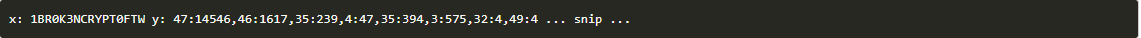
Step 13: A Python script can decode the flag character by character from the trace.Combining all the arg 0 values, we get the flag.

Conclusion
The solutions to the Flare-on 3 Blue Team Challenge showcase a comprehensive range of reverse engineering and malware analysis techniques. Each challenge required a different approach, from static analysis and debugging to network forensics and deobfuscation.
Key Takeaways
Diverse Skillset: The challenge required a diverse skillset, including proficiency with tools like IDA Pro, Wireshark, dnSpy, and various scripting languages (primarily Python). This highlights the need for a multi-faceted approach to dealing with sophisticated malware.
Obfuscation and Anti-Analysis Techniques: The challenges progressively introduced more advanced techniques, such as Base64 encoding (Challenge 1), anti-debugging and anti-virtual machine checks (Challenge 2, Challenge 10), and code obfuscation (Challenge 9). Analysts must be prepared to bypass these mechanisms to uncover the true functionality of the malware.
Layered Payloads: Several challenges, notably Challenge 9 and 10, involved a multi-stage payload delivery. The initial file was a loader that decrypted and executed subsequent stages, often involving dynamic loading of DLLs, encrypted blobs, or remote files. This is a common tactic used by modern malware to evade detection.
Importance of Context: The solutions often relied on clues from the environment (e.g., registry keys, disk serial numbers, external URLs), which highlights the importance of analyzing malware in a controlled, instrumented environment that can simulate these conditions.
Scripting for Automation: The recurring use of Python scripts in the solutions for tasks like decoding, decryption, and brute-forcing demonstrates the necessity of automation in malware analysis. Manual analysis alone would be too time-consuming for these complex challenges.
Network Traffic as a Source of Information: Challenge 10 specifically showcased how network forensics can be an integral part of malware analysis. The pcap file contained not only the malware payload but also critical information about its communication and decryption keys.
In conclusion, the Flare-on 3 challenges were designed to test an analyst's ability to navigate and overcome a wide variety of security obstacles. The solutions provide an excellent reference for common reverse engineering methodologies, underscoring that a combination of static analysis, dynamic analysis, and creative problem-solving is essential for success in malware analysis.